Keanu Nys
@RedByte1337
Followers
825
Following
127
Media
15
Statuses
86
Offensive Security Lead @ Spotit. Creator of GraphSpy
Belgium
Joined August 2014
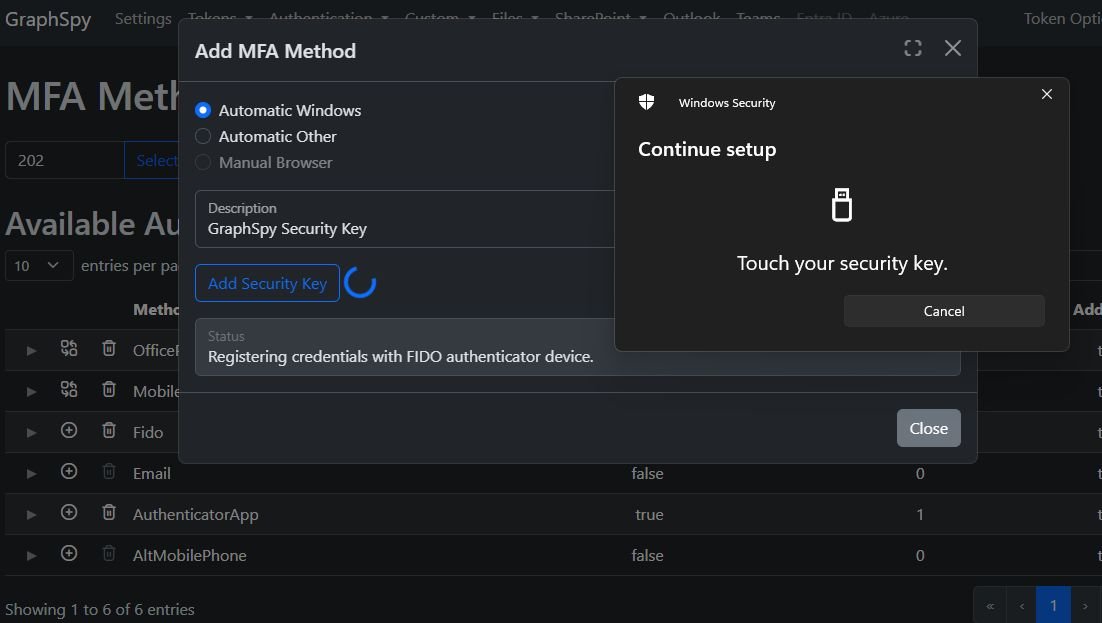
🚀I'm finally releasing GraphSpy to the public!🕵️.A powerful offensive security tool focused on making initial access and post-compromise enumeration in Microsoft Entra and M365 much more convenient during penetration tests and red team assessments!.
github.com
Initial Access and Post-Exploitation Tool for AAD and O365 with a browser-based GUI - RedByte1337/GraphSpy
2
135
366
I just noticed that the domain enumeration technique with the Autodiscover endpoint is suddenly not working anymore. This is what tools like @DrAzureAD's AADInternals (Get-AADIntTenantDomains) used to allow unauthenticated enumeration of all domains linked to an Entra ID tenant.
6
17
86
RT @nikhil_mitt: Grab a seat for one of @AlteredSecurity's three popular Red Team classes at @BlackHatEvents . Azure Attacks Advanced (In-….
0
5
0
❤️🔥 If you want to support the development of GraphSpy and get early access to new features, check out the 𝐬𝐩𝐨𝐧𝐬𝐨𝐫 𝐩𝐚𝐠𝐞 here: Thanks to @infosecnoodle and @q8fawazo for already supporting GraphSpy before this public announcement. ❤️.
0
0
5
RT @lastweekinfosec: ProxyBlobing (@_atsika), SonicWall n-days (@SinSinology), Drag and Pwnd (@d4d89704243), Loki C2 2.0 (@0xBoku), and mor….
blog.badsectorlabs.com
ProxyBlobing (@_atsika), SonicWall n-days (@SinSinology), Drag and Pwnd (@d4d89704243), Loki C2 2.0 (@0xBoku), GraphSpy 1.5.0 (@RedByte1337), and more!
0
8
0
RT @janbakker_: 💡Learn how to restrict device code flow in Entra ID!.
janbakker.tech
For good reasons, device code flow in Entra ID is getting a lot of attention. Attackers heavily use it to get access to Microsoft 365 accounts and data. Device code phishing is very effective, as...
0
4
0
RT @merill: I just published this week's Entra newsletter!. Featuring @12Knocksinna, @alitajran, @Christian_Frohn, @Ciraltos, @DanielatOCN,….
0
12
0
RT @mrgretzky: Defenders use cross-origin requests through CSS url() or injected JS to leak your phishing URL in the HTTP Referer header.….
0
35
0
Last week to register in the Azure Red Team Expert bootcamp from @AlteredSecurity!.Join me during the 4 live sessions in October to level up your Azure Red Teaming skills.
alteredsecurity.com
This 2-week advanced bootcamp is designed to help security professionals in taking their Azure Red Team skills to the next level.
0
1
3