Bertrand Yangni
@CodedBlues
Followers
234
Following
22K
Media
3
Statuses
623
Zionite | Tech Fanatic 🇬🇧| Chelsea FC Fan
London , England - UK
Joined January 2022
@reggiejohnson86 It depends on what you do but the core of DevOps engineering is building CI/CD pipelines and being able to use IaC. If not then you aren't there yet.
2
0
7
AFCON needs more respect… ✊🏽 It matters & federations need to do more to highlight this. Ask the likes of Mo Salah, Didier Drogba, Yaya Toure, Abedi Pele, Samuel Eto'o what it means…. #AFCON
2K
14K
62K
If you’re new to programming or want to get started with Python, Cohort 2 of my FREE beginner-friendly python programming course is here. 💻 100% virtual 🌍 Open to anyone, anywhere 🗓 Limited spots - so grab yours fast! Sign up here: https://t.co/MUDhjExflg
2
53
51
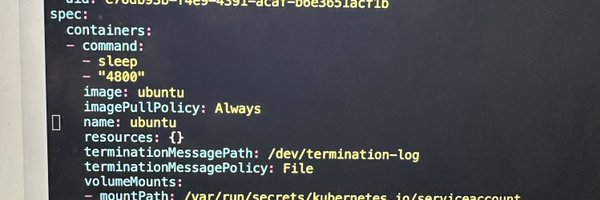
Resource abuse is a challenging problem in Kubernetes. Happens often with people who are new to Kubernetes. Here's how to handle.
2
9
68
