Breachkey
@BreachKey
Followers
261
Following
146
Media
3
Statuses
202
Joined February 2020
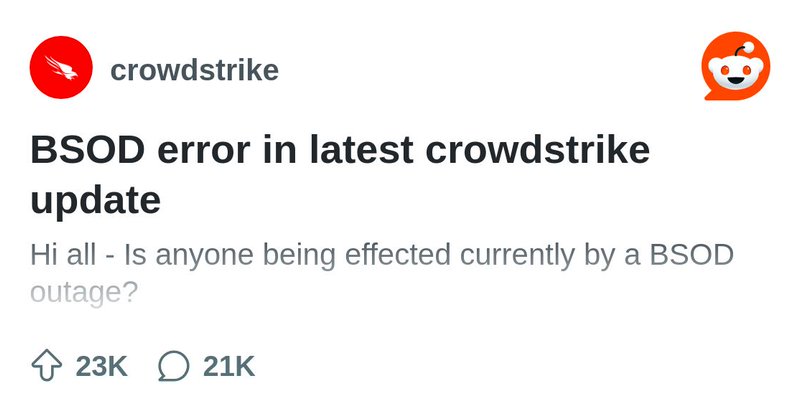
CrowdStrike Falcon agents are imploding right now and causing a Blue Screen of Death boot loop on every endpoint. Reports of massive outages globally. https://t.co/cS9Zt4SagH
reddit.com
Explore this post and more from the crowdstrike community
71
1K
4K
The #FBI released a joint Cybersecurity Advisory detailing the tactics and indicators of compromise related to BianLian, a ransomware developer, deployer, and data extortion cyber criminal group. Read more to help protect your networks: https://t.co/3KYRUDreBw
#StopRansomware
118
108
246
🌐@CISAgov and @DHSgov are working with @NIST to prepare for the launch of a new cryptographic standard to protect against future quantum-based threats. Learn more about this effort and read https://t.co/xA1670mnoQ
#Cryptograpy #Cybersecurity #IT #Quantum #Technology
3
47
85
NEW #DFIR Course | COMING SOON Authored by Sean O'Connor (@vHUMINT) & @thegrugq #FOR589 #DarkWeb #ThreatHunting & #BlockchainForensics teaches to hunt #DarkWebIntelligence, investigate illicit #Blockchain & analyze #Cryptocurrency evidence 👉 https://t.co/dvChjmHMTu
3
19
51
Lapsus$ member? (based on the bookmarks in the screenshot) #opsecfail
https://t.co/3oMPkPAu7a
13
39
161
15 members of REvil has been arrested by the Russian authorities. REvil, once dubbed the "Crown prince of Ransomware", was responsible for the Kaseya supply chain attack, and many other high-profile breaches. Footage courtesy of the FSB.
34
707
2K
An incoming blog detailing the short synpo[psis behind Emotet return...."Corporate Loader "Emotet": History of "X" Project Return for Ransomware"
0
5
20
1
39
98
Diving Deep into UNC1151’s Infrastructure: Ghostwriter and beyond | https://t.co/DqBI9vxZki
@prevailion
1
5
25
Alright, folks, let's talk about Cobalt Strike! https://t.co/v2gmWXp5CO (Sorry, red team pals. This one is for my defense buddies!) 🧵
12
227
603
Just found a new potential #MirrorBlast #TA505 domain: - int-onedrive[.]com Fun fact: In 12 of 200 documented TA505 domains used for their Get2/SDBBot campaigns between September 2019 and Decmeber 2020, they used the keyword "onedrive".
2
21
58
[ALERT] DESORDEN GROUP claimed to have hacked ACER INDIA SERVERS.
1
29
58
DETECTION OPP: We’re seeing increased Qbot activity, including new TTPs that we haven’t previously associated with this threat. While we haven’t observed the ultimate payload delivered by Qbot, this trend is concerning given that Qbot is often a precursor to Conti ransomware. 1/6
1
83
235
If you have deployed Microsoft Defender for Endpoint this is the guide for you.
0
9
33
NEW BLOG POST!! In this blog post, I have shared my experience with the NEW CVE-2021-40444. https://t.co/eMDWrotILW
#redteam #infosec #CyberSecurity #CVE
6
176
353
'According to Mujahid, the only Taliban promise is that it will not let anyone use the Afghan soil against the U.S. and its allies. However, two reasons leave few doubts about whether al-Qaeda will again use Afghanistan in the future (...)' https://t.co/7TJBkLAboG
0
1
1
Yes, it's back! Your weekly overview of OSINT related topics in Week in #OSINT! H/T: @kirbstr @aware_online @LorandBodo @LogicallyAI @brechtcastel
https://t.co/i3IHkoMTzV
sector035.nl
After some time off, it's time again for your weekly dose of OSINT! This time I've got topics ranging from handy searches, to extr
5
48
127