Digital Guardian
@DigitalGuardian
Followers
17K
Following
2K
Media
8K
Statuses
13K
Provider of data protection solutions and services that have secured businesses around the world since 2003. A key part of @FortraOfficial.
Eden Prairie, MN
Joined March 2012
Social security numbers, credit cards, email addresses, phone numbers. When it comes to data, what's the difference between sensitive and personal data?
digitalguardian.com
Social security numbers, credit cards, email addresses, phone numbers. When it comes to data, what's the difference between sensitive and personal data?
0
0
0
CMMC 2.0 will require an estimated 76,000 organizations to maintain a level 2 or 3 certification to bid on and hold DoD contracts. Need some help? Join this @ITBrew webinar for all the need-to-know points on CUI and CMMC compliance:
0
0
1
ISO 27001 is an international standard for information security management. Learn the ins and outs of ISO 27001, including the benefits of certification and implementation, how it helps secure data, and how to maintain compliance in this blog:
digitalguardian.com
0
0
0
Data tokenization is a security method for replacing sensitive data with non-sensitive, unique tokens. Learn about how it works, why it's important for data security, and some of the challenges of data tokenization in this new blog.
digitalguardian.com
0
0
0
"In 2025, new global regulations like the EU AI Act, GDPR updates, Malaysia’s privacy laws, and U.S. state privacy laws are reshaping compliance. " Good to see our Wade Barisoff in @byronacohido's Last Watchdog:
0
0
1
The Defense Industrial Base (DIB) is vast. It comprises more than 100,000 companies and subcontractors that work under contract with the Department of Defense (DoD). How can these organizations go about securing sensitive defense information?
digitalguardian.com
Learn why the Defense Industrial Base (DIB) continues to be a ripe target for cyberattacks, how the CMMC affects DIB contractors, and how to form a robust DIB cybersecurity framework.
0
0
0
In the UK, the GSC - or Government Security Classifications - utilizes three classification tiers: OFFICIAL, SECRET, and TOP SECRET, each representing a different level of sensitivity. Learn more about the system in this blog:
dataclassification.fortra.com
GSC is a policy system used by the UK government and public sector organizations to classify their information and data assets. Read this blog to learn more about the system, why it's important,...
0
0
0
It's the first Release Day of 2025! 🚀 That means new updates for @DigitalGuardian and Fortra's Data Classification. Learn more:.
Fortra Release Day 2025.1 is here! Explore enhancements, updates, and fixes from our solutions. Highlights include a Proactive Security module for GoAnywhere, enhanced admin management in DCS Policy Manager, and more. Dive into the updates:
0
0
0
Working with CUI? Standards have and will change, so you need a tool that's flexible to meet those changes with the click of a mouse vs. waiting on vendors to make changes to address the new standards. Learn how @fortraofficial can help:
dataclassification.fortra.com
Explore what the Cybersecurity Maturity Model Certification program is and what affected organizations need to do to achieve CMMC compliance.
0
0
0
To support compliance requirements and legal exposure, organizations must understand the privacy, legal, and data compliance implications of storing data.
digitalguardian.com
Data residency refers to the physical or geographical location where an organization's data is stored to servers, databases, or data centers. Learn more about data residency in today's blog.
0
0
1
Audit logs and audit trails document a complete historical record of system actions and activities. They serve as a security measure to monitor and verify system activities, ensure compliance, and aid in troubleshooting and forensic investigations.
digitalguardian.com
An audit log is a document that records the activities within an application, system, or network. Learn more about audit logging in today's blog.