CrowdStrike is actively working with customers impacted by a defect found in a single content update for Windows hosts. Mac and Linux hosts are not impacted. This is not a security incident or cyberattack. The issue has been identified, isolated and a fix has been deployed. We
4K
6K
21K
You're in an interview, and the interviewer asks, "What are your strengths and weaknesses as a developer?" Here is how you can answer:
4
61
424
This is a very useful Kubernetes tip. Trust me. I just found a tool that can help you tail multiple Kubernetes pod logs at once. It's called stern. For example, if you have a nginx deployment with 5 replicas. Just use the following command to get the logs of all 5 nginx pods at
7
47
216
SRE vs DevOps vs Cloud Engineering vs Platform Engineering What is unique in terms actual role?
1
33
174
Docker best practice: Don't store secrets in Docker images. You can rather inject them: - as environment variables - as build arguments - with orchestration tools such as Docker Swarm or Kubernetes 👇
2
17
119
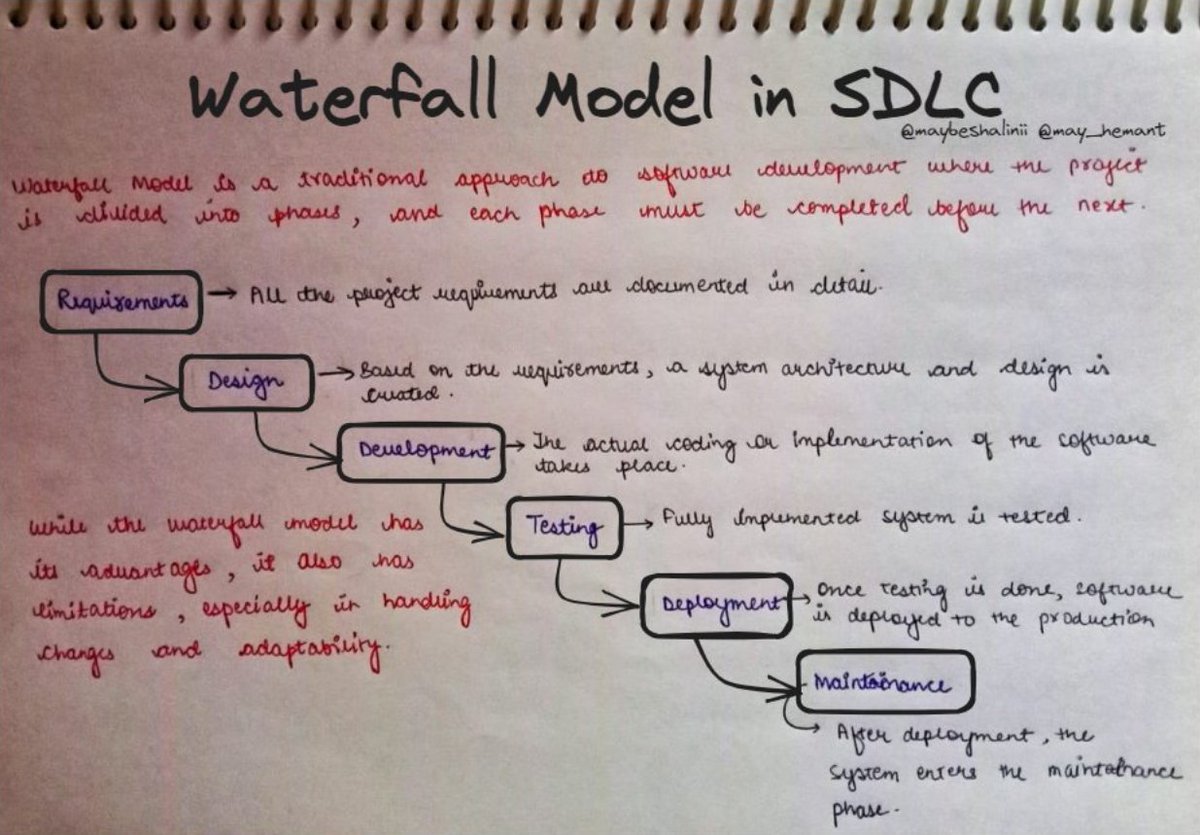
