CommandK
@CommandKDev
Followers
116
Following
18
Media
2
Statuses
51
Secret Management best practices to stay compliant, enhance security, and improve developer productivity. All out of the box. Know more at https://t.co/ak1NMccROp
Mumbai/Bengaluru/San Francisco
Joined June 2022
A fantastic security founders event in the bay area today with @LightspeedIndia @descopeinc @CommandKDev @EndorLabs & @scrutsocial! Massive turnout, full of great conversations. Security is an evergreen area of investment for us and it's been great to see our india & US
1
5
36
🔐 Elevate Your Kubernetes Security 🔐 Learn to protect your data with best practices. From RBAC and secret encryption to automated rotation. Manage sensitive data, network policies & advanced secret solutions. Full guide:
0
4
8
Many founders fr India visiting SF Bay Area in Sept, excited to meet you at @saasboomi Caravan, @SaaStrAnnual! Since last yr, we've partnered w many new India/SEA->US founders incl @supabase, @PortkeyAI, @zluri_hq, @thenaplatform, @ZipstackHQ, @CommandKDev, @scrutsocial, others.
0
7
34
In our latest blog post, we explore the ins and outs of Kubernetes Secrets. Check it out here:
0
1
2
🔐 Kubernetes Secrets offer a way to keep your critical information separate from your app's code and config, minimizing the risk of exposure or unauthorized access. They're essential for airtight containerization and orchestration.
2
4
3
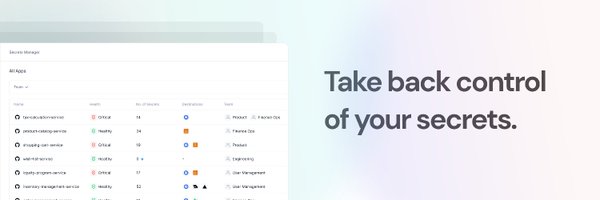
At CommandK, we're reshaping how you secure and manage your secrets. We have already enabled large organizations to regain control of their secrets – in under 5 minutes.
0
0
0
We are thrilled to share that CSO Online has recognized CommandK as one of the cybersecurity companies to watch for. Read more on the blog: https://t.co/HLlwL3FrR3.
csoonline.com
These startups are jumping in where most established security vendors have yet to go.
1
6
13
.@CommandKDev is building one of the world's smartest command centers for better enterprise security posture (secrets, api keys, configs & more). If you're a fast growing US enterprise, DM me; I'll intro you to the founders for early access. Cc @JayeshSidhwani @LightspeedIndia
There are so many incidents of data breaches. and if we are honest, there's not enough time to build all the safeguards that you really need! So what's the 80/20 you can do to prevent data breaches? Periodic Auditing. But you've got to do it the right way. Read our thoughts
0
4
14
Read our latest blog on how to audit your secrets correctly! Do you have any experiences to share?
There are so many incidents of data breaches. and if we are honest, there's not enough time to build all the safeguards that you really need! So what's the 80/20 you can do to prevent data breaches? Periodic Auditing. But you've got to do it the right way. Read our thoughts
0
0
1
just got a demo of what @JayeshSidhwani is building to solve this at @CommandKDev 👀 got onboarded and was good to go in 5 minutes. Engg leaders and managers should ping him asap to solve credentials management for your product
0
14
23
If this sounds exciting, check out the Interview Process and apply here: https://t.co/v8aZPVAnBw.
1
1
3
Hiring 🚨: We're looking for a stellar Technical Content Writer! 💻🌟
7
13
24
Software architecture has become exponentially complex with 100s of integration points, but the way we handle secrets hasn't evolved with it. We think the only way to solve it is to rethink secret management at all points in the stack. How? Link in the next tweet
1
1
1
What do Uber, Heroku, and Capital One have in common? They lost millions of $$ in the last 2 years due to data breaches How could this happen at a place with such competent engineering teams? We think we know the answer (hint: it's not their fault)
1
12
29
👋 Have you implemented a BYOK strategy at your organization? We’d love to hear your thoughts. #BYOK #DataSecurity #Encryption #KeyManagement #CloudSecurity
0
0
0
🔄 Key rotation is a manual exercise, potentially causing operational hassles in rotating the key & re-encrypting existing data.
1
0
0
🔓 Most CSP KMSs only support symmetric encryption strategies for BYOK.
1
0
0
BYOK is merely a strategy that facilitates the successful implementation of sensitive data management. While the CSPs KMS simplify the adoption of BYOK, they do have some caveats to be aware of:
1
0
0
🌍 Geo-Localization of data: As discussed earlier, the strategy facilitates the implementation of data localization guidelines.
1
0
0