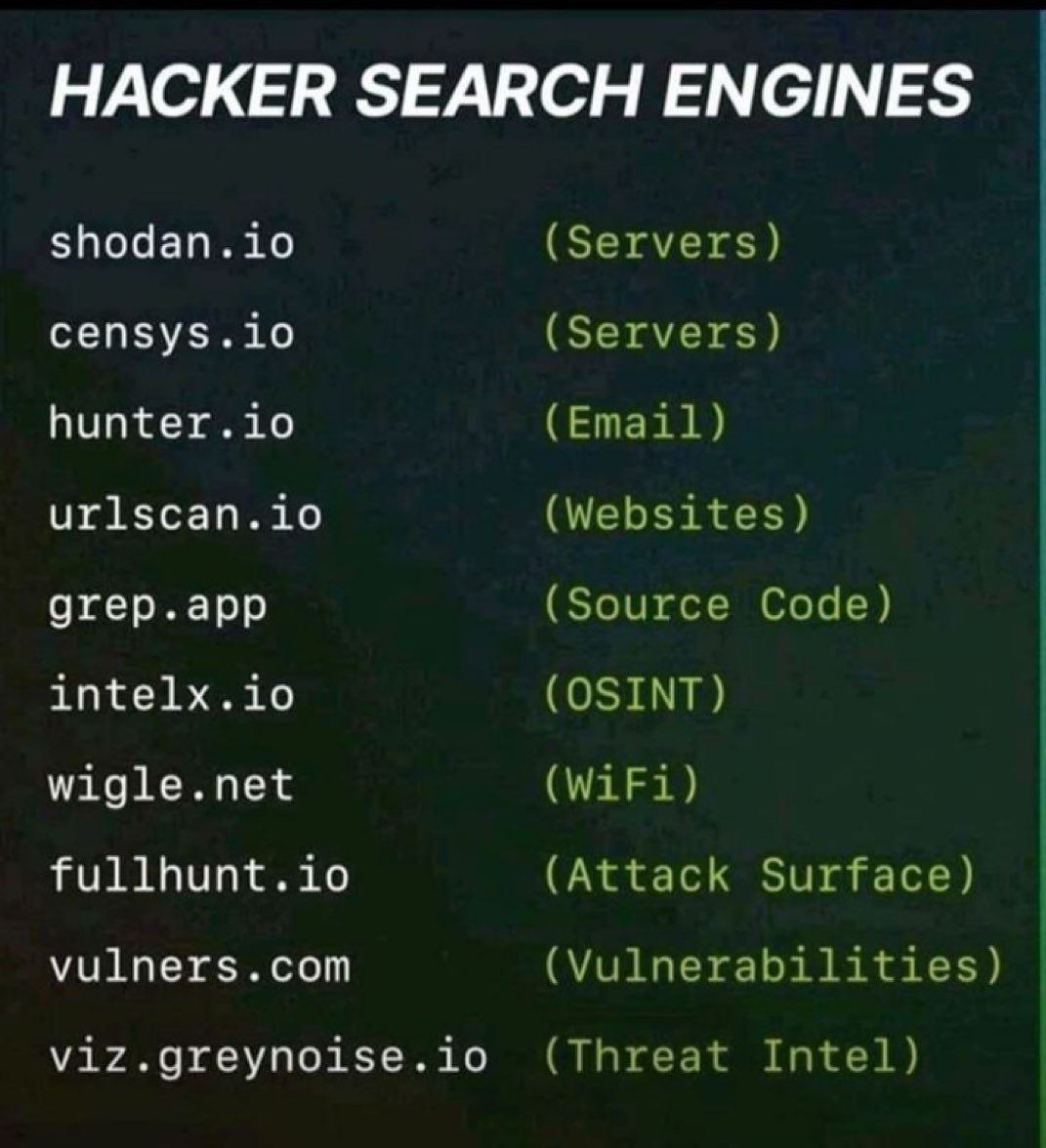
Elevate Cyber
@ElevateCyber
Followers
328
Following
5
Media
135
Statuses
250
I help beginners land cybersecurity jobs in only 6 months. DM me the word “Elevate” ⬆️
Joined December 2020
RT @netbiosX: Bypassing AppLocker when PowerShell and CMD are Locked Down
umsundu.co.uk
The Scenario: In this scenario, we have access to a Windows 10 host where an AppLocker policy is enforced, explicitly blocking access to cmd.exe, powershell.exe, and powershell_ise.exe for a specific...