Waterfall Model explained: The Waterfall Model is like building software in a step-by-step manner, where each step is like a phase in a sequence. Phases of the Waterfall: - Requirements: First, you figure out and write down exactly what the customer wants. It's like making a
11
110
586
JavaScript for Everything: JavaScript + Three.js = 3D Visualization JavaScript + React = Web Development JavaScript + Angular = Web Applications JavaScript + Phaser = Game Development JavaScript + Vue.js = Progressive Web Apps JavaScript + TensorFlow.js = Machine Learning
75
543
3K
Day 8 of #60daysofMERN 🚀 Topics Covered: - CSS Z-Index - Pseudo Class - Cursor Properties CSS Z-index CSS z-index is a property that controls the stacking order of elements on a web page. Here's a simple way to understand it: - Stacking Order: Think of your web page as a
4
47
196
Day 6 of 60daysofMERN Topics Covered: - CSS Box Model - CSS Fonts CSS Box Model The CSS Box Model is a fundamental concept in web design and development that dictates how elements are structured and displayed on a web page. Components of the CSS Box Model 1. Content - The
13
40
178
Day 5 of #60daysofMERN 🚀 Topics Covered: - CSS Comments - CSS Colors - CSS background properties - CSS Border properties CSS Comments /* This is a comment */ CSS Colors Colors in CSS can be defined by either rgb, hex or hsl values. CSS Background Properties These properties
3
44
241
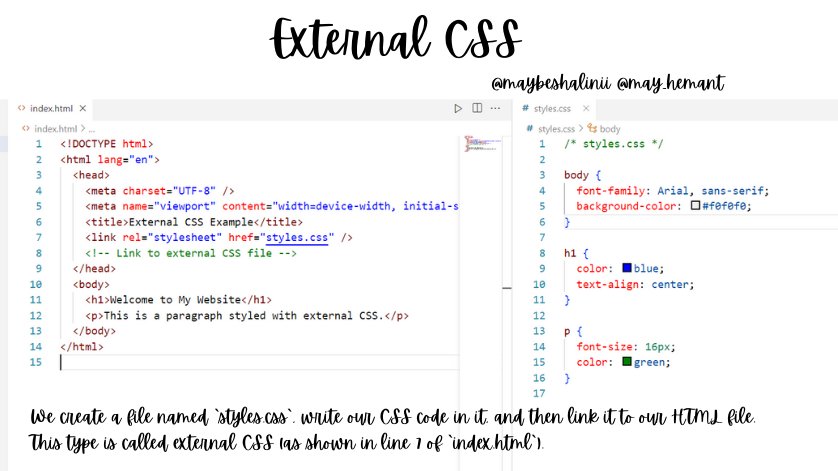
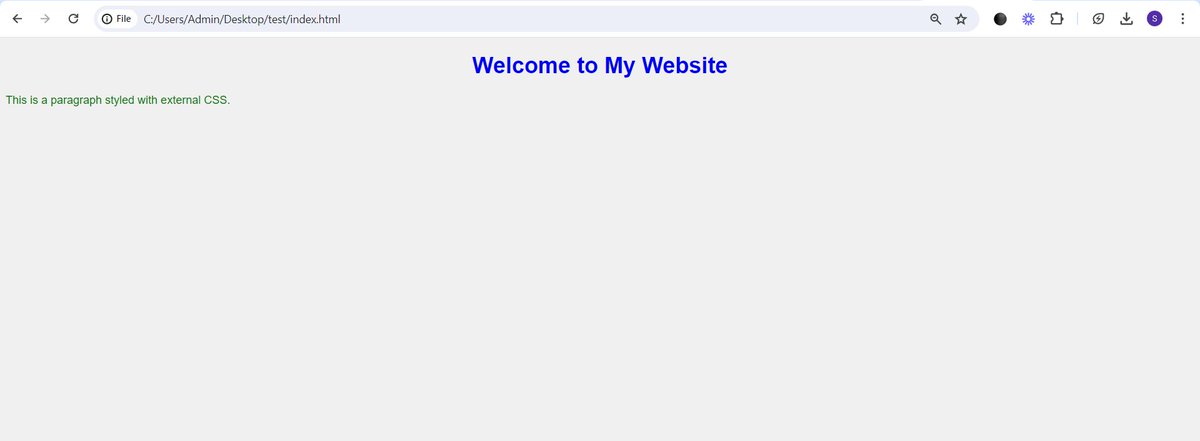
Day 4 of #60daysofMERN 🚀 Topics Covered: - CSS Introduction - Linking an external Style sheet. - CSS Syntax What is CSS? CSS refers to Cascading Style Sheets. It is used for styling our HTML. Why Use CSS? 1. Separation of Concerns: CSS allows you to separate the content
6
53
254
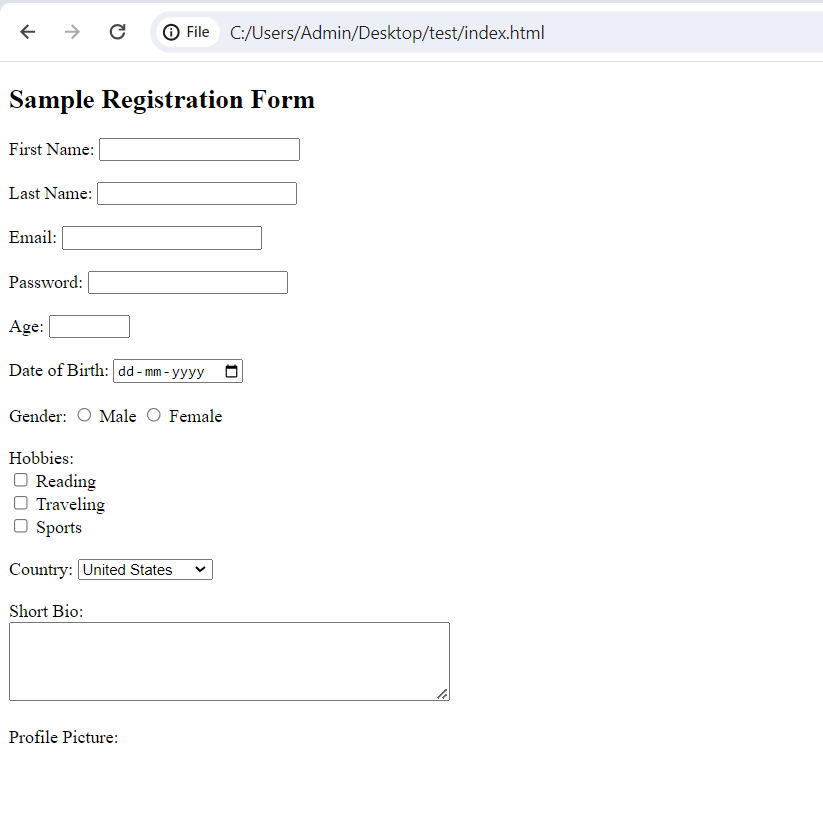
Day 3 of #60daysofMERN 🚀 Topics Covered: - HTML Forms - How to link CSS to our HTML File A form is created using the <form> element, which acts as a container for various input elements. The basic structure of a form includes attributes like action and method that specify how
4
54
315
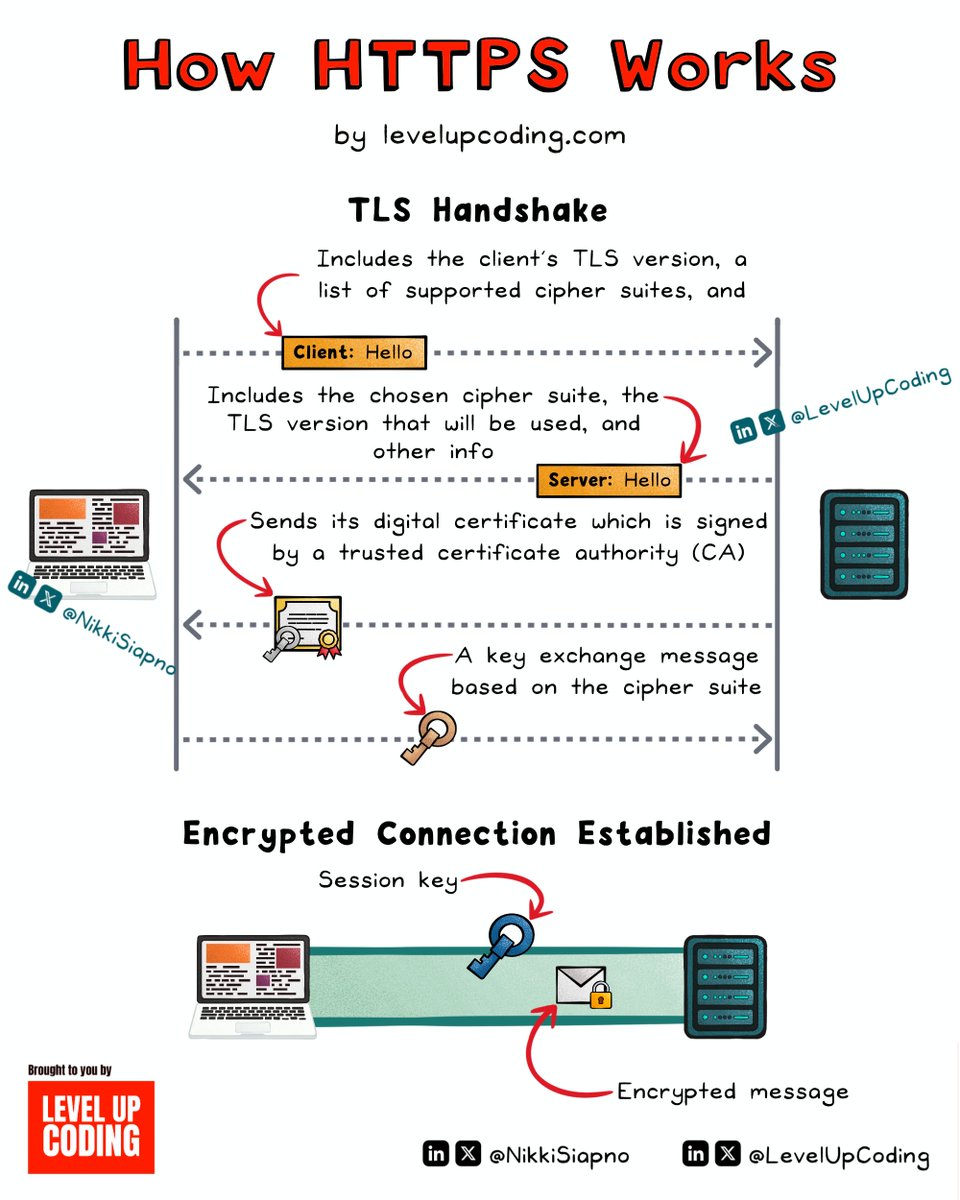
