Netwrix
@Netwrix
Followers
3K
Following
2K
Media
2K
Statuses
5K
Data Security starts with Identity, the #1 Attack Vector. Fast, Cost-Effective, Flexible Solutions Trusted by 13,500 Organizations.
Frisco, TX
Joined April 2009
Active Directory made simple. ADUC works, but it slows IT down with manual resets & group updates. See how Netwrix Directory Manager automates AD management: https://t.co/xKAFF9y5rM
#ActiveDirectory #ADUC #ITManagement #SysAdmin #Netwrix
0
0
0
CMMC is coming fast - Oct 2026 will be here before you know it. 🚀 Join our experts Sept 9–11 @10AM PT / 1PM ET: ✔️ What CMMC really means ✔️ Common compliance traps ✔️ How to stay ahead with classification, USB encryption & PAM 👉 https://t.co/VXtA3RZ3ep
0
1
1
🚨 ChatGPT isn’t just writing essays. It’s hacking payloads. White hat hacker Brian Johnson puts it to the test. He shows how AI is transforming penetration testing & what that means for organizations. 🎥 Watch the full webinar: https://t.co/42tswwvw4G
1
0
0
CMMC isn’t paperwork - it’s revenue protection. Miss the mark and risk losing contracts. 3 key endpoint controls keep you contract-ready (L2): • CIS/STIG hardening • Least privilege • USB control 📘 Get the ebook → https://t.co/BJcb2EDhle
1
0
1
CMMC compliance is coming — deadline Oct 2026. 🚨 Join our webinar (Sept 9–11) to learn what CMMC really means, key challenges, and how to get ahead with data classification, USB encryption & privileged access controls. 👉 Register: https://t.co/fG65PNpuhw
#CMMC #Compliance
1
0
0
Meet Michael Wetzel, our CIO in Hershey, PA 🌟 From reinventing systems to driving growth with automation & agentic AI, he’s all about fast, impactful change. His advice? “Come hungry, move fast & create lasting impact.” 🚀 Explore #LifeAtNetwrix: https://t.co/vOB5AGQkNB
1
1
1
⚡ Faster audits. Faster time to value. The director of infrastructure at a consumer goods company gives Netwrix Auditor a 5/5 rating in the Gartner Peer Insights™ File Analysis Software Market. Read the full review here: https://t.co/CplupOmwQk
1
1
1
🔎 Sensitive data is everywhere. Do you know where yours lives & how exposed it is? Netwrix 1Secure DSPM unifies data + identity protection. 👉 Book a demo: https://t.co/fSlydKRjvD
#DSPM #DataSecurity #Cybersecurity #ShadowData #CloudSecurity
0
1
1
Manual compliance checks slow you down. ⚡ Automate CIS Benchmarking & File Integrity Monitoring with Netwrix Change Tracker. Join our 30-min live demo → https://t.co/lGqJsUR9Rz
1
0
1
Cloud sprawl and GenAI are reshaping cybersecurity — and expanding your attack surface. Our new blog breaks down 2025 trends, including why DSPM is essential and how Copilot amplifies data risks. Visibility is critical. Read now: https://t.co/o4d1ryQGIm
0
1
2
Can ChatGPT really make sense of exploit data? 🤔 Yes! In seconds, it decoded a hex payload & exposed a password file. See how AI is changing penetration testing in our full webinar 👉 https://t.co/42tswwvw4G
0
0
1
🤖 Are AI Cybersecurity Tools Worth It? Absolutely — they detect threats 60% faster than traditional methods. Our free Ebook covers: ⚡ Threat detection with AI 🛡️ AI-powered cyberattacks to watch ✅ How to implement AI securely 👉 Download here: https://t.co/K5QQ8LNkfW
0
0
0
The biggest threats aren’t always obvious. Business logic flaws hide in plain sight—spotting them takes connecting insights across identities, data & infrastructure. @DirkSchrader_ explains why in @DarkReading Read here:
darkreading.com
Securing business logic isn't just a technical requirement — it's a business imperative.
