Hash Suite
@HashSuite
Followers
327
Following
0
Media
0
Statuses
21
Hash Suite is a program to audit security of password hashes
Joined October 2012
Hash Suite 4.0 (Windows) adds support for custom Python scripts as key-provider, updated wordlists to download, better high-resolution support, and should have fewer antivirus false positives.
0
2
4
Hash Suite Droid 1.6, our Open Source password hash cracker for Android, supports Android 11 scoped storage enforcement and no longer requires the READ_EXTERNAL_STORAGE and WRITE_EXTERNAL_STORAGE permissions. Homepage: https://t.co/sSw1D848Ix Google Play:
2
4
5
Hash Suite 3.7 (Windows) and Hash Suite Droid 1.5+ (Android) add support for sha256crypt and sha512crypt. Windows download or purchase: https://t.co/eusSd0yP3d Android download (free only): https://t.co/sSw1D848Ix Also on Google Play:
0
3
4
Hash Suite Droid 1.4, our Open Source password hash cracker for Android, is a release focusing on reliability enhancements, including automatic self-test at the start of each attack. Homepage: https://t.co/sSw1D848Ix Google Play:
0
9
5
Hash Suite 3.6 adds support for hashes import from a Domain Controller using replication APIs, from local registry, from offline backup of registry files, from offline Active Directory database (ntds.dit file), and from memory (already authenticated users)
1
3
4
We've just released version 1.3.2 of Hash Suite Droid, our Open Source password hash cracker for Android. This is a minor update focusing on usability enhancements and bug fixes. Homepage: https://t.co/sSw1D848Ix Google Play:
0
0
1
We've just released version 1.3.1 of Hash Suite Droid, our Open Source password hash cracker for Android. This version brings new hash types and features from Hash Suite for Windows to Android. Homepage: https://t.co/sSw1D848Ix Google Play:
0
9
7
Hash Suite 3.5.1 is out, fixing bugs identified since the 3.5 release. This is a free upgrade to those who purchased 3.5 Standard or 3.x Pro, and it appears automatically in the download directories that were created for those orders.
0
2
3
Hash Suite 3.5 supports cracking millions+ hashes at once as tested on 320M SHA-1 hashes from Pwned Passwords v1 on a 16 GB RAM machine. Got more RAM in your Windows box? Try 517M SHA-1 or NTLM from PP v3 and let us know! Downloads: https://t.co/eusSd0yP3d
haveibeenpwned.com
Pwned Passwords is a huge corpus of previously breached passwords made freely available to help services block them from being used again.
0
10
13
Our guide for windows admins looking to conduct password audits just went live on the #trustedsec blog https://t.co/KOECTibVGv
0
28
52
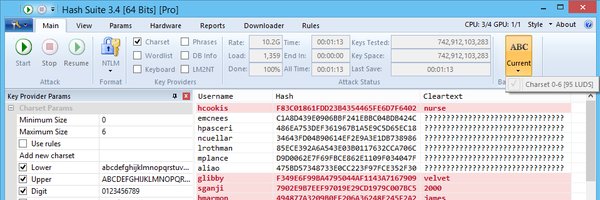
Hash Suite 3.4 adds SSHA, md5crypt (5.5M vs. 3.6M for cudaHashcat 2.01 at length 7 on GTX 970), "fingerprint attack"
1
5
7
Hash Suite 3.3 (Windows, paid) and Droid 1.2 (Android, free) add cracking of WiFi WPA-PSK, SHA-256, SHA-512, bcrypt:
0
10
14
Hash Suite Droid 1.1 (free) adds mobile GPU support: desktop CPU like speeds, 2+ hours battery life on Galaxy S5: http://t.co/gQ4H9C9lQ5
0
9
3
Hash Suite 3.2 adds raw MD5, raw SHA-1, DCC2 on CPU and (multi-)GPU, outperforms the competition as usual: http://t.co/q3YwwL5XvW
0
4
1
Hash Suite password cracker for Android is now Open Source (GPLv2+) http://t.co/gQ4H9C9lQ5
https://t.co/60prmuzUqb
http://t.co/dz0T098mhR
github.com
Hash Suite for Android. Contribute to alainesp/HashSuiteDroid development by creating an account on GitHub.
0
9
12
We've just released Hash Suite Droid (free), the first multi-hash cracker developed specifically for Android devices: http://t.co/gQ4H9C9lQ5
0
19
14
Hash Suite 3.1 adds on-GPU rule engine, AVX2, tutorial http://t.co/PGIoYPfqKB using @CrackMeIfYouCan's 2010 contest hashes, Hash Suite Free
0
9
4
As far as we're aware, Hash Suite 3.0 is now world's fastest LM hash cracker on CPU and GPU: 5350M c/s on 7970GE (vs. oclHashcat's <1400M)
0
5
2
Hash Suite 3.0 adds GPU support, concurrent use of (multi-)CPU and (multi-)GPU: http://t.co/knh95aSrxG Demo/purchase: http://t.co/Bh87GIzxDj
0
4
4
Hash Suite 2.1 speeds up LM and NTLM cracking at >65k hashes and on CPUs with AVX: http://t.co/8IoLsDXX
0
2
2