0
68
0
RT @hackthebox_eu: The #HTB ecosystem just got a lot stronger 💡.We’re thrilled to welcome @vulnlab_eu to our HTB multiverse, further addres….
0
71
0
RT @Malcoreio: Today we are releasing our FREE educational course: "Intro to Exploit Dev"!. This course is perfect for those trying to star….
0
192
0
RT @C5pider: spend some time rewriting stardust to be more minimalist and easier to use! I needed a generic minimal shellcode template that….
0
34
0
RT @MarcMenninger: 🔍 How to Analyze a Suspicious File Without Getting Infected. You just received a sketchy file. It could be harmless, or….
0
224
0
RT @GrahamHelton3: Golden Ticket Attack In Kubernetes? 🤔. A new post exploitation & persistence tool for Kubernetes just came out called Ku….
0
91
0
RT @CyberWarship: ''ShadowHound: A SharpHound Alternative Using Native PowerShell''. #infosec #pentest #redteam #blueteam..
blog.fndsec.net
ShadowHound is a PowerShell tool designed for mapping Active Directory environments without using known malicious binaries. It utilizes legitimate PowerShell modules for data collection through two…
0
72
0
RT @ksg93rd: #DFIR.#Malware_analysis.1. WMI Malware:.The Complete Forensics Guide.2. Confluence Exploit Leads to Lo….
cybertriage.com
Attackers can use WMI malware for just about anything. Execution, persistence, lateral movement… honestly, the list goes on. Fortunately for you, there
0
15
0
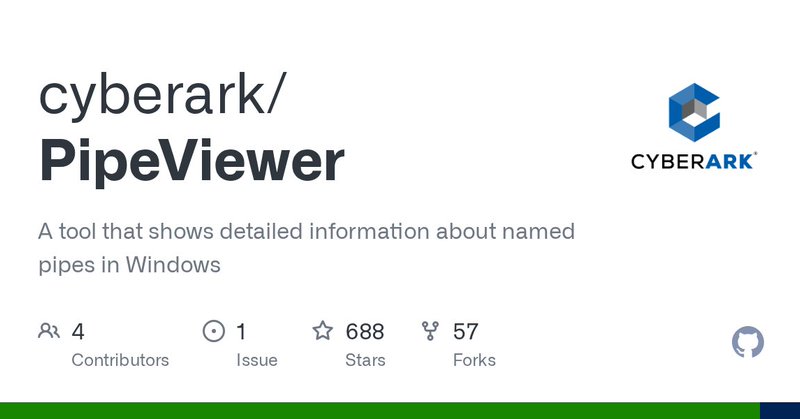
RT @DirectoryRanger: PipeViewer. GUI tool for viewing Windows Named Pipes and searching for insecure permissions.
github.com
A tool that shows detailed information about named pipes in Windows - cyberark/PipeViewer
0
62
0
RT @DirectoryRanger: WMI Malware: The Complete Forensics Guide #DFIR.
cybertriage.com
Attackers can use WMI malware for just about anything. Execution, persistence, lateral movement… honestly, the list goes on. Fortunately for you, there
0
36
0
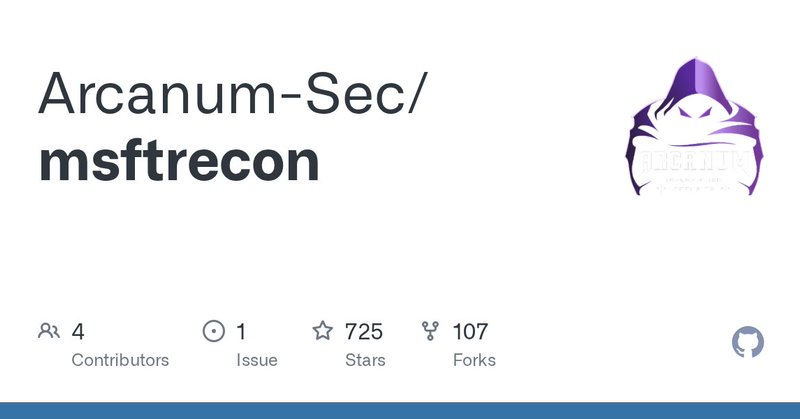
RT @sapirxfed: HUGE enumeration tool for Azure WITHOUT AUTHENTICATION!.This tool is amazing! It reminds me what @DrAzureAD did a couple of….
github.com
Contribute to Arcanum-Sec/msftrecon development by creating an account on GitHub.
0
90
0