Andrew Lock "Sock"
@andrewlocknet
Followers
16K
Following
3K
Media
136
Statuses
6K
Microsoft MVP and blogger, focused on ASP.NET Core. Author of ASP.NET Core in Action: https://t.co/GTRJ4hBm9s @[email protected] @andrewkock.bsky.social
Plymouth, England
Joined May 2016
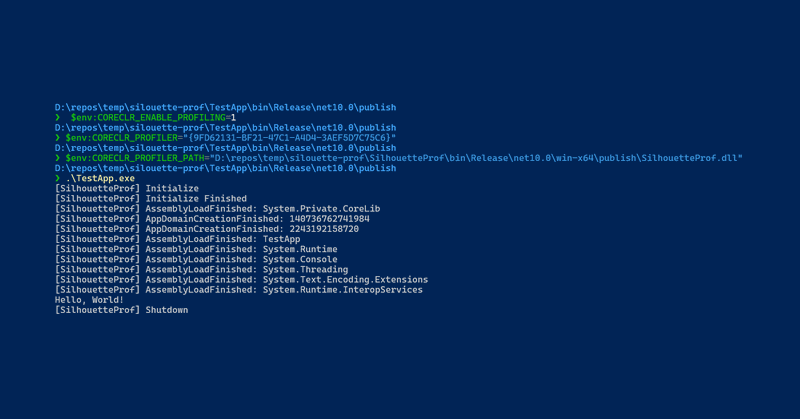
Blogged: Creating a .NET CLR profiler using C# and NativeAOT with Silhouette https://t.co/EB1diuVEcA In this post I look at how to create a simple .NET profiler. But instead of using C++, the profiler uses C# and NativeAOT with @KooKiz's Silhouette library #dotnet
andrewlock.net
In this post I look at how to create a simple .NET profiler. But instead of using C++, the profiler uses C# and NativeAOT with the Silhouette library
0
11
54
Blogged: Trying out the Zed editor on Windows for .NET and Markdown https://t.co/Xz7hLBgjJO In this post I try out Zed on Windows to see if it can replace my VS Code usages for quick edits of .NET projects and writing Markdown documents. #dotnet
andrewlock.net
In this post I try out Zed on Windows to see if it can replace my VS Code usages for quick edits of .NET projects and writing Markdown documents
9
8
87
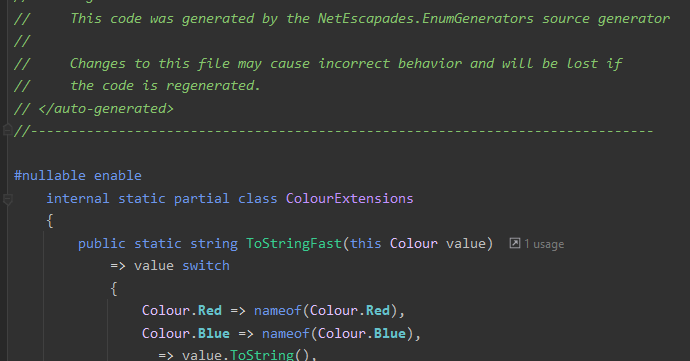
Blogged: Recent updates to NetEscapades.EnumGenerators: [EnumMember] support, analyzers, and bug fixes https://t.co/uB7L6AfKFM In this post I describe recent changes to the NetEscapades.EnumGenerators source generator, including [EnumMember] support and new analyzers #dotnet
andrewlock.net
In this post I describe some recent changes to the NetEscapades.EnumGenerators source generator, including support for [EnumMember] and new analyzers
0
2
13
New issue of .NET R&D Digest is here! Thanks to @unmeshjoshi, @doctorow, @abhi9u, @Scooletz, @andrewlocknet, @AntonMartyniuk, @meziantou, @shanselman and other great and talented authors for making amazing content! https://t.co/RM5MnDUzUP
#dotnet
olegkarasik.wordpress.com
This issue includes bits of AI, software development, performance, licensing, security, philosophy, something to watch and of course .NET and .NET Internals.
