Jonathan Leitschuh - [email protected]
@JLLeitschuh
Followers
4K
Following
14K
Media
104
Statuses
2K
Inaugural Dan Kaminsky Fellow | Security Researcher for the OSS Ecosystem | Speaker | Dropper of 0days (Responsibly) | @GitHub Star ⭐️ | Opinions=Mine | He/Him
Boston MA
Joined May 2010
This is my #ZeroDay #PublicDisclosure of a security vulnerability impacting 4+ Million of @zoom_us's users who have the Zoom Client installed on Mac. Zoom had 90-days + two weeks to resolve this #vulnerability and failed to do so. https://t.co/hvsoS79bos
93
3K
4K
Anyone have a security contact at @SandboxVR? A friend found a rather large data leak. They've reported it and the company has been, as of yesterday, unresponsive.
0
0
0
I've included a link to a detailed disclosure of this vulnerability here 👉
github.com
### Summary Use of `curl` with the `-k` (or `--insecure`) flag in installer scripts allows attackers to deliver arbitrary executables via Man-in-the-Middle (MitM) attacks. This can lead to full sy...
0
0
0
As a result, downstream consumers are just going to continue to get bad CVE data for MSFT vulnerabilities, as demonstrated in this case.
1
0
0
The CNA rules-as-written *forbid* us from requesting MSFT CVE numbers from CNAs like @VulnCheckAI, @fluidattacks, @RedHat , or @snyksec ; vendors that would publish better and far more accurate CVE descriptions.
1
0
0
I would argue that this CVE demonstrates how Microsoft is a bad CNA for their OSS projects. Unfortunately, as security researchers, we MUST work with Microsoft as the CNA for CVE assignment due to their scope covering all Microsoft owned products.
1
0
1
I raised these concerns to a Microsoft Security Response Center (MSRC) PM a week ago, and heard nothing back.
1
0
0
The CVE published by Microsoft fails on a couple of levels: - Microsoft doesn't include the name of the impacted project - They fail to link to the vulnerable code - No link to a fix commit - Our CVSS calculations differ: MSFT (CVSSv3.1 5.3 Med) vs my (CVSSv4.0 8.3 High)
1
0
1
Any MITM of those downloaded browsers could have allowed for arbitrary code execution on the machine of a user of Microsoft Playwright.
1
0
0
This is the description for CVE-2025-59288, a vulnerability where I had found that Microsoft Playwright (a project with 78.5k stars on GitHub) was downloading browser installers with curl using the `-k` flag; essentially meaning that TLS certificate validation is skipped.
1
0
0
.@msftsecresponse published probably one of the most opaque CVE descriptions I've seen: "Improper verification of cryptographic signature in GitHub allows an unauthorized attacker to perform spoofing over an adjacent network." Like... What is that even supposed to mean?! 🧵
1
0
0
I may have found an SSRF vulnerability in @TheASF project 'Cloudstack'. Anyone interested in helping me confirm, DM me
0
0
0
⚠️ Google’s OSV just added 500+ new advisories, not from new vulns, but from fixing a long-standing policy that made disputed CVEs invisible. Learn more →
socket.dev
A data handling bug in OSV.dev caused disputed CVEs to disappear from vulnerability feeds until a recent fix restored over 500 advisories.
0
2
4
Today we’re publishing research on 80 confirmed fraudulent candidates who applied for Socket engineering roles in the past 2 months. They’re part of a coordinated campaign, including suspected North Korean operators, aiming to infiltrate hiring pipelines. https://t.co/9KFlYYtK6k
socket.dev
Socket identified 80 fake candidates targeting engineering roles, including suspected North Korean operators, exposing the new reality of hiring as a ...
0
12
27
🚨 Malicious update to @ctrl/tinycolor on npm is part of an active supply chain attack hitting 40+ packages across multiple maintainers. Audit & remove affected versions. Our analysis of the malware: https://t.co/UsGNkZBRdj
#NodeJS #JavaScript
socket.dev
Malicious update to @ctrl/tinycolor on npm is part of a supply-chain attack hitting 40+ packages across maintainers
0
11
18
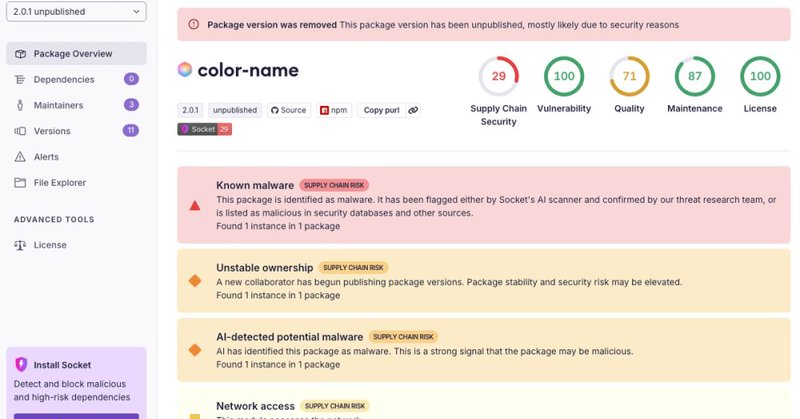
🚨 Breaking: npm author Qix compromised. Malicious package versions published in projects that typically see hundreds of millions of downloads each week. Details:
socket.dev
npm author Qix’s account was compromised, with malicious versions of popular packages like chalk-template, color-convert, and strip-ansi published.
3
23
97
@MITREcorp it would be great if you could... ya know... include the *body* of the OG request in the email response, like a sane email thread? Too much to ask? This has been this way for *years* now 😡
0
0
0
Imagine if you have multiple CVE requests pending with MITRE for different CVEs in different products. How on earth are you supposed to disambiguate the tickets from one another.
1
0
0
One of these email responses from @MITREcorp's CVE secretariat is in response to requesting 9 CVEs, one is a response to a request to join a working group. Can you tell which is which? Yea... Neither can I 🤦♂️
1
0
1
dawg, @BobDaHacker compromised McDonalds by finding one of their endpoints and ... REGISTERING AN ACCOUNT. That's all it took. It then sent a plaintext password via email. McDonalds did however apparently fix the problem when they reported it to them.
22
113
1K