0
0
1
Not all insider threats are malicious.⚠️ Some are well-meaning teammates with too much access & no idea what’s at risk. 🧑🦰 Learn how to stop privilege misuse, USB chaos & silent data movement before it’s a breach. 🔗 https://t.co/hU0fcanagQ
0
1
2
🚀 Netwrix opens its Innovation Center in Kraków, Poland—our new European hub for R&D, support, marketing, product development, and sales. A step toward faster innovation, stronger customer support, and continued leadership in data & identity security: https://t.co/ot1DD9T38V
0
0
1
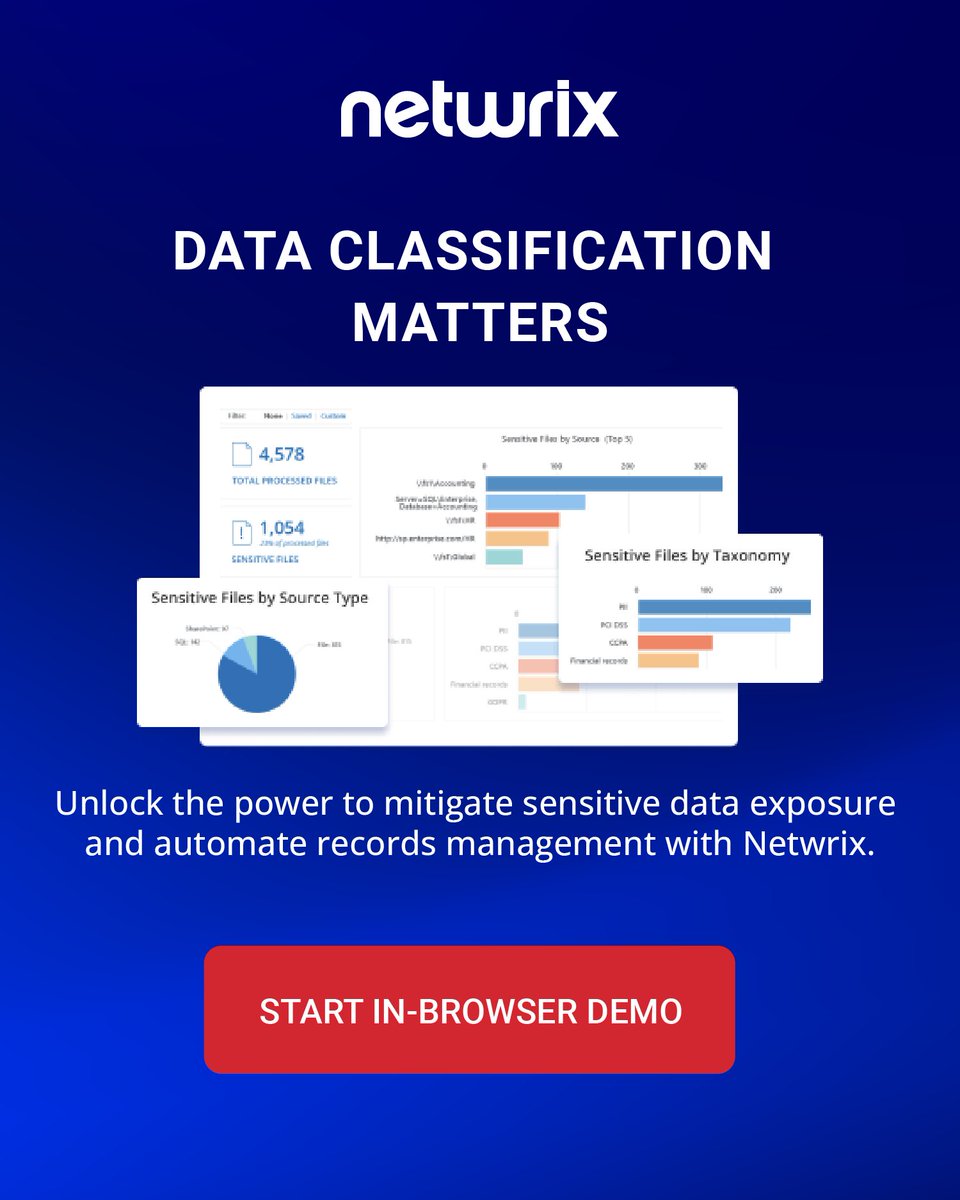
Data sprawled across systems, platforms, and teams? No wonder 3 out of 4 breaches involve files no one labeled. Join our live demo (10 am PT / 1 pm ET) to see how automated classification can protect your business and save you time + money. Link: https://t.co/RMKotCa6qk
0
0
0
Meet Carsen Cochran — our NYC-based Sr. Sales Ops Specialist who turns complex challenges into scalable solutions. From revamping Salesforce to leading cross-functional projects, she's the go-to for operational excellence. Want to join our team? Visit: https://t.co/vOB5AGPMY3
0
1
1
🔒 Would your team spot a hacker moving laterally through your systems? Netwrix DSPM helps you: ✔️ Discover & classify sensitive data ✔️ Detect threats in real time ✔️ Automate response 👀 See it. 🚫 Stop it. 🔐 Secure it. 🔗 Book a free demo: https://t.co/HAgaRxCTOO
0
0
0
Insider threats often start at the endpoint, where local admin rights, USBs, and misconfigs go unchecked. In this on-demand webinar, our expert shows how to: • Remove local admin rights • Block risky USBs and apps • Enforce policies 🎥 Watch now: https://t.co/KoBsHs8s1N
0
0
1