Sharan Panegav
@PanegavSharan
Followers
616
Following
2K
Media
14
Statuses
677
InfoSec Enthusiast, Bug Hunter, Dota 2 Addict
Joined April 2017
Android Deep Links Parser.A script to parse the AndroidManifest.xml and Strings.xml to list the all Deep Links of the android application.
github.com
Contribute to Shapa7276/Android-Deeplink-Parser development by creating an account on GitHub.
1
48
96
RT @galnagli: I hacked a popular vibe coding platform with a simple, straight-forward logic flaw - allowing access to private applications….
0
238
0
RT @ptswarm: 🦊 Mozilla Foundation fixed CVE-2025-6430, discovered by our researcher Daniil Satyaev!. This vulnerability allows the Content-….
0
45
0
RT @S1r1u5_: Hacking Windsurf: I asked the AI for the shell, it said yes. new video’s out. I show how I could’ve hacked you… just by getti….
0
74
0
RT @slonser_: My new research.Escalation of Self-XSS to XSS using modern browser capabilities.
blog.slonser.info
Disclaimer: This article is intended for security professionals conducting authorized testing within the scope of a contract. The author is not responsible for any damage caused by the application of...
0
178
0
RT @jeffboudier: 🥁 Today we announce a new collaboration with @nvidia to connect AI Researchers with GPU Clusters! 🤝. Introducing Training….
0
34
0
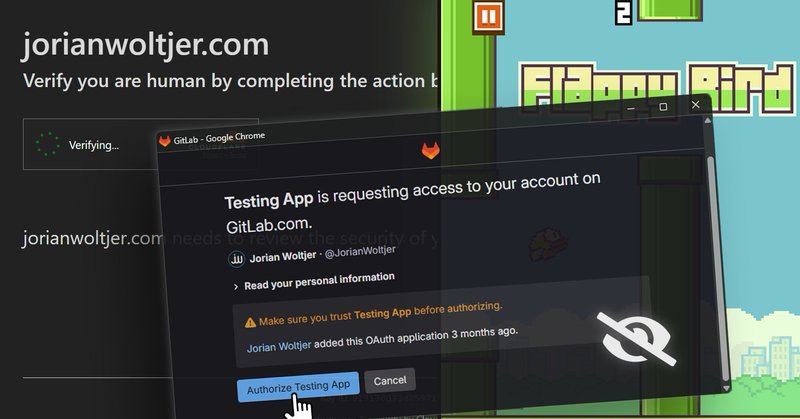
RT @J0R1AN: Double-Clickjacking, or "press buttons on other sites without preconditions". After seeing and experimenting with this techniqu….
jorianwoltjer.com
Combing a lot of browser tricks to create a realistic Proof of Concept for the Double-Clickjacking attack. Moving a real popunder with your mouse cursor and triggering it right as you're trying to...
0
48
0
RT @ri5255: I've released a blog series about modern Linux kernel exploitation, where you can learn some advanced techniques used in real-w….
0
243
0
Check out : BugBountyShorts: AI-Powered Summaries of Security Write-Ups 🎯 via @LinkedIn.
linkedin.com
Hey everyone, I'm excited to introduce a tool I've been working on—a new AI-powered solution designed to make bug bounty article reading simpler and more efficient. Let’s be honest—reading bug bounty...
0
0
0
RT @BugBountyShorts: Discover a hidden stored Cross-Site Scripting (XSS) vulnerability in an onclick event attribute! Learn to bypass HTML….
infosecwriteups.com
[Write-up] Stored XSS into Onclick Event with Angle Brackets and Double Quotes HTML-encoded and Single Quotes and Backslash Escaped.
0
1
0
RT @itsolelehmann: Everyone says Europe can't compete with America in tech. But 48 hours ago, Mistral's 'Le Chat' just proved them wrong:….
0
4K
0
RT @BugBountyShorts: The article discusses a non-technical vulnerability in the bug bounty process, often referred to as 'Overreporting'.….
0
1
0
RT @BugBountyShorts: Discover a potential DoS vulnerability in Django's IPv6 validation! By exploiting excessive resource consumption caus….
hackerone.com
###CVE-2024-56374: Potential denial-of-service vulnerability in IPv6 validation Lack of upper bound limit enforcement in strings passed when performing IPv6 validation could lead to a potential...
0
1
0
RT @BugBountyShorts: Unveil the game-changing tools of ethical hacking in 2025! Get ready to master advanced penetration testing, wireless….
osintteam.blog
In the ever-evolving world of cybersecurity and ethical hacking, having the right tools can make all the difference. As technology…
0
1
0
RT @BugBountyShorts: Boost your bug bounty game by learning how to harness the power of FFUF - a top open-source tool for discovering hidd….
osintteam.blog
master these web fuzzing methods for Easy Bounties in Bug Bounty programs
0
1
0
RT @BugBountyShorts: Discover the power of Routersploit, an open-source tool revolutionizing cybersecurity! Learn how to exploit common vul….
systemweakness.com
In the realm of cybersecurity, Routersploit is a powerful tool that ethical hackers and penetration testers rely on to target…
0
1
0
RT @BugBountyShorts: This article unveils 5 key insights demonstrating ChatGPT's edge over DeepSeek AI R1, understanding and adaptability….
medium.com
The artificial intelligence landscape is rapidly evolving, with new models emerging to challenge established leaders. One such contender is…
0
1
0
RT @BugBountyShorts: Explore the art of HTTP Request Smuggling and learn how to exploit this critical vulnerability that can lead to sess….
medium.com
The idea is to cause a de-sync at the back-end of the server that downgrades HTTP/2 requests to HTTP/1.1 on the way, either via proxy…
0
1
0