RedDrip Team
@RedDrip7
Followers
16K
Following
6
Media
308
Statuses
401
Technical Twitter of QiAnXin Technology, leading Chinese security vendor. It is operated by RedDrip Team which focuses on malware, APT and threat intelligence.
Joined April 2018
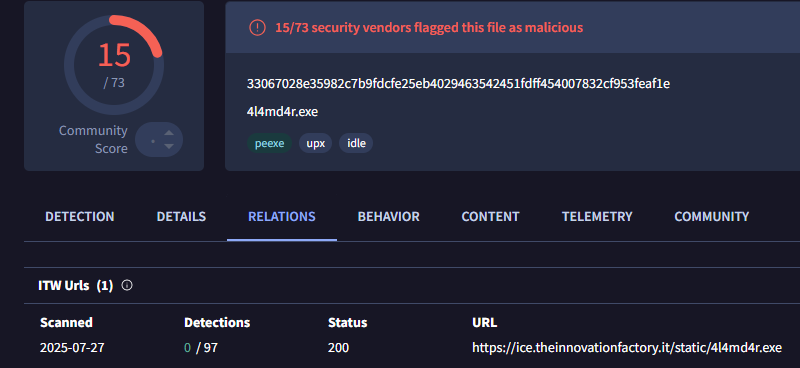
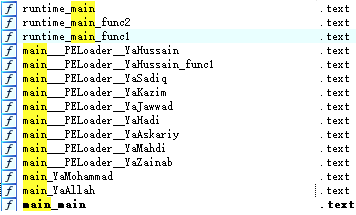
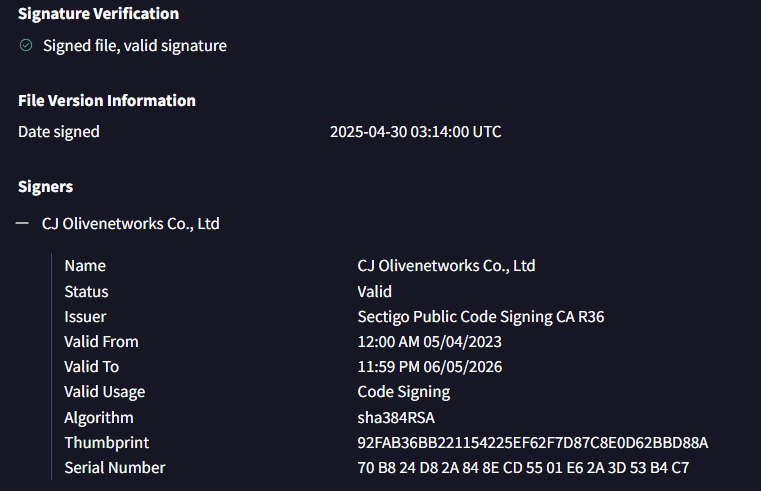
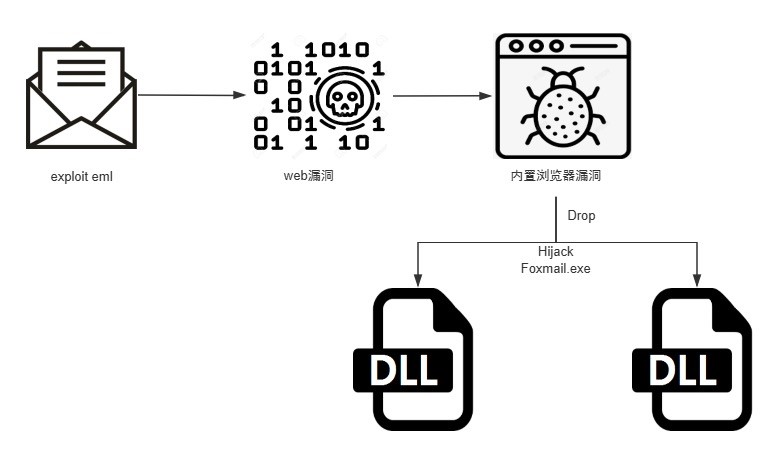
"Mimo" Gang used #Sharepoint #ToolShell to deliver "4l4md4r" #ransomware, which is written in Go language and contains religious-style function names. Report:
1
7
40
To improve threat intelligence sharing, we've released a detailed report on #APT group #NightEagle (APT-Q-95), including analysis of a novel malware, additional #IOCs, and full documentation of the Exchange attack chain. report:
At the recently held CYDES 2025, we disclosed #APT group #NightEagle (APT-Q-95). This threat group has been targeting high-tech industries for a long time, including chip semiconductors, AI/GPT and other fields. Actors used an unknown Exchange exploit chain. PPT: #IOCs #APT
1
33
73
At the recently held CYDES 2025, we disclosed #APT group #NightEagle (APT-Q-95). This threat group has been targeting high-tech industries for a long time, including chip semiconductors, AI/GPT and other fields. Actors used an unknown Exchange exploit chain. PPT: #IOCs #APT
7
24
66
#APT #Patchwork targets Nepal with Spyder malware.dcd38befbaff3b153c40cd9c2858e72a.myprivatedrives[.]com. hxxp://myprivatedrives.com/ticket_line/openai.php.hxxp://myprivatedrives.com/ticket_line/certificate.php
0
7
19