SIGFLAG
@SIGFLAG_CTF
Followers
184
Following
77
Media
22
Statuses
55
CTF Team of @jkulinz
Linz, Österreich
Joined March 2017
We played @MidnightSunCTF this weekend and took 1st place as a merged team with @LosFuzzys and @SIGFLAG_CTF! Excited to meet all the other finalists in Stockholm for the MIDNIGHT SUN Finals Huge thanks to @HackingForSoju for organizing the CTF and keeping it fun right to the end
0
6
17
Peak from #glacierctf was a challenge with three ingredients: (1) An XSS vulnerability, but with (2) a strict CSP that made it impossible to include external JS scripts, and (3) a bullet-proof implementation of an image upload contact form. We hacked it anyway. Read on. (1/5)
1
1
4
9th place at SaarCTF together as KuK Hofhackerei with @SIGFLAG_CTF
@We_0wn_Y0u @TeamAustriaECSC and more! Thanks @saarsec for organizing, @JoePichlmayr and CSA for sponsoring accomodations for our guests, and IAIK @tugraz for providing the space!
0
8
23
Learn a few things about ext4 and Java decompilation in a new blog post by our teammate Robert on the recently released @sadservers_com SRE/DevOps challenges Kihei and Belo Horizonte
sigflag.at
A walkthrough through a new set of SRE/DevOps challenges
0
0
3
Big shout-out to @daho_at for being the first one in our team to get into the CVE index! ;)
CTFs can result in real-world improvements like this year's pbctf. The result: CVE-2023-25825 ( https://t.co/tkYyZti1fv) found by @SIGFLAG_CTF on @zoneminder
0
0
2
New audio data decoding write-up by our team mate Daniel on decompressme-2 from pbctf 2023 @pb_ctf
sigflag.at
Reverse Engineering of an unknown audio codec.
0
0
3
New blog post by our teammate Robert on the recently released @sadservers_com SRE/DevOps challenges Pokhara and Roseau
sigflag.at
A walkthrough through a new set of SRE/DevOps challenges
0
0
2
Let's kick-off 2023 with a comprehensive write-up by Robert Führicht on the @sadservers_com SRE/DevOps challenges
sigflag.at
A walkthrough through a set of SRE/DevOps challenges
0
0
4
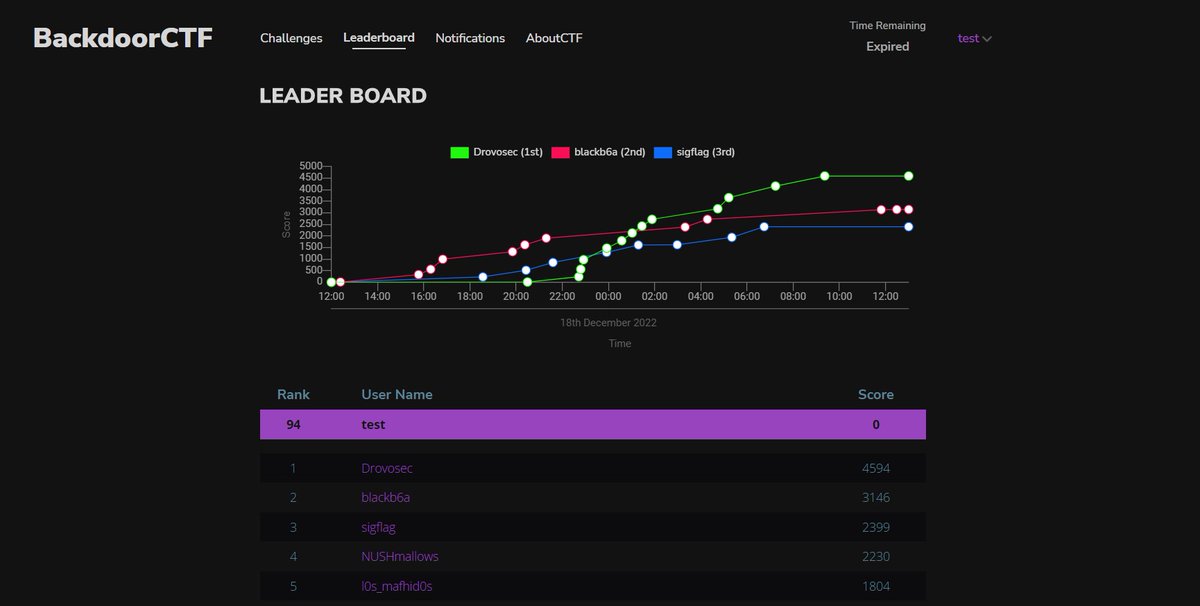
And Backdoor CTF 2022 comes to an end! Congrats to the winning teams 🎉 #Drovosec, @BlackB6a, @SIGFLAG_CTF Thanks everyone for participating and see you next year ❤️
0
3
13
Want to play some CTFs in the upcoming weeks? Join SIGFLAG on-site in Linz when we participate in #HITCONCTF2022 (26.11, today), do a TryHackMe beginner session (07.12) or attend the bi0sctf (17.12) - details at
0
2
0
THANKS to 100+ hackers that visited our BECOME A HACKER workshop today! This was AMAZING! Shoutout to Jürgen Weiss from ARES CI & @Dynatrace & @epunkt_com for sponsoring us. See you at the next competition!
1
9
20
Wow, your interest in our workshop is amazing!! Due to an update of our compression algorithm we now have even more free seats for you!
sigflag.at
SIGFLAG is looking for new members. And we want to let you get a taste of hacker air.
0
1
5
Missing the taste of hacker air? We start the new semester with the 2nd edition of our beginner-friendly IT security workshop. Register for free! https://t.co/i68o5sTDpd
0
5
6
We are looking forward to our very first hackathon! It will take place on September 17th in the GRAND GARAGE at the Tabakfabrik Linz. Please register at https://t.co/DElcvFvTHz
0
2
3
Even an up-to-date #log4j 2.17.2 didn't stop us from extracting secrets from the environment. Read how we used a ReDoS side channel attack in #GoogleCTF
sigflag.at
Even with the latest Log4j version, some injection attacks are still possible
2
82
233
Had a lot of fun escaping the maze on the final day of @OverTheWireCTF - check out my write-up if you are curious
sigflag.at
Programmatically escaping from a maze with Trémaux and dead-end filling
0
2
5
Merry Christmas everyone! As a special we play the Musical Stegano challenge from @OverTheWireCTF on real synthesizers. Enjoy! :)
0
2
3
#ructfe2019 was a great pleasure! Thanks to @RuCTFE ! And here is the write-up for the single flag in engine that we stole from NARF! ;)
sigflag.at
How to get first blood without understanding the service. Take 2.
1
1
9
Our team member @_mroland wrote about exploiting Buggy .Net from #hitconctf ;)
sigflag.at
This style of exception handling should certainly make you suspicious!
0
0
2
Informatik-Studierende der JKU @SIGFLAG_CTF und der FH Hagenberg qualifizierten sich für das Finale des internationalem „Hacker“-Wettbewerbs @VolgaCTF. 📷 oben: Markus Vogl, Tobias Höller; unten: Mario Kahlhofer, Thomas Pointhuber
3
7
27