IST, Inc.
@ISTIncOfficial
Followers
124
Following
140
Media
245
Statuses
809
Integrated Security Technologies is a Virginia-based corporation founded in 1997 as a full service #security integrator. #ISTOnline VA DCJS 11-5536
Herndon, VA
Joined September 2016
A recent survey reports that most defense contractors are failing to meet DFARS cybersecurity requirements resulting in a direct threat to national security.
0
0
0
The Pentagon has released a plan to direct defense agencies to implement zero-trust standards by 2027. The plan starts with getting departments on the same page in managing identity, credentialing, and access (ICAM).
govexec.com
Defense agencies are to implement zero-trust standards by 2027.
0
0
0
Recently at the Centers for Medicare and Medicaid, 254,000 records were exposed by a contractor that may have not adhered to the agency’s security obligations.
govexec.com
The Centers for Medicare and Medicaid said the breach involved a subcontractor that appears to have violated its obligations to the agency.
0
0
0
Security ranks among the four trends in improving government employee engagement. Security approaches like passwords, tokens and other barriers are giving way to zero-trust security that gives governments an edge on fraud and ransomware.
govexec.com
Four trends are showing improvements in the daily work of government employees.
0
0
0
Ransomware attacks continue to target governments and agencies. While 80% of state and local IT leaders think ransomware is a big threat, less than half have an incident response plan in place.
securitymagazine.com
What can U.S. states do to mitigate ransomware and cybersecurity risks? A two-tiered approach that begins with continuous data care best practices and diligent data recovery measures, followed by...
0
0
0
The Department of the Navy (DON) announced its cybersecurity goals for FY 2023. The plan highlights a variety of ways in which security leaders can build on existing systems to improve their protection.
securitymagazine.com
The U.S. Navy released a 2023 cybersecurity plan, Information Superiority Vision, outlining security steps the department will take to secure data.
0
0
0
The U.S. government issues documents, stores sensitive PII and disperses payments across siloed environments that have inconsistent access requirements, which makes it a prime target for criminals, says Lorraine Bellon of Cloudflare.
govinfosecurity.com
Federal government departments issue documents, store sensitive PII and disperse vast payments across multiple siloed environments that have inconsistent access
0
0
0
Experts discuss the cyber security capabilities being built by the U.S. DoE and mistakes enterprises commonly make when building ransomware defenses.
govinfosecurity.com
This week's edition of the ISMG Security Report discusses the mistakes enterprises commonly make when building ransomware defenses, the cybersecurity capabilities
0
0
0
They’re the everyday heroes whose work ensures that security and safety technologies are installed and supported so that people and property are protected. #securitytechnology #NationalSecurityTechnicianDay
0
0
0
An expert panel discusses cloud cyber security concerns, with one expert saying, “The general misconception is that cloud systems are not as secure as traditional on-premise systems, but cloud systems are actually easier to keep up to date.”
securityinformed.com
Cloud systems faced early resistance from physical security end users concerned about a perceived lack of control of data that ‘leaves’ their premises. More recently, mass adoption of...
0
0
0
A vendor working for a government contractor opened the gateway to a ransomware attack resulting in the Medicare administration having to issue 254,000 new identifiers and ID cards for affected beneficiaries.
govinfosecurity.com
More than a quarter million Medicare beneficiaries will be issued new Medicare cards and identifiers following a ransomware attack on a government contractor
0
0
0
Phishing attacks aimed at government personnel are up 30% in 2021, with half the attacks seeking to steal credentials. The survey also reports that governments increased their reliance on unmanaged mobile devices at a rate of 55% from 2020 to 2021.
securitymagazine.com
Lookout data reveals that the risk of mobile phishing and device vulnerability within U.S. government agencies has increased since 2021.
1
0
1
In this video interview, Dan Wilkins, CISO for the State of Arizona, explains how to build a roadmap to improve maturity and how to overcome roadblocks.
govinfosecurity.com
An important element of cybersecurity maturity is defining what exactly an organization is trying to accomplish, says Dan Wilkins, CISO for the state of Arizona.
0
0
0
What’s the Air Force’s cyber status? A task force is currently mapping networks as a prelude to recommending changes in spending. The goal is to find and mitigate problems with critical systems ahead of a potential conflict.
nextgov.com
To answer the question, a new task force is working to map the service’s networks.
0
0
0
A draft update to NIST digital identity guidelines includes standards for biometric proofing designed to ensure the tech’s effectiveness across demographic groups.
nextgov.com
The forthcoming draft of the government's digital identity guidelines take equity into account when it comes to fielding biometric identification tools.
0
0
0
The Biden administration is ramping up cyber security requirements for critical infrastructure and agencies are publishing new directives for public water systems, hospitals, public transportation and railroads in an effort to shore up national security.
govinfosecurity.com
The Biden administration will put more critical infrastructure sectors, such as water, under mandates to ensure minimal cybersecurity standards. The White House is
0
0
0
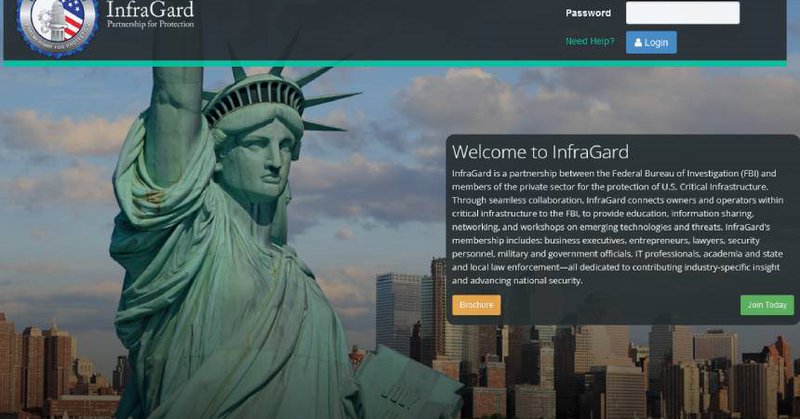
A hacker breached the FBI cyber security forum, InfraGard, using a fake email address to pose as a chief executive of a U.S. financial institution, and is now selling details of InfraGard’s 80,000+ members.
govinfosecurity.com
A hacker selling a data set purportedly containing emails stripped from the FBI's InfraGard public-private cybersecurity forum obtained access by sending an
0
0
0
Federal agencies will soon be required to regularly scan their networks and digital assets for potential vulnerabilities and report their findings to CISA. The directive is an effort to gain more visibility into the risks facing federal networks.
0
0
0
The HHS is saying that healthcare entities and their vendors should have thorough, documented and well-rehearsed incident response plans ready to execute.
govinfosecurity.com
Healthcare entities need to rehearse breach response playbooks to avoid paying fines to the Department of Health and Human Services for poor incident response after
0
0
0
The OMB has called for adopting multifactor authentication that includes verification of device-based security controls, continuous monitoring and authentication, and mandates a switch to phishing-resistant MFA by January 2023.
govinfosecurity.com
The January memorandum from President Biden’s Office of Management and Budget calls for adopting multifactor authentication that includes the verification of device-based security controls, continu...
0
0
0