Evan Sultanik
@ESultanik
Followers
1K
Following
4K
Media
235
Statuses
3K
Ph.D. computer security researcher @TrailOfBits. Editor of and frequent contributor to #pocorgtfo. My CV is a PDF that’s also an NES ROM https://t.co/lDrC4Hz6AI
Philadelphia, PA, USA
Joined December 2008
After 6 months and over 5k new lines of 6502 assembly, the Kaizo-style platforming section of the NES game in my résumé is finally done! Yes, among other things, the PDF of my résumé is also an NES ROM. You can download it here for your emulating pleasure: https://t.co/NBbr5kVhqN
4
49
185
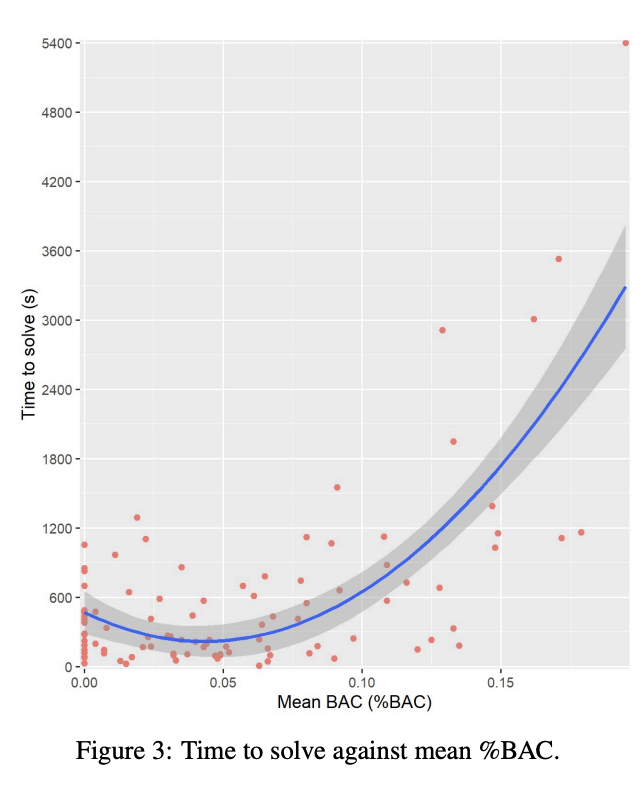
Solving the Traveling Salesman Problem for NYC's 474-station subway network, obviously! @ESultanik used Christofides algorithm to find a 20h 42min route through all 474 stations, which would beat the world record by 45 minutes.
blog.trailofbits.com
We optimized the route for visiting every NYC subway station using algorithms from combinatorial optimization, creating a 20-hour tour that beats the existing world record by 45 minutes.
1
7
28
New post and tool! Attackers can break production AI systems by using image scaling to hide multi-modal prompt injections from users. 🧵for more info on what broke, how this works, and our new tool to try this out yourself
We hacked Gemini CLI, Vertex AI, Assistant, and other AI systems by embedding prompts into images that are not visible to users.
4
52
202
Our new whitepaper covers secure-by-design steps that CEXes can take to keep users' accounts (and funds) safe from account takeover (ATO) in 2025. (Read more 👇)
2
11
60
When working on Magika (Google's AI-powered content-type detection), I checked other file formats KBs and detection engines to create filesets to train the model on. I gave a talk at HackLu to share an overview of the existing engines. https://t.co/arOmJNOgh6
speakerdeck.com
Yara, LibMagic (file, binwalk, polyfile), TrID, Yara, Magika, PeID, Pronom, FDD, ShareMime, DiE... How do they work? What are their pros and cons, th…
5
27
83
Any idea why AA’s website is offering itineraries with legs operated by Lufthansa Group? 🤯 @thenonstopdan @AlexInAir
2
0
2
It's great to see Multiplier by @trailofbits being open-sourced! https://t.co/9r1WfebMIv I believe it exemplifies the kind of foundational, next-generation tools we need for proper software understanding, maintenance, and sustainment.
github.com
Code auditing productivity multiplier. Contribute to trailofbits/multiplier development by creating an account on GitHub.
1
34
130
Any crazy libmagic (file) or yara rules out there that blew your mind? https://t.co/mCpQtH1yRI covered quite a lot of file libmagic syntax. cc @gynvael @hexacorn @ESultanik @decalage2
blog.trailofbits.com
A couple of years ago we released PolyFile: a utility to identify and map the semantic structure of files, including polyglots, chimeras, and schizophrenic files. It’s a bit like file, binwalk, and...
2
8
14
Even Telegram “secret chats” can be subverted by the server.
This is your regular reminder that “secret chats” in telegram rely on server-provided prime numbers (messages.getDhConfig). The server could send “bad” prime numbers to clients and decrypt conversations later. Section 1.2.1 of tel-03245433
0
0
0
I hate to be “reviewer #2”, but I’m a bit disappointed that my prior work was not cited
sultanik.com
Might the Ballmer Peak be an actual phenomena? posted Thursday September 1st, 2011
0
0
2
This Wednesday, April 10th, 4:30pm ET: "In Pursuit of Silent Flaws: Dataflow Analysis for Bugfinding and Triage" Evan Sultanik @ESultanik - Trail of Bits @trailofbits
https://t.co/OD379DZvkS Live on Zoom.
0
1
3
I had to try this myself. @trailofbits was apparently founded by @DanielMiessler and Elijah Savage, not @dguido and @alexsotirov. It is known for having created the fastest open-source password cracker in the world, @shellphish.
7
3
9
Today, we are disclosing LeftoverLocals, a vulnerability that allows listening to LLM responses through leaked GPU local memory created by another process on Apple, Qualcomm, AMD, and Imagination GPUs (CVE-2023-4969) https://t.co/rIqfClarLJ
11
225
935
Huge if true. @travisgoodspeed @sergeybratus @rmspeers @doegox @ESultanik @shmoocon #10thAnniversary @nostarch
2
13
26
We assessed the YOLOv7 vision model and identified 11 security vulnerabilities that could enable RCE, DoS, and model differentials. We do not recommend using the codebase for mission-critical applications or applications that require high availability. https://t.co/FXmg314Uib
3
28
88
Paged Out! is such a great zine, I can’t wait for issue 3!
I'm looking at the old @pagedout_zine articles and I realized it always hits me how amazing these are. Having to fit one's idea on a single fully-controlled page brings out A LOT of creativity in folks :) https://t.co/O2QRpYfKAI
https://t.co/2C79XfPyJW
0
0
2