Robin
@D4mianWayne
Followers
519
Following
2K
Media
16
Statuses
250
Wannabe pwner! Founder @PwnFuzz | CTFs @shellphish
Batcave, Gotham
Joined May 2019
Our fuzzer generated entirely by Vibing just found it first ( confirmed! ) 0day in Firefox. CVE and details soon!
10
86
711
Teaming with @gh0stbyt3, we built DiffRays for headless IDA (@HexRaysSA) decompilation. It stores decompiled code in a SQLite DB and provides a Web UI for diffing between the stored functions. Built for vuln research. https://t.co/U6RzM3XcXk
#pwnfuzz
5
39
132
This is absolute good, as an individual researcher, one wouldn't normally think of setting up the a honeypot and monitor it, spent around 3 nights to came up with exploit only to be outsmarted, this is absolute great! Awesome work as usual!
"Teach a hacker to find vulnerabilities, and they might find a couple. Teach a hacker to steal warez from another idiot, and they will feast for eternity" Enjoy our analysis of CrushFTP's CVE-2025-54309, fueled by watchTowr's Attacker Eye https://t.co/G2lHM4ASpd
0
0
7
We have reproduced "ToolShell", the unauthenticated exploit chain for CVE-2025-49706 + CVE-2025-49704 used by @_l0gg to pop SharePoint at #Pwn2Own Berlin 2025, it's really just one request! Kudos to @mwulftange
9
162
644
My Sitecore CMS pre-auth RCE chain blog is public now. Enjoy 🫡
With the help of the Sesame Street gang, watchTowr Labs is back - with a pre-auth RCE chain against Sitecore Experience Platform that we discovered and reported in February this year. Enjoy..... https://t.co/1ii0LQPCPw
6
20
110
I made this tool that checks if drivers from https://t.co/QABNdVCnBU are blocked by HVCI. It helps identify vulnerable drivers not blocked by Windows Hypervisor Code Integrity policy to find suitable BYOVD candidates. Tool: https://t.co/57NDRuKiby
#BYOVD #HVCI #Cybersecurity
0
8
16
Never assume you've understood a bug report correctly unless you've written a PoC for it (or an exploit if one is present). You'll be surprised to catch your slightest misunderstanding of a verbal description of an issue and it'll make you question your ability to read.
3
6
54
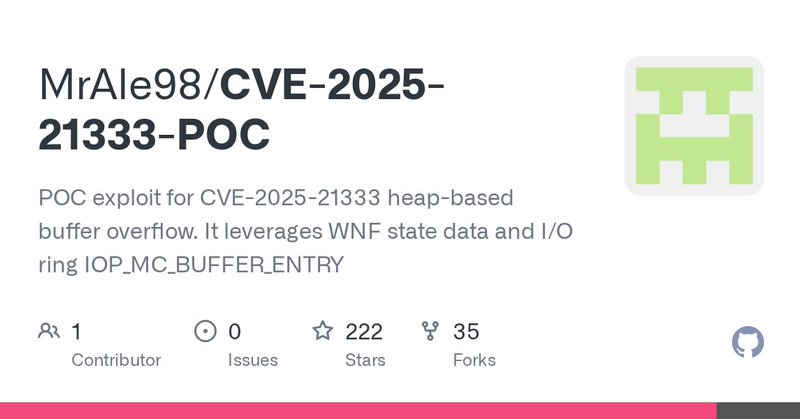
Developed an exploit for CVE-2025-21333 (quite unreliable): vulnerability in vkrnlintvsp.sys. Exploit code: https://t.co/PU1ZYSefnJ Exploits a paged pool overflow overwriting a _IOP_MC_BUFFER_ENTRY*. Hope you find it useful in case not already shown🙂.
github.com
POC exploit for CVE-2025-21333 heap-based buffer overflow. It leverages WNF state data and I/O ring IOP_MC_BUFFER_ENTRY - MrAle98/CVE-2025-21333-POC
9
104
380
0x0 - Windows Driver 101 - https://t.co/QQBRbTnwQP 0x1 - Setup & Reversing - https://t.co/eeONmyJAUj 0x2 - SMEP & kASLR & VBS - https://t.co/gCeVED3kpO 0x3 - VBS & HVCI - https://t.co/434waY8CxS
#windows #cybersecurity #kernel #redteam
0
2
6
Starting 2025 strong! We’ve developed a PoC exploit for CVE-2024-49112. Read the blog and check out the GitHub repo: https://t.co/hd9qI2vm6o Just the beginning of the great things SafeBreach will deliver this year; stay informed at https://t.co/1wVKwuwM6Z.
#CTEM #whatisPropagate
safebreach.com
SafeBreach provides the leading exposure validation platform, combining breach and attack simulation with attack path validation.
1
44
122
In his latest blog, @chudyPB covers a pre-auth Arbitrary File Deletion vulnerability he discovered in the SolarWinds Access Rights Manager (ARM). It may not sound exciting, but it can lead to an LPE on domain-joined Windows machines. Read the details at
zerodayinitiative.com
Some time ago, I spent some time researching a core SolarWinds product, SolarWinds Platform (previously Orion Platform). At that time, I hadn’t been aware of the SolarWinds Access Right Manager...
