Proton Drive
@ProtonDrive
Followers
55K
Following
2K
Media
285
Statuses
2K
Backup, share, and edit your files with #E2E encrypted cloud storage from @ProtonPrivacy. 🔍 Open-source | 🧐 Audited | 🇨🇭 Swiss | 🎁 5GB free
Geneva, Switzerland
Joined February 2016
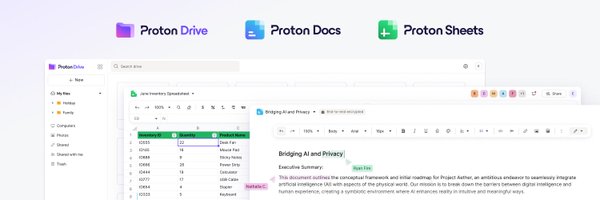
You requested it, now it’s here - introducing Proton Sheets! The privacy-first alternative to Excel and Google Sheets. Spreadsheets form the framework of modern businesses, and with Proton Sheets, you can ensure your data is private and secure. 1/4
225
401
4K
Whether you’re a small business, journalist, or startup, Proton Sheets helps you organize, collaborate, and protect the data that matters. We’re gradually rolling it out to users. Visit https://t.co/gq5XEBpu5T > New > New Spreadsheet to check it out. 4/4
12
14
274
Unlike spreadsheets provided by Big Tech, whose business model relies upon using your data, Proton Sheets doesn’t scan, track, or monetize your work. That means: ✅ You are in control 🚫 No file scanning or surveillance 🔐 Client and partner privacy is always respected 3/4
2
11
252
With Sheets, you can: 🔒 Safeguard your sensitive data with E2EE ➕ Use the built-in formulas you know and love 🕚 Work together with real-time collaboration 📊 Turn numbers into charts with data visualizations ⬇️ Easily import .CSV/.XLS 🛂 Control access at any time 2/4
2
13
251
Google says it's for compliance in regulated industries, but any org can enable it. The key takeaway here is: treat work devices like public channels, and for anything private, stick to personal devices. More on how employers spy on you here: https://t.co/VY2KvCCasB 2/3
3
12
132
Is your work phone an Android device? If so, be careful of the messages you’re sending. Google’s latest update means your employer can now read your messages. Even messages that appear end-to-end encrypted are accessible on managed devices. 1/3
52
208
1K
Apple users, don’t worry, these improvements are rolling out on iOS in the coming days. Some of you are already starting to notice 👀 Download now: https://t.co/41fAktCLj5 2/2
2
3
45
Have you noticed? The 'Gallery' in our Proton Drive app on Android now loads significantly faster, making scrolling through your photos super smooth. 1/2
24
30
356
With Proton Drive, you can securely share files with individuals/groups using secure link sharing. You can also create public links that you can easily turn on or off whenever you need. Share your files with both end-to-end encryption and full control over who can access them.
14
27
250
Windows users, what is stopping you from ditching OneDrive and switching to Proton Drive? Download the Windows app, select which folders or drives you want to be synced, and get your files off of Microsoft's data-harvesting servers.
167
68
865
Our dating advice? Keep your data locked up away from these large technology companies and their ever-increasing AI features. Read the full piece: https://t.co/aiTgECYByX 2/2
theverge.com
The dating app is testing a new feature that gets to know users by analyzing their photos.
1
3
36
Think you have chemistry? How can you be sure without letting an AI look at both of your photo rolls to check? Tinder is testing combining this invasive practice with "interactive questions" to help you find a match. I would do anything for love, but I won’t do that… 1/2
12
25
188
Knowing how to protect yourself and stay private online is important, and there are many tips and tricks out there. So to help you get started, here's a big one: https://t.co/ur2sGKpfxO
drive.proton.me
Securely store, share, and access your important files and photos. Anytime, anywhere.
14
31
276
Despite this, network security isn’t a checklist; it’s an ongoing program that evolves with your business. Start with the fundamentals, layer on more visibility and response tools as you grow, and you’ll be ahead of most organizations. Full guide: https://t.co/YNRHWWVze8 7/7
proton.me
Network security tools protect your organization’s data, systems, and users from cyber threats. We look at the best solutions for protecting your business.
1
0
24
5. Security awareness training Your team is still the first line of defense. Regular training helps employees identify phishing attempts, report suspicious activity, and foster a security-first culture that reduces human-driven risks. 6/7
1
0
19
4. Password manager Weak or reused passwords remain a top cause of breaches. A password manager enforces strong, unique credentials across your organization, simplifying onboarding, offboarding, and the secure sharing of credentials. 5/7
1
1
17