SHASHWAT SHARMA
@Shashwat_12304
Followers
14
Following
124
Media
16
Statuses
71
Co-Founder @Datacrux.ai | AI Engineer @Alyssum @Transilience.ai | IndiaAI Fellow| Founder @Amity Competitive Programming Club | AI Researcher | ASET IT'25
Noida, India
Joined February 2023
I am at @blrtechsummit this week, representing Transilience AI. At @transilienceai, we are working toward a simple vision: an ecosystem of security agents that work together like a tireless junior security engineering team – handling the repetitive, manual heavy-lifting across
1
0
2
🚨 Toys "R" Us Canada Data Breach Analysis [Medium] Oct 24, 2025 Checkout our Threat Intelligence Platform: https://t.co/QuwNtEhw6z
https://t.co/QuwNtEhw6z
#ThreatIntelligence #CyberSecurity #Innovation #LLM #CyberSecurityWarning
0
1
2
🚨 Operation Zero Disco [High] Oct 24, 2025 Operation Zero Disco is a cyberattack campaign exploiting a vulnerability in Cisco switches to install a Linux rootkit, granting attackers persistent control over network infrastructure. The campaign exploits CVE-2025-20352, a...
0
1
2
The wait is almost over… and it’s going to be epic. Get ready – something huge is about to drop. #ComingSoon #BigReveal #EpicDrop #StayTuned #ExcitingNews #SomethingBig #Countdown #GetReady #alyssumglobal
0
1
2
When every second counts, the right solution makes all the difference. We’re getting ready to unveil it. Stay tuned - you won’t want to miss this. #Innovation #TechLaunch #StayTuned #DigitalTransformation #NextGenSolutions #AlyssumGlobal #EnterpriseTech
0
2
2
Here is a demo on how you can use our @transilienceai's Vulnerability Prioritization app and Threat Intel app to learn about the Oracle vulnerability, including IOCs, compensating controls, and detections. Both tools are open-access for the community: - Vulnerability
1
3
7
@transilienceai @grok Feedbacks on this product advisory?
1
0
0
Stop patching blind. 🧭 Launching @transilienceai Product Advisories. Every advisory ships with: • Product + affected versions • CVE + a one-line impact • Mitigations you can act on now • Linked PDF + structured IOCs • API endpoints for automation • References & timeline
2
0
2
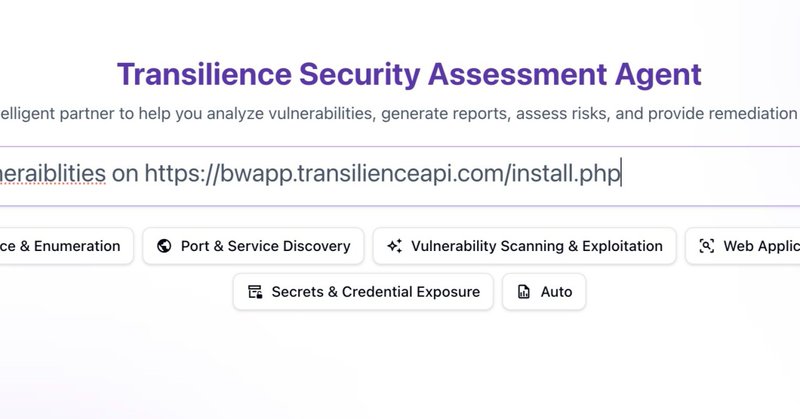
Here is a hands-on guide (2 min read) to automated web app vulnerability testing with @transilienceai PenTest Agent, including a pre-made vulnerable app for practice and a detailed breakdown of real findings and next steps from the agent. Web App Vulnerability Testing with
transilience.ai
See how Transilience AI's PenTest Agent automatically discovers vulnerabilities in web applications, analyzes findings, and provides actionable remediation steps—all at scale.
1
2
3
🚨 Malicious Listener [Critical] Sep 24, 2025 Checkout our Threat Intelligence Platform: https://t.co/QuwNtEhw6z
#ThreatIntelligence #CyberSecurity #CyberThreats #CyberAttack #CyberSecurityNews #CyberSecurityAlert #CyberSecurityWarning #CyberSecurityUpdate
0
1
1
for latest Threat Intel checkout
🚨 Shai-Hulud NPM Supply Chain Compromise Analysis [High] Sep 24, 2025 Checkout our Threat Intelligence Platform: https://t.co/QuwNtEhw6z
#ThreatIntelligence #CyberSecurity #CyberThreats #CyberAttack #CyberSecurityNews #CyberSecurityAlert #CyberSecurityWarning
0
1
2
🚨 Gamaredon–Turla collaboration [Critical] Sep 23, 2025 Checkout our Threat Intelligence Platform: https://t.co/QuwNtEgYh1
#ThreatIntelligence #CyberSecurity #CyberThreats #CyberAttack #CyberSecurityNews #CyberSecurityAlert #CyberSecurityWarning
0
1
2
🚨 Analysis of NPM Supply Chain Attack - September 2025 [Critical] Sep 15, 2025 Checkout our Threat Intelligence Platform: https://t.co/QuwNtEhw6z
#ThreatIntelligence #CyberSecurity #CyberThreats #CyberAttack #CyberSecurityNews #CyberSecurityAlert
0
2
3
An n8n script so powerful it’s like the brain of the cosmos, jacked into the internet’s core. Scans TikTok, IG, YT, LinkedIn, X & FB at godspeed, crunching a trillion signals in real time, hijacking trends before they exist! FOLLOW + RT + comment ‘N8N’ & I’ll DM free.
327
212
640
Thrilled to expand @transilienceai with our latest AI-powered penetration testing app. Our complete autonomous security suite now includes: 1️⃣ Vulnerability Prioritization 2️⃣ Threat Intelligence 3️⃣ Security Consulting 4️⃣Managed Compliance 5️⃣ AI-Powered Pentest App
1
1
3
𝗘𝗻𝘁𝗿𝗼𝗽𝘆 𝗶𝘀 𝘂𝗻𝗱𝗲𝗳𝗲𝗮𝘁𝗲𝗱. Physics tells us that if you leave any system alone, disorder increases. The same is true in business: leave a startup unchecked, and things drift into chaos - customers churn, priorities scatter, bugs pile up, and markets shift. To
0
1
0
𝗘𝗻𝘁𝗿𝗼𝗽𝘆 𝗶𝘀 𝘂𝗻𝗱𝗲𝗳𝗲𝗮𝘁𝗲𝗱. Physics tells us that if you leave any system alone, disorder increases. The same is true in business: leave a startup unchecked, and things drift into chaos - customers churn, priorities scatter, bugs pile up, and markets shift. To
0
1
0