HTTPS explained in simple terms. Online communication relies on trust and confidentiality. Here's where HTTPS is invaluable. HTTPS, the secure version of HTTP, is fundamental for web security. It encrypts data in transit to ensure its security and privacy, helping to prevent
9
117
581
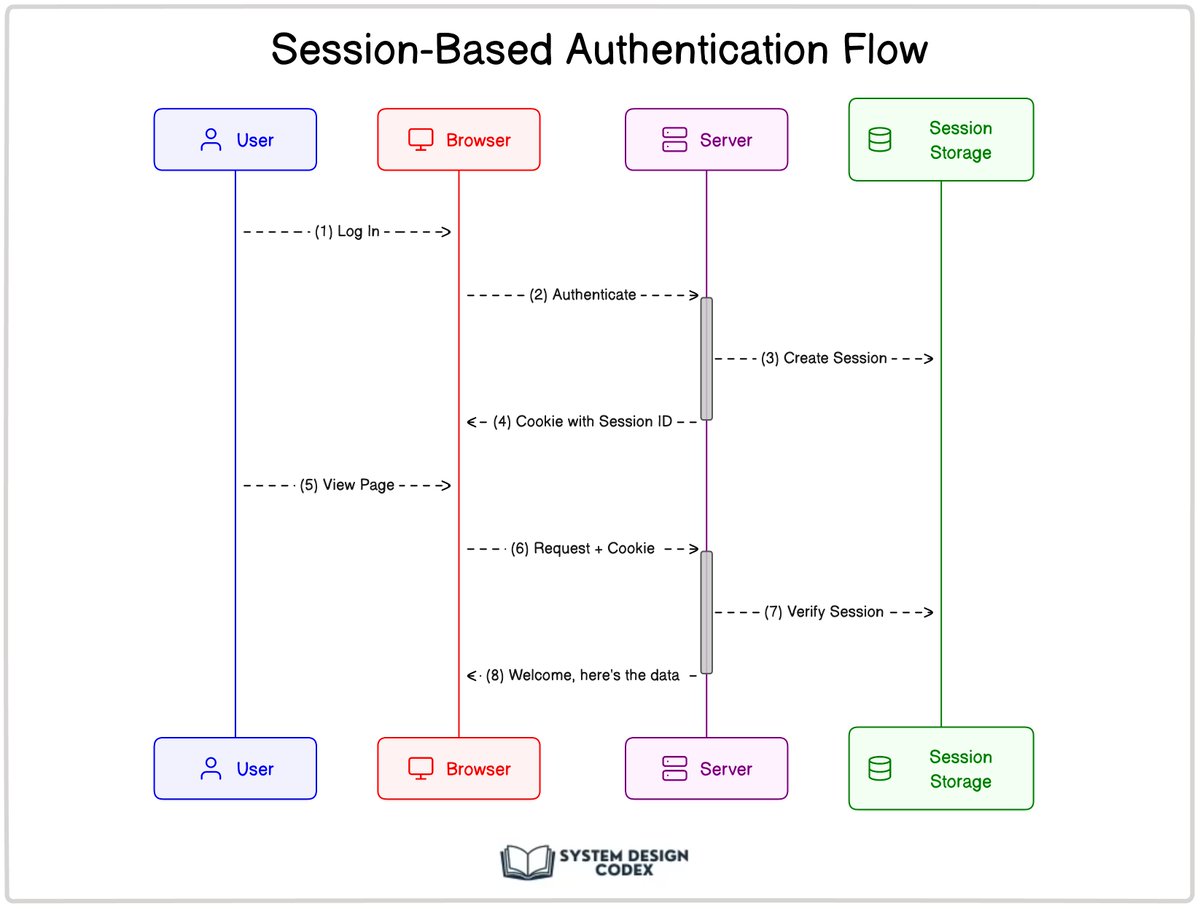
𝗛𝗧𝗧𝗣 𝗶𝘀 𝗮 𝘀𝘁𝗮𝘁𝗲𝗹𝗲𝘀𝘀 𝗽𝗿𝗼𝘁𝗼𝗰𝗼𝗹. This means every request is independent. The web application server can’t tell if two requests came from the same browser or user. But the users aren’t stateless. No one wants to log in to your application every time they
8
72
334
As a DevOps Engineer, you might be asked: How do you build a robust CI/CD pipeline? Let’s explore the key components, best practices, and essential tools to create an effective CI/CD pipeline. A thread 🧵
8
142
702
Back-end developer: ∟📂 Server-side programming (Python,Java,PHP, NodeJs,Go,Rust) ∟📂 Databases (SQL, NoSQL) ∟📂 APIs and web services ∟📂 Security and authentication ∟📂 Caching and performance tuning ∟📂 Scalability and load balancing ∟📂 Deployment and DevOps ∟📂
64
222
984