System Weakness
@SystemWeakness
Followers
381
Following
0
Media
0
Statuses
4K
🖥️ We cover cybersecurity, ethical hacking, and everything in between.
Joined January 2022
Post Exploitation with PowerShell and Alternatives: What Happens After You’re In #systemweakness #cybersecurity #ethicalhacking.
systemweakness.com
So, you’ve just pwned a system. You’ve bypassed the firewall, landed a shell, or executed your payload — now what?
0
0
0
Website & API Security Boost with SafeLine Web Application Firewall #systemweakness #cybersecurity #ethicalhacking.
systemweakness.com
Websites and APIs are not only business-critical — they’re also constant targets for cyberattacks. From SQL injections to bot abuse and…
0
0
0
iDocView RCE Vulnerability: How a Simple URL Leads to Remote Code Execution #systemweakness #cybersecurity #ethicalhacking.
systemweakness.com
> About Author Hi, I’m Sharon, a product manager at Chaitin Tech. We build SafeLine, an open-source Web Application Firewall built for…
0
0
0
How an API Token Flaw Let Me Bypass Premium Restrictions #systemweakness #cybersecurity #ethicalhacking.
systemweakness.com
Hi Guys, Welcome back to yet another article, Today, I want to walk you through one of the bugs I found while hunting on HackerOne. I was…
0
0
0
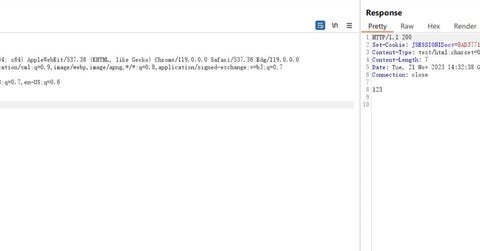
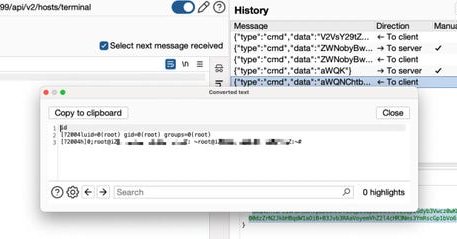
PortSwigger Lab Walkthrough: Blind OS Command Injection with Time Delays #systemweakness #cybersecurity #ethicalhacking.
systemweakness.com
When it comes to exploiting web applications, nothing is more thrilling than turning a simple form input into a foothold on the server.
0
0
0
Do you Practice, but Still Feel Stuck at Bug Bounty? #systemweakness #cybersecurity #ethicalhacking.
systemweakness.com
Browsing Reddit recently, I found a lot of hunters who faced a common problem… They studied the theory, did CTFs, and spent time doing Bug…
0
0
0
[CVE-2025–54424] Critical RCE Vulnerability in 1Panel Pro — Patch Now! #systemweakness #cybersecurity #ethicalhacking.
systemweakness.com
> About Author Hi, I’m Sharon, a product manager at Chaitin Tech. We build SafeLine, an open-source Web Application Firewall built for…
0
0
0
How the Tea App Exposed 72,000 IDs and 1.1 Million DMs: A Security Breakdown #systemweakness #cybersecurity #ethicalhacking.
systemweakness.com
When a women-first safety app becomes a data nightmare — anatomy of the Tea app breach and how poor design fuelled a massive privacy…
0
0
0
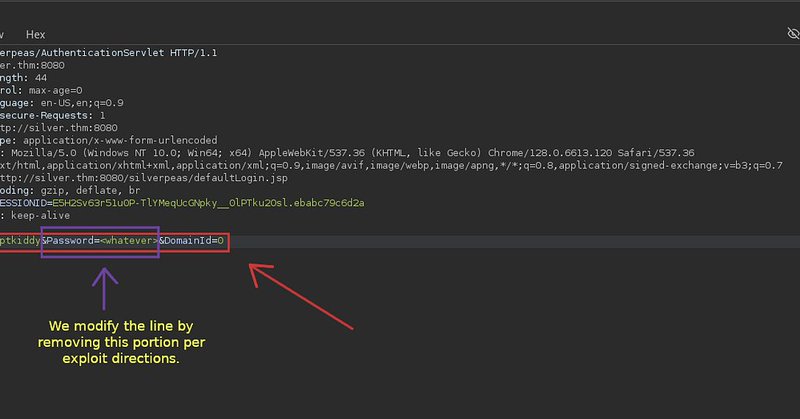
“Juicy 404s”: How Broken Pages Spilled Secrets and Gave Me Admin Access #systemweakness #cybersecurity #ethicalhacking.
systemweakness.com
💬 “Everyone chases 200 OK. I chase the errors — that’s where the gold leaks.”
0
0
0
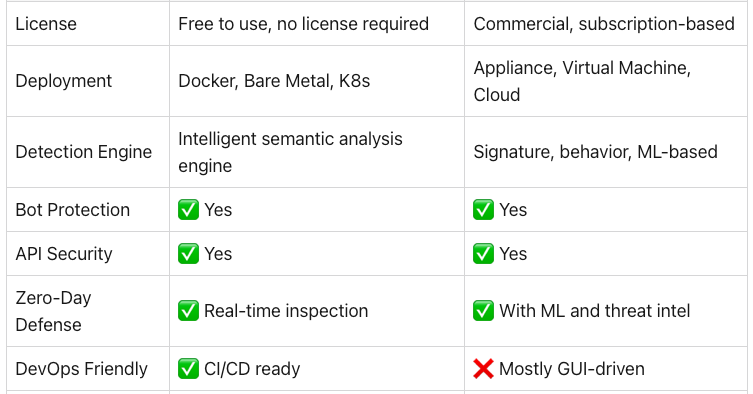
SafeLine vs. FortiWeb: Which WAF Fits Your Architecture? #systemweakness #cybersecurity #ethicalhacking.
systemweakness.com
Web Application Firewalls (WAFs) are critical for protecting modern web applications from evolving threats. FortiWeb is widely recognized…
0
0
0
Prototype Pollution Vulnerability: Full Technical Guide #systemweakness #cybersecurity #ethicalhacking.
systemweakness.com
By Shah kaif | “One polluted prototype can compromise an entire application.” | LinkedIn
0
0
0
I Tried CSRF Attacks in Many Website (And Failed Miserably). Here’s What I Learned #systemweakness #cybersecurity #ethicalhacking.
systemweakness.com
By Shah kaif | “Each failed payload is basically my application telling me: ‘Thanks for the pen-test, free of charge.” | LinkedIn
0
0
0
The Day I Started Thinking Like a Real Threat Hunter #systemweakness #cybersecurity #ethicalhacking.
systemweakness.com
Staring at 40GB of enterprise logs. 24 different data sources. Complete information overload.
0
0
0
Threat Modeling for AI Systems: STRIDE, DREAD, and Beyond #systemweakness #cybersecurity #ethicalhacking.
systemweakness.com
AI systems are no longer confined to experimental labs. They power real-world applications in healthcare, finance, critical infrastructure…
0
0
0