⠠⠵🕵️⠠⠵
@Gh0st_3xp101t
Followers
319
Following
602
Media
166
Statuses
1K
🕵️ Security Researcher 🔥 Open Source 🎯 Software Developer 😈 #pentester ⚡ #codeislife ☄️ #0day 💥 #exploit 🔮 127.0.0.1:1337 🎲 #bugbounty 🃏 #infosec 🎭
France
Joined May 2013
Even though I'm posting this to get a 35% off coupon, I cant avoid saying it's freaking cool:
lo.cafe
A whole new way, full of possibilities of using your macos notch
0
0
1
RT @citronneur: Powershell deobfuscator
github.com
Powershell Linter. Contribute to airbus-cert/minusone development by creating an account on GitHub.
0
41
0
RT @pentest_swissky: SeeSeeYouExec: Windows Session Hijacking via CcmExec @googlecloud
cloud.google.com
0
15
0
RT @cyb3rops: When I look at this table, the first thing I see is that size matters more . I reckon users prefer being told: „use a passwor….
0
105
0
RT @pentest_swissky: AWS Cloud Security Config Review using Nuclei Templates
projectdiscovery.io
We're excited to tell you about Nuclei Templates release v9.8.5! This new version includes newly added AWS cloud review templates. In this blog post, we'll discuss automating cloud misconfiguration...
0
31
0
RT @theori_io: Do you use a virtual machine to browse dangerous links safely? If you use the Chrome browser inside that virtual machine, is….
0
266
0
RT @hack_git: IOS17 Crash Exploit. The Exploit was original found by ECTO-1A and then refactored by WillyJL. I portet it to the ESP32 from….
0
103
0
RT @therceman: Bug Bounty CheatSheet. jQuery XSS Payloads. 🔹 CVE-2020-11023.🔹 CVE-2020-11022.🔹 CVE-2019-11358. 🔗 ht….
0
69
0
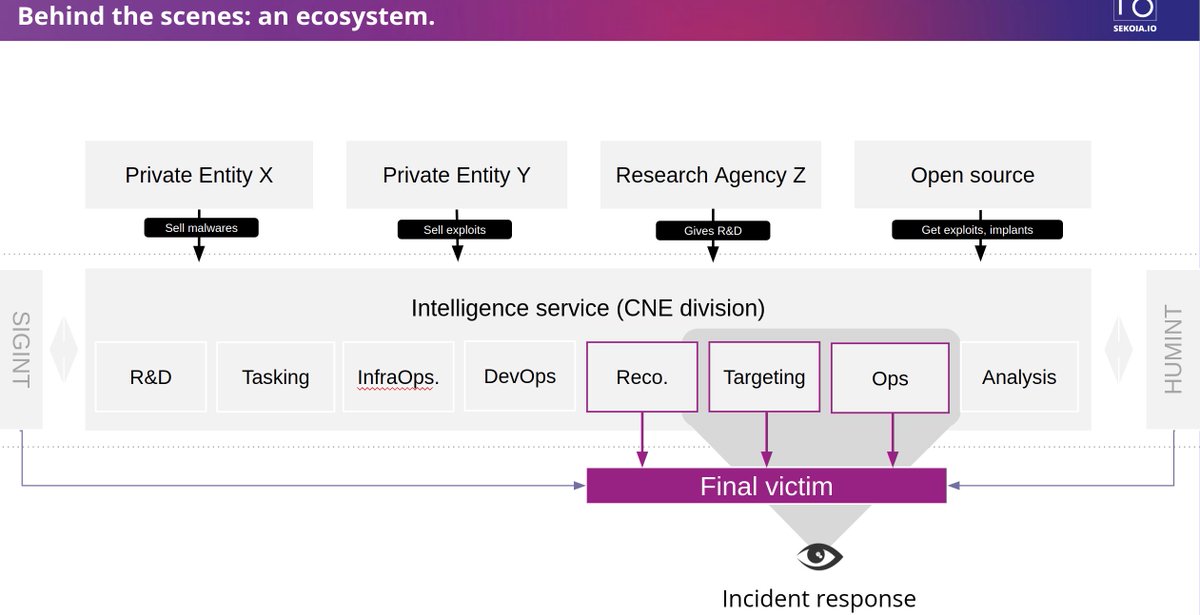
RT @felixaime: An old scheme that I still like to present some perspective regarding cyber "stuff".
0
7
0
RT @blackorbird: #APT28 used "Microsoft Edge" as a bootloader, TOR and mockbin[.]org/website[.]hook services as a control center. Any reque….
0
80
0
RT @mpgn_x64: New release of crackmapexec is out ! 6.1.0🥳. This version now support of a new protocol : WMI by @Memory_before ! If the SMB….
0
201
0
RT @Massilia93: iphone 11 Pro trouvée dans le #RERA à Marne la Vallée poser sur un siège. Si c’est à toi viens faire le code. @RER_A https:….
0
72
0
RT @NeobeePaul: RedTeam Pentesting - Blog - Introducing resocks - An Encrypted Back-Connect SOCKS Proxy for Network Pivoting .
blog.redteam-pentesting.de
Compromising a host in a company’s perimeter often creates the opportunity to pivot into an internal network. From there on, each additional compromised system may grant us access into further...
0
36
0
RT @_cablethief: Excited to teach wireless hacking and try to convince more people that using wpa_sycophant is easier than it seems (most o….
0
17
0