0
0
0
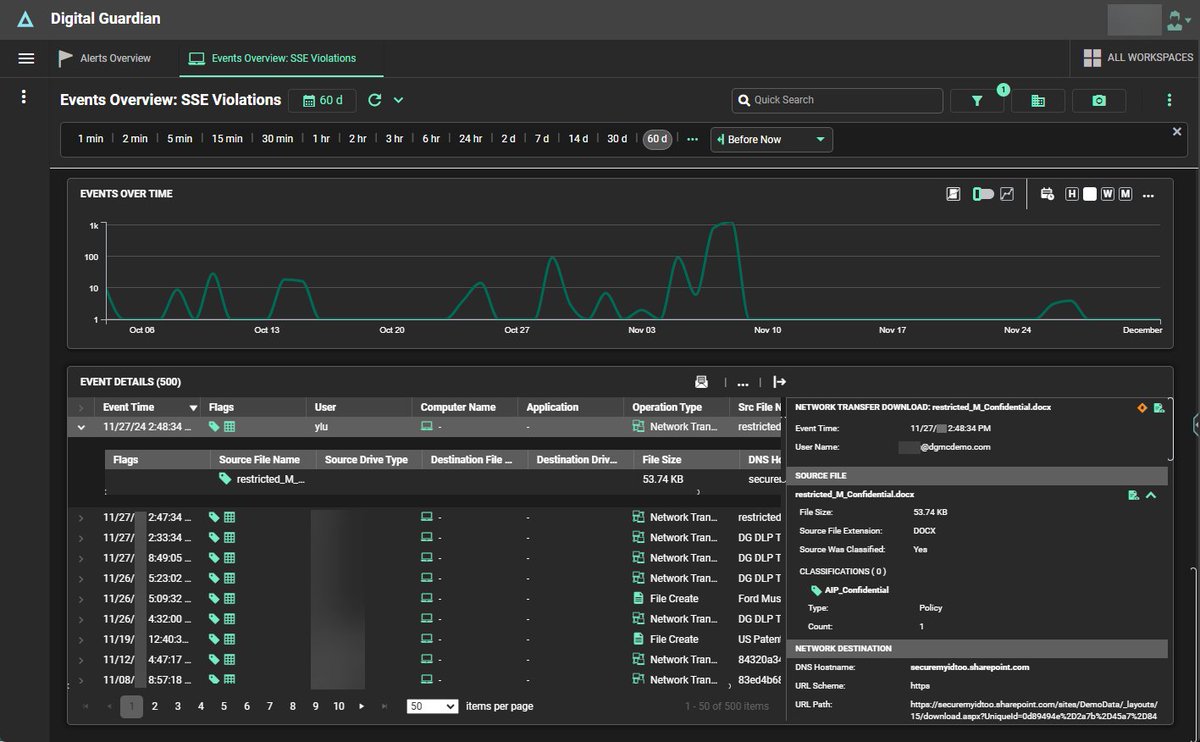
Today, companies need to demonstrate that they're making a “best effort” to manage the data they oversee; Digital Guardian's SSE solution provides the information needed to manage data loss risk.
digitalguardian.com
Today, companies need to demonstrate that they're making a “best effort” to manage the data they oversee; Digital Guardian's new SSE solution provides the information needed to manage data loss risk.
0
0
0
Data mining risks refer to the potential pitfalls and negative consequences associated with the data mining process. Learn more about data mining risks and how to protect yourself from them in this blog:
digitalguardian.com
Data mining risks refer to the potential pitfalls and negative consequences associated with the data mining process. Learn more about data mining risks and how to protect yourself from them in this...
0
0
0
Cybersecurity measures in the NDAA, a major supply-chain attack on security experts, and new federal cloud security mandates were among this past week’s top stories. Catch up with @dangoodin001 @ddimolfetta @mattbracken @lizoleeta + @carlypage_:
0
0
1
What are the key components of an effective incident response plan? Preparation and having an incident response plan are only part of it. Learn more:
digitalguardian.com
An Incident Response Plan (IRP) is a strategic document that outlines the procedures to be followed when a cyber threat or security incident occurs. This plan details the steps to detect, respond to,...
0
0
0
Australia recently passed two pieces of legislation designed to bolster security and privacy by protecting personal data in the country. Catch up on the news in this new Fortra Data Classification blog:
dataclassification.fortra.com
0
0
0