Mo. S.
@Mo_Sa_1983
Followers
688
Following
973
Media
38
Statuses
137
Web Application Developer
South Africa
Joined April 2011
👏❤️.
It's over in Paris! What a game, we go again next week in the #RWC2023 final. Thanks for an amazing contest @EnglandRugby 🇿🇦🤝.#StrongerTogether #Springboks #RWC2023 #RSAvENG
0
0
0
This emphasises the need for ongoing research and efforts to improve transparency and explainability in order to fully understand and trust the outcomes generated by the programmes. #BlackBoxProgramming #TransparencyInAlgorithms #ExplainableAI #AlgorithmicOpacity.
0
0
0
The internal mechanisms or decision-making processes of the programme can be like a black box, where the exact reasoning or logic behind the outcome remains unclear. #TechIndustryChallenges #EthicsInProgramming.
1
0
0
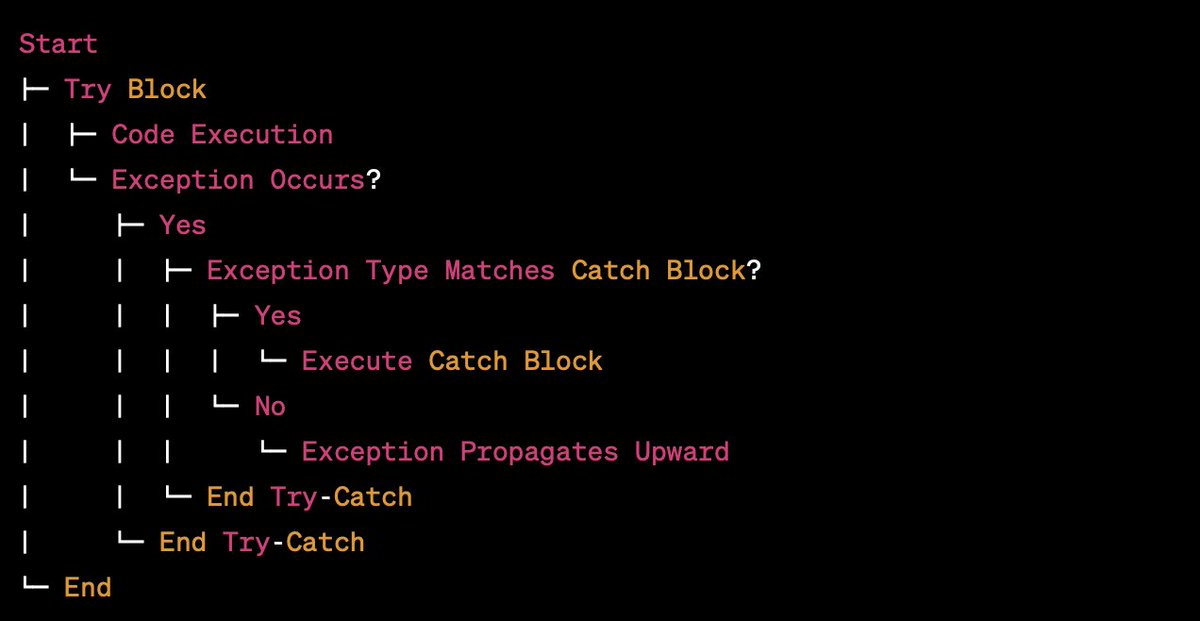
Try-Catch Blocks for Error Handling.While running our code, errors or unexpected situations may occur. We can use a try-catch block to handle these situations gracefully and prevent our programme from crashing. #ErrorHandling #ExceptionHandling #TryCatchBlock #CodeErrors
1
0
0
When you ask, Why is engineering important? .#engineering #technology #innovation #engineeringlife #engineeringstudents #engineeringeducation #engineeringinspiration #engineeringsolutions #engineeringcommunity #engineeringmindset #engineeringworld #engineeringfacts
0
0
0
Dark web . It refers to a part of the internet that is not indexed by search engines and requires special software, such as the Tor browser, to access. #DarkWeb #DeepWeb #TorBrowser #OnlinePrivacy #CyberSecurity #IllegalActivities #AnonymousCommunication #HiddenInternet.
1
0
0
Salted hash.It refers to the process of adding a random salt value to a password before it is hashed. #security #Salted_hash #cryptography #attackers #hacking #hacking.
1
0
0