Shubham Sharma
@Shubham_pen
Followers
59K
Following
4K
Media
2K
Statuses
3K
In cybersecurity, you should be eager to learn new things.
Delhi, India
Joined February 2015
Public Key vs Private Key. #infosec #cybersecurity #cybersecuritytips #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity #cybersecurityawareness
2
82
396
Address Resolution Protocol (ARP) explained.Credit to @sysxplore . #infosec #cybersecurity #cybersecuritytips #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity #cybersecurityawareness
1
8
27
How does Docker work?.Credit to @bytebytego . #infosec #cybersecurity #cybersecuritytips #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity #cybersecurityawareness
0
2
15
HTTPS Under the Hood.Credit to @bytebytego . #infosec #cybersecurity #cybersecuritytips #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity #cybersecurityawareness
0
3
16
Security and Privacy Protocols.Credit to @LetsDefendIO . #infosec #cybersecurity #cybersecuritytips #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity #cybersecurityawareness
1
5
26
The 7 Layer OSI Model.Credit to @LetsDefendIO . #infosec #cybersecurity #cybersecuritytips #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity #cybersecurityawareness
1
3
25
How does Sender Policy Framework (SPF) works?.Credit to @sysxplore . #infosec #cybersecurity #cybersecuritytips #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity #cybersecurityawareness
0
3
23
What is DevSecOps?.Credit to @bytebytego . #infosec #cybersecurity #cybersecuritytips #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity #cybersecurityawareness
0
9
29
Linux basic file permissions for beginners.Credit to @sysxplore . #infosec #cybersecurity #cybersecuritytips #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity #cybersecurityawareness
0
5
27
4 main types of databases.Credit to @sysxplore . #infosec #cybersecurity #cybersecuritytips #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity #cybersecurityawareness
0
3
21
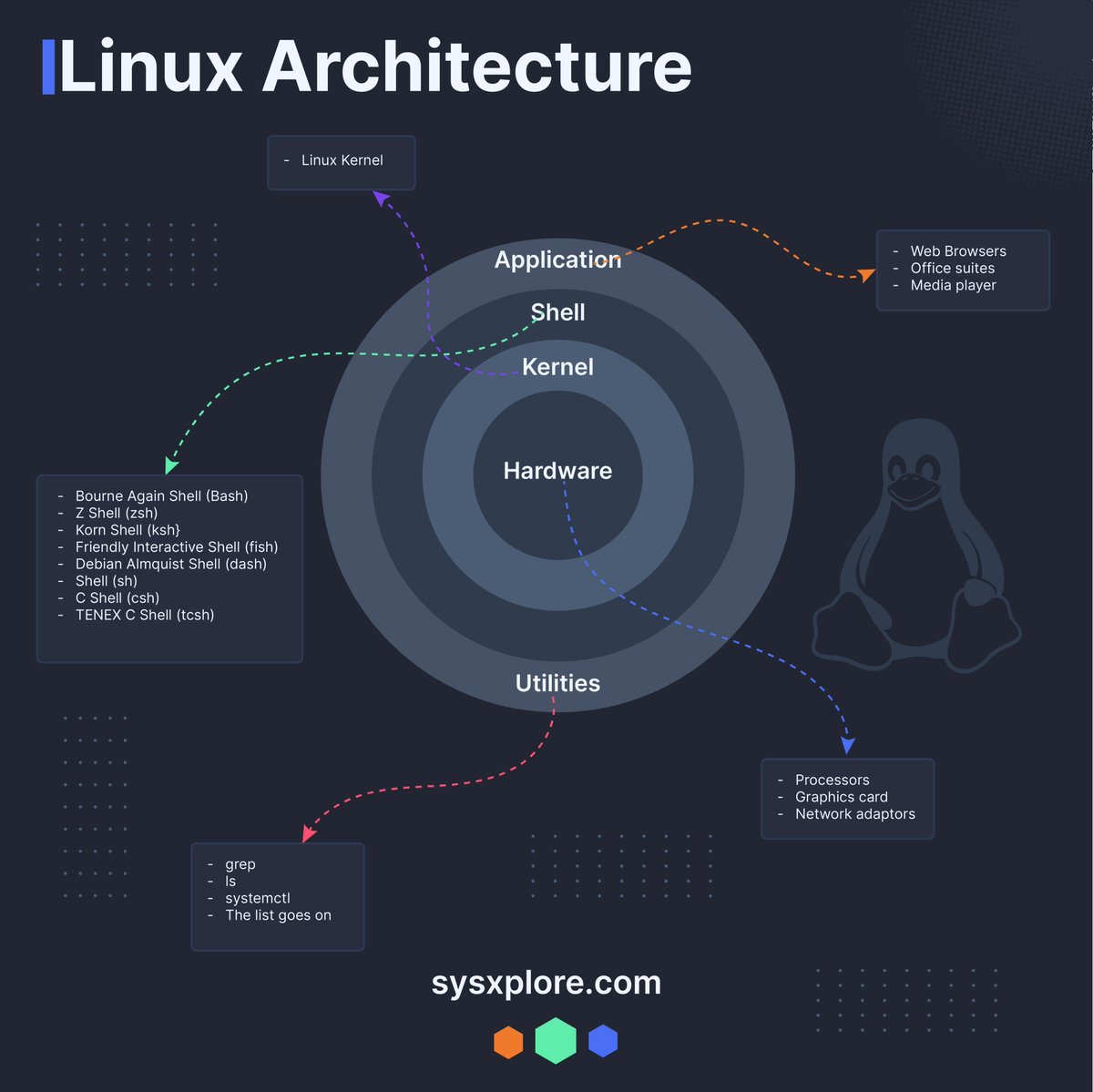
Linux architecture.Credit to @sysxplore . #infosec #cybersecurity #cybersecuritytips #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity #cybersecurityawareness
0
4
34
MITRE ATTCK vs Cyber Kill Chain.Credit to @LetsDefendIO . #infosec #cybersecurity #cybersecuritytips #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity #cybersecurityawareness
0
9
34
How DNS Works?.Credit to @LetsDefendIO . #infosec #cybersecurity #cybersecuritytips #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity #cybersecurityawareness
1
11
36
RT @Ronald_vanLoon: Public Key vs Private Key.by @Shubham_pen. #CyberSecurity #Infosec #IT #Technology . cc: @bernardmarr @gp_pulipaka @….
0
5
0
Here are a list of useful Linux commands for looking up hardware related information. Credit to @xmodulo . #infosec #cybersecurity #cybersecuritytips #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity #cybersecurityawareness
0
3
11
On Linux, the /etc directory is where system-wide system settings or app-specific config files are stored. Credit to @xmodulo . #infosec #cybersecurity #cybersecuritytips #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity #cybersecurityawareness
0
3
16
5 SOC tools soc analyst should know.Credit to @LetsDefendIO . #infosec #cybersecurity #cybersecuritytips #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity #cybersecurityawareness
0
9
27
How SSH works ?.Credit to @sysxplore . #infosec #cybersecurity #cybersecuritytips #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity #cybersecurityawareness
0
4
25
Ipsec VPN Fundamentals.Credit to @sysxplore . #infosec #cybersecurity #cybersecuritytips #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity #cybersecurityawareness
2
3
25
How to Improve API.Credit to @bytebytego . #infosec #cybersecurity #cybersecuritytips #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity #cybersecurityawareness
1
3
12
When you power on a Linux computer, a series of behind-the-scenes steps take place during the boot process before you reach the login screen.Credit to @xmodulo . #infosec #cybersecurity #cybersecuritytips #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity
0
4
22