Ninad Mishra
@NinadMishra5
Followers
6K
Following
1K
Media
244
Statuses
2K
Previously ethically hacked Google, Likedin, Twitter, Paytm, Redhat, Oracle, Apple https://t.co/xU23c1Rs3s
Joined November 2020
https://t.co/XkCjhkq63F From late-night debugging sessions to being recognised by Google, LinkedIn, and Twitter, it's been a journey of passion and persistence. Discovered few CVEs, reported critical infra vulnerabilities to the indian government, and got some cybersecurity
bugcrowd.com
Ninad grew up in Bhopal, a small city in Madhya Pradesh, India. His love for his city stems from the amazing forests that add to the atmosphere of peace and tranquility. His favorite fact about...
1
2
17
Since Apple doesn’t care, I don’t care either. Here are the details of an address bar spoof vulnerability in Safari on Mac using custom cursor overlap - Apple said it’s *not* a vulnerability. https://t.co/7bW1P39iS1
59
309
4K
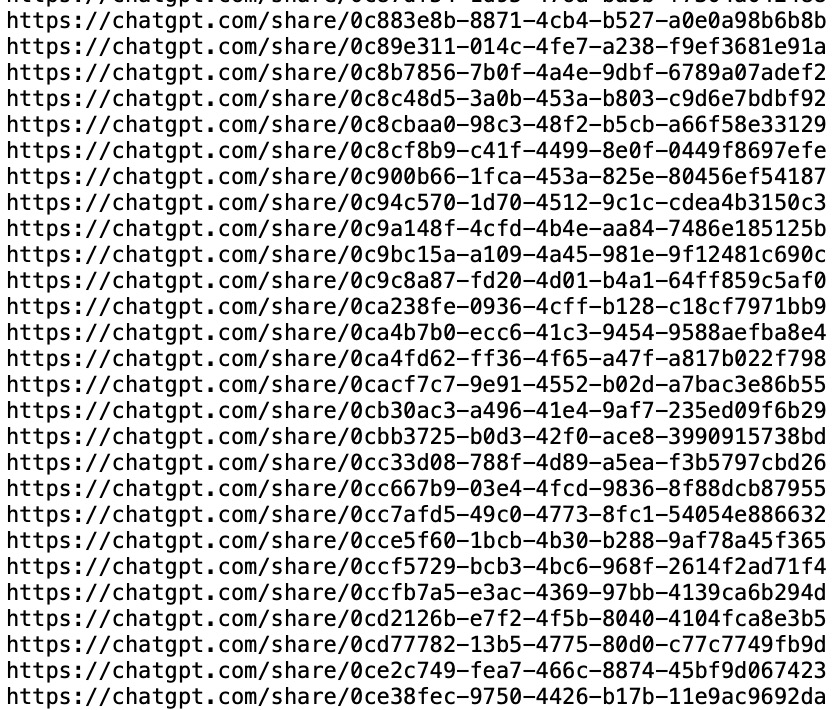
Lets understand why this is a clickbait - How links get indexed? links shared on public platforms are hit by crawlers, nothing was actually leaked here these links were shared publicly (that's how crawlers accessed it) Fix: adding an meta noindex html tag in these links
ChatGPT quietly scrubbed today nearly 50,000 shared conversations from Google's index after our investigation. They thought they'd solved the problem. They were wrong. (1/5)
0
1
6
The problem with bugbounty platforms banning researchers without accurate reasonability is that, at the end it's the customer of the platform that suffers along with the researchers simply due to bad decision making of the platform
1
0
9
New Web3 Hack👇 @OraCareUK account is compromised and scamming web3 users, by talking about a fake @pumpdotfun airdrop, look at how beautifully they're trying to scam people by using @x's article feature😍 and also have created 697 Posts so far mentioning potential web3 users
0
2
10
Imagine being so bored that you run cat ./stealerlogs/* >>new_16_B_leak.txt And then release an article of 16 billion credentials leaked And tell people that this "breach" is so new even the people releasing it don't have exact sources 😂
1
0
9
It's 2025, knowledge is free and more accessible than ever. stop getting tricked into buying a course 😂
0
1
11
AI is coming for bug bounty hunters, they say. Cool. But maybe get Grammarly to fix your writeups first.
1
0
7
Bugbounties are easy af
I once found a critical on a public bug bounty program just by viewing the source code of a page, here's what happened👇 1. Target implemented a feature allowing users to post private images on their profile 2. images were publicly accessible by URLs leaking in the html source💰
1
0
9
I once found a critical on a public bug bounty program just by viewing the source code of a page, here's what happened👇 1. Target implemented a feature allowing users to post private images on their profile 2. images were publicly accessible by URLs leaking in the html source💰
2
3
23
Infosec Ink: Learn web3 hacking Reply with your solana wallet address to get infosec ink airdrop Access: infosec[.]ink
9
5
12
Read “Unauthenticated Kibana Dashboard Access — A Serious Security Risk You Can’t Ignore“ by Pratik Dabhi on Medium: https://t.co/zZgpVx0luT
#bugbounty #infosec #hacking
infosecwriteups.com
Hello there,
1
16
54
Building a web3 security community @inkinfosec Join the discord channel https://t.co/DKDPoZeu7R
1
5
10
Cybersecurity job requirements in 2025: Entry level position: 10 years experience Must know: Every CVE since 1999 Bonus: Time travel experience preferred
1
0
8
a list of MCPs for infosec, if you use some add em here
github.com
A curated collection of MCP servers useful for bug bounty hunting - rootThatBox/BugbountiesMCP
If you're not using AI yet, you're missing out AI solving expert-level lab of @WebSecAcademy through a single prompt in 8 minutes 🔥
0
0
10
If you're not using AI yet, you're missing out AI solving expert-level lab of @WebSecAcademy through a single prompt in 8 minutes 🔥
1
6
32