0
4
16
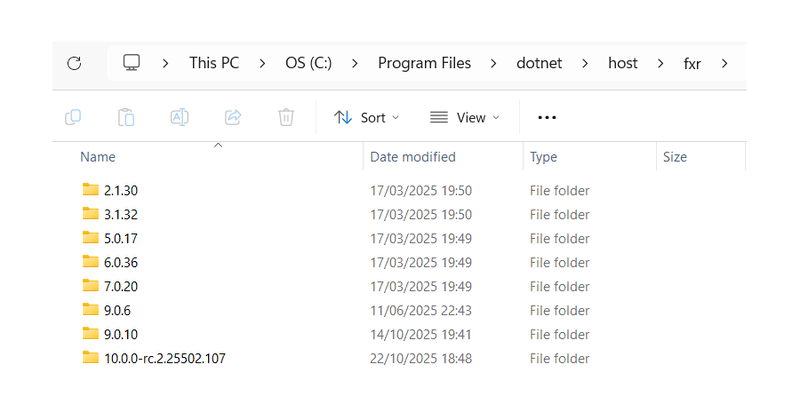
Blogged: Exploring the .NET boot process via host tracing https://t.co/TQ9RhUuCTd In this post we enable host tracing and use that to understand how a .NET app boots up via the dotnet muxer, hostfxr, and hostpolicy.dll #dotnet
andrewlock.net
In this post we enable host tracing and use that to understand how a .NET app boots up via the dotnet muxer, hostfxr, and hostpolicy.dll
2
14
73
To watch full episodes of Secret America - check us out - Follow: @secretamericatv OR Visit: secretamericalive("dot")com
3
61
63
Snyk is referencing CVE-2025-55315-repro (and @andrewlocknet's blog) in their vulnerability database entry for CVE-2025-55315
1
1
4
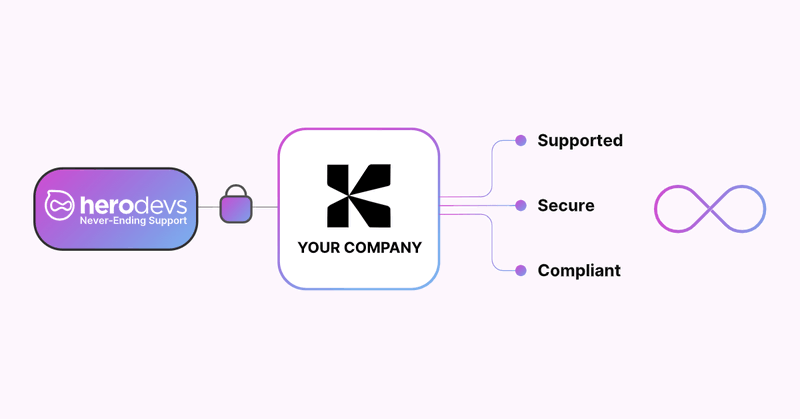
Blog about the .NET support lifecycle, post-EOL support, and how other ecosystems do it from @andrewlocknet
andrewlock.net
In this post I describe a solution to .NET "releasing too quickly": just pay for support of older versions, such as HeroDevs' Never Ending Support for .NET 6
0
2
4
A lot of .NET teams blame Microsoft for “moving too fast.” This post explains why that’s not really the problem. 👇 @andrewlocknet breaks down how support windows work, why upgrades can be brutal for large orgs, and what actually happens when a 9.9 CVE hits an out-of-support
1
4
10
Blogged: Companies complaining .NET moves too fast should just pay for post-EOL support https://t.co/LdOBBoIbs2 In this post I describe a solution to .NET "releasing too quickly": just pay for support of older versions, such as HeroDevs' Never Ending Support for .NET 6 #dotnet
andrewlock.net
In this post I describe a solution to .NET "releasing too quickly": just pay for support of older versions, such as HeroDevs' Never Ending Support for .NET 6
5
3
30
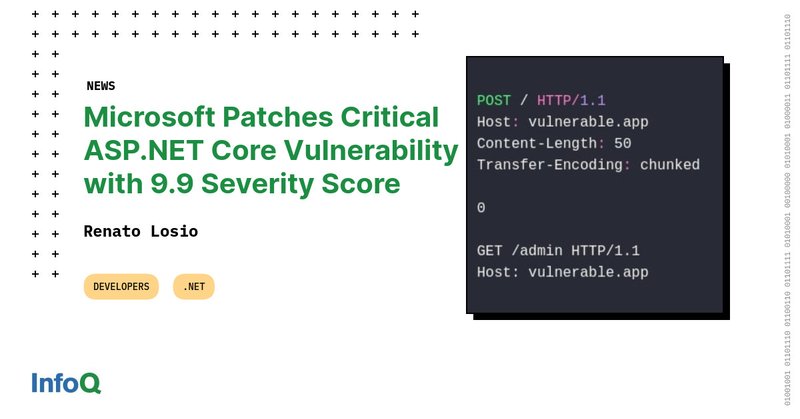
Nice writeup in @InfoQ about CVE-2025-55315, quoting @andrewlocknet and a link to my repro tool
infoq.com
Microsoft recently released a security advisory and patched a critical vulnerability in ASP.NET Core that allows an attacker to bypass a security feature over a network due to an inconsistent...