2
21
55
New blog post on exploiting XXE in Ivanti Endpoint Manager (CVE-2024-37397)! No more hardcoded values—chained an API method to fetch the required ID. Full details here: https://t.co/jFzfWtVOlf
#Infosec #XXE #CVE202437397 #BugBounty #AppSec
old.pwnfuzz.com
This blog provides an in-depth analysis of the exploitation process for an unauthenticated XXE vulnerability in Ivanti Endpoint Manager, identified as CVE-2024-37397. Uncovering the ImportXml...
With all the buzz around Ivanti EPM CVEs, here’s my take on the unauthenticated XXE (CVE-2024-37397): https://t.co/AukrILqyLM. Vulnerability Credit: 06fe5fd2bc53027c4a3b7e395af0b850e7b8a044 (Trend Micro). Stay tuned for the blog post! #CVE #Ivanti #Security
2
29
123
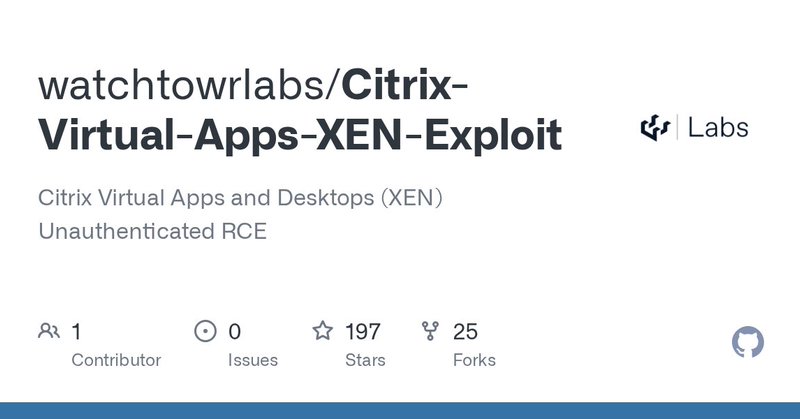
we heard Citrix marked this as a CVSS 5.1 - ok then https://t.co/j5AuVEWYRJ
github.com
Citrix Virtual Apps and Desktops (XEN) Unauthenticated RCE - watchtowrlabs/Citrix-Virtual-Apps-XEN-Exploit
4
70
161
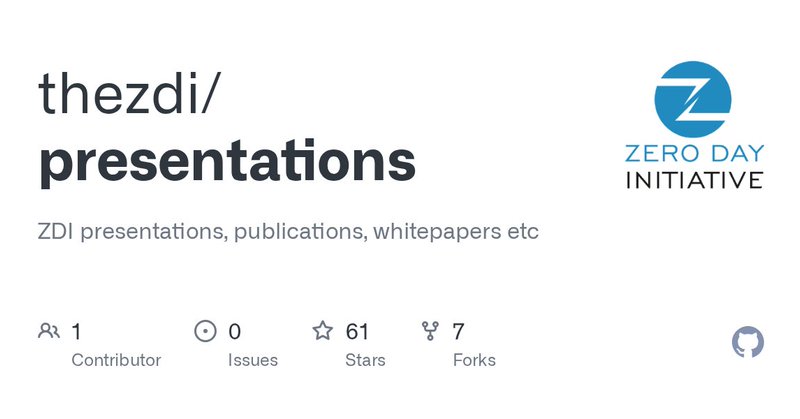
My WarCon slides about Ivanti Avalanche are public! I tried to do some mapping of the attack-surface, show the new auth mechanism and present some research ideas (things I didn't try). It also shows my first-ever fuzzing and memory corruption experience😆 https://t.co/FBeKGI16nJ
github.com
ZDI presentations, publications, whitepapers etc. Contribute to thezdi/presentations development by creating an account on GitHub.
1
41
149
I was just laid off at Hi-Rez today. I'm thankful for all the time I spent, the people I worked with, and the games I worked on. If anyone is looking for a gameplay programmer... I'm you're guy.
10
47
350
Blog about my @PwnieAwards nominated Exchange RCE gadget chain dropped: 1) File Write to drop DLL to unknown directory and leak this path to log file. 2) File Read to leak write location from the log file. 3) Local DLL loading gadget -> RCE It was a fun process 🥲
In part 3 of his series on exploiting #Exchange #Powershell after ProxyNotShell, ZDI researcher @chudyPB chains 3 bugs that lead to RCE, mainly by abusing the single-argument constructor conversions. Read the details at
2
42
169
With all the buzz around Ivanti EPM CVEs, here’s my take on the unauthenticated XXE (CVE-2024-37397): https://t.co/AukrILqyLM. Vulnerability Credit: 06fe5fd2bc53027c4a3b7e395af0b850e7b8a044 (Trend Micro). Stay tuned for the blog post! #CVE #Ivanti #Security
0
2
15
I examined the mySCADA myPRO Hard-Coded Credentials RCE Vulnerability - CVE-2024-4708. The hardcoded password is "brumla". Kudos to Nassim Asrir (Trend Micro) for discovering this. Not sure about the RCE exploit vector yet.
0
0
6