SecurityGuill
@SecurityGuill
Followers
16K
Following
2K
Media
468
Statuses
1K
Cybersecurity Expert 👨💻 | Content for any types of audiences 💡 | You will learn something every day 📚
Joined November 2018
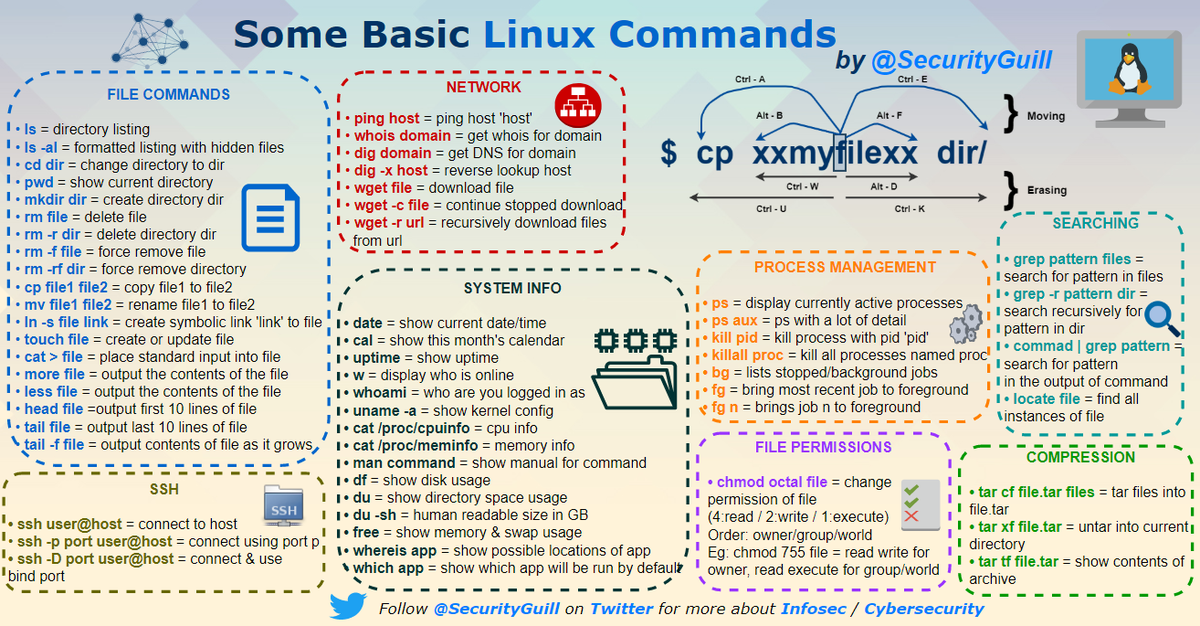
This thread brings together all my #infographics until today (2years of work). These are all infographics about #infosec 🔐. Feel free to share this tweet if you think it may be useful for your #community 📚. Follow me ➡ @SecurityGuill fore more about #security #hacking #news
42
944
2K
0-Day. It is a vulnerability in software that even the developers don't know about 👨💻. Hackers exploit this loophole before it's fixed, giving them an advantage to launch unexpected cyber attacks 🎯. 💰 They can also sell this vulnerability to other hackers. #CyberSecurity
0
1
6
Social Engineering 💡. It is a manipulative tactic used to exploit human psychology 🧠 and trust in order to gain unauthorized access or information 🔓⛔. This is based on emotions: provocation of stress, fear, nervousness. Widely used by Phishing attacks #CyberSecurity
0
3
7
Cyberattacks are becoming more numerous and sophisticated 🏴☠️. Antiviruses are no longer enough to protect yourself 🔓. 💡 Have you already heard about EDR? . 📖 I made an #infographic that explains what an EDR is! . Follow me ➡ @SecurityGuill for everything about #CyberSecurity
1
12
28
RT @SecurityGuill: [THREAD] 🧵 - You can have your entire bank account drained in seconds 🏦. I just finished a phone call with someone who j….
0
11
0
If you liked this thread, feel free to RT/share/like/comment. Follow my account @SecurityGuill for more about #infosec #CyberSecurity #cyberattack #hacking #news #technology.
0
0
0
[THREAD] 🧵 - You can have your entire bank account drained in seconds 🏦. I just finished a phone call with someone who just had their bank account emptied. 🔎 Here's how it went (3 mins read and your money safe). #CyberSecurity #infosec.#CyberAttack #hacking #news #technology
2
11
12
RT @SecurityGuill: [THREAD] 📚 - My Cybersecurity infographics . This thread brings together all my #infographics until today (2years of w….
0
43
0