0
1
2
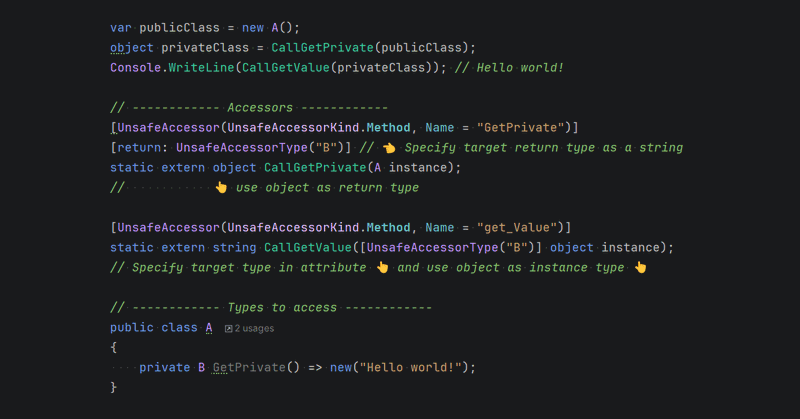
Easier Reflection with [UnsafeAccessorType] in .NET 10 - https://t.co/nm7JpJndaF
@andrewlocknet
andrewlock.net
In this post I show how to work with [UnsafeAccessor] to do 'easier' reflection and how to use .NET 10's [UnsafeAccessorType] with types you can't reference
1
6
42
Given the port from Disqus to Gisqus worked so well for my personal website (thanks to @andrewlocknet! 🙏), I've just done the same for the podcast! A good time to go and comment on your favorite episodes! 😊 https://t.co/Z2K6QWOu4I
unhandledexceptionpodcast.com
Software Development podcast hosted by Dan Clarke
As part of this, I added Giscus for comments instead of Disqus that I was previously using. I haven't ported the old comments yet though. Just Googled it and found this post (and migration tool!) by @andrewlocknet! Andrew - you're a star!!! 🙏⭐ https://t.co/KC2EVXiEjf
0
1
2
Blogged: Easier reflection with [UnsafeAccessorType] in .NET 10 https://t.co/XjeaVgAIsP In this post I show how to work with [UnsafeAccessor] to do 'easier' reflection and how to use .NET 10's [UnsafeAccessorType] with types you can't reference at compile time #dotnet
andrewlock.net
In this post I show how to work with [UnsafeAccessor] to do 'easier' reflection and how to use .NET 10's [UnsafeAccessorType] with types you can't reference
4
7
77
New issue of .NET R&D Digest is here! Thanks to @lemire, @ryanjfleury, @andrewlocknet, @KooKiz, @maoni0, @Scooletz, @thomaslevesque, @meziantou, @STeplyakov, @zodiacon and other great and talented authors for making amazing content! https://t.co/rL9iRsLPjb
#dotnet
olegkarasik.wordpress.com
This issue includes bits of computer science, AI, software development, parallelism, security, C#, .NET and of course some of .NET Internals.
0
9
22
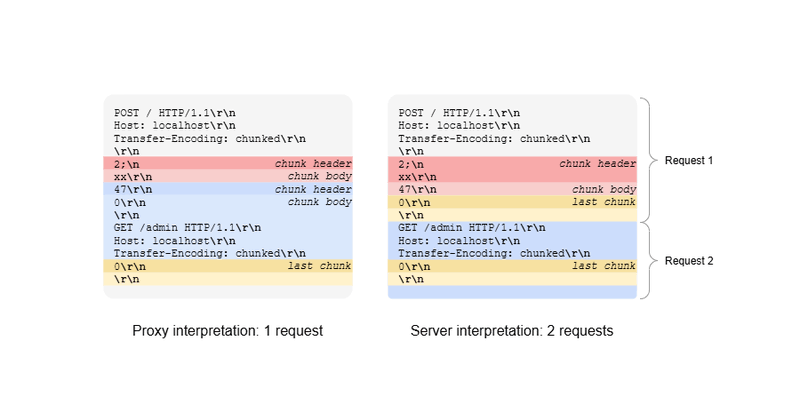
Understanding the worst .NET vulnerability ever: request smuggling and CVE-2025-55315 by @andrewlocknet
https://t.co/BWyB1VTuYB
#aspnetcore
0
8
32
@schneidenbach @andrewlocknet Special Andrew Lock shoutout in my latest vid, as promised
1
2
9
Cracking blog post from @andrewlocknet explaining the 9.9 Request Smuggling issue in .NET from last week, way better than my video This blog post should have come from the .NET Security team IMO. It’s wild that volunteers have to do this. https://t.co/H4CLqdGlfg
andrewlock.net
In this post I discuss request smuggling, the recent vulnerability in ASP.NET Core with a severity score of 9.9, and how attackers could exploit it
2
12
80
This post links to a deep analysis discussion of the .NET security vulnerability (rated 9.9) - CVE-2025-55315. Best description of the issue that I've seen so far.
Blogged: Understanding the worst .NET vulnerability ever: request smuggling and CVE-2025-55315 https://t.co/89TCJvjnNF In this post I discuss request smuggling, the recent vulnerability in #AspNetCore with a severity score of 9.9, and how attackers could exploit it #dotnet
0
1
6
Blogged: Understanding the worst .NET vulnerability ever: request smuggling and CVE-2025-55315 https://t.co/89TCJvjnNF In this post I discuss request smuggling, the recent vulnerability in #AspNetCore with a severity score of 9.9, and how attackers could exploit it #dotnet
andrewlock.net
In this post I discuss request smuggling, the recent vulnerability in ASP.NET Core with a severity score of 9.9, and how attackers could exploit it
1
31
181
Great analysis of CVE-2025-55315 "the worst .NET vulnerability ever" by @andrewlocknet
andrewlock.net
In this post I discuss request smuggling, the recent vulnerability in ASP.NET Core with a severity score of 9.9, and how attackers could exploit it
0
1
6