Amitai Cohen 🎗️🤟
@AmitaiCo
Followers
2K
Following
8K
Media
111
Statuses
1K
✦ researching threats @wiz_io 🐞 maintaining vulns @cloudvulndb 🎙️ casting pods @ https://t.co/9Jsah9BjbO
Tel Aviv, Israel
Joined August 2011
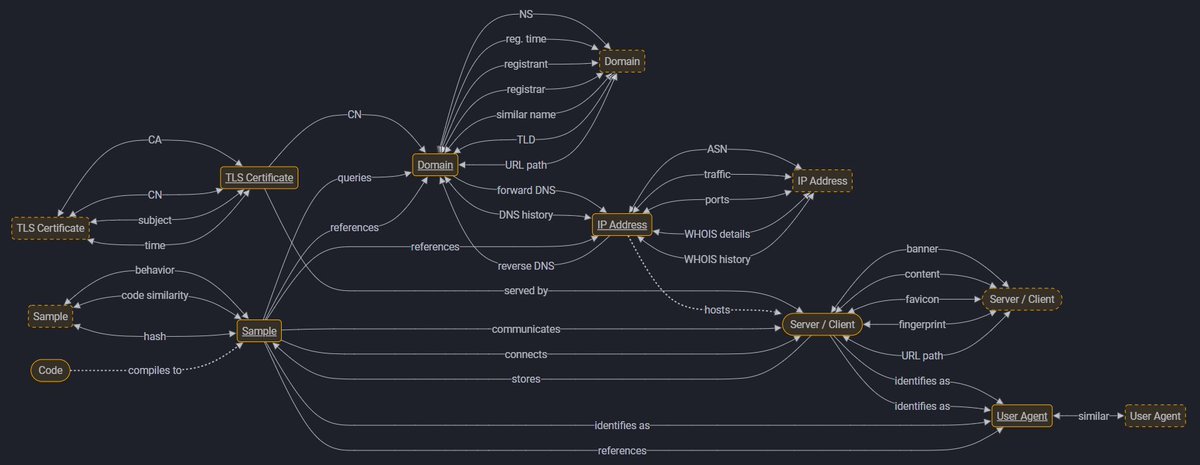
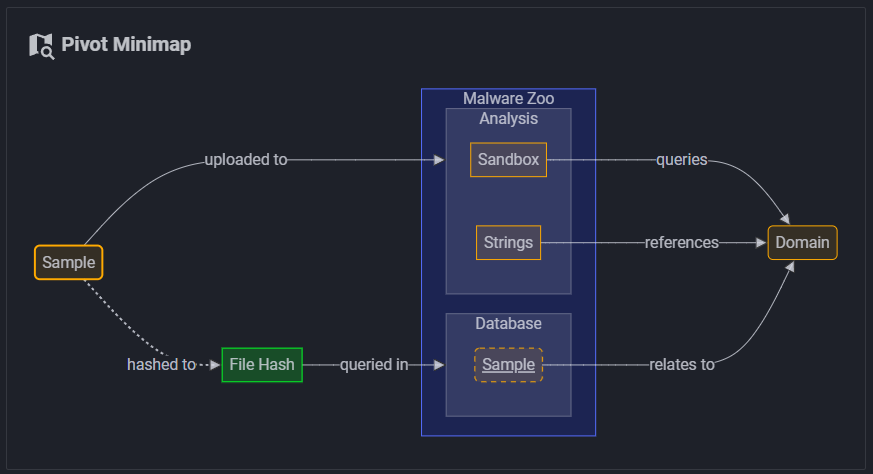
Happy to introduce "Pivot Atlas", a digital pivoting handbook for cyber threat intel analysts. I've been working on this as a personal project with the goal of graphing the "pivotability" of threat intel artifacts and providing real-world examples and reference material. (1/2)🧵
12
85
319
Very curious to see how this plays out but I'm optimistic - while there's a risk of media overhyping early disclosures ("There's an iOS 0day but you'll need to wait 90 days to be protected!!111"), ZDI has had a similar policy for a while now and it's been fine.
While most vendors ship timely patches for vulnerabilities reported by Project Zero, they don’t always reach users. Today, we’re announcing Reporting Transparency, a new policy to encourage downstream fixes.
0
0
1
Check out @merav_br's great in-depth writeup on TraderTraitor's tradecraft (traitcraft?) and history of operations:.
🚨 TraderTraitor: North Korea's cyber "traitor" inside the crypto world. This hacking crew hijacks dev workflows, poisons open-source, and compromises cloud environments — all to steal billions in crypto. Here's how they do it 🧵
0
2
5
RT @cloudvillage_dc: ⚡️Excited to have @AminovDanielle & Yaara Shrike at Cloud Village @DEFCON 33 presenting:.“Auths Gone Wild: When ‘Authe….
0
5
0
RT @wiz_io: 🚨 Research update: #ToolShell is back, and it just leveled up. Two new vulnerabilities in Microsoft SharePoint Server, CVE-202….
0
5
0
RT @nirohfeld: We found a new container escape affecting all container runtimes using @NVIDIA GPUs. The crazy part?.The exploit is just th….
0
133
0
RT @wiz_io: 💡 Eden hosts @sherrod_im, @IssaUrbanGirl & @41thexplorer . Cloud chaos, career confessions & the future of cybersecurity. This….
0
4
0
RT @sweetdelightss: I love when people share their screen. You instantly have all my attention. How many tabs are open?.What’s the icon si….
0
6
0
RT @wiz_io: 🚨 New vulnerabilities in #NetScaler (incl. a 0-day) are now exploited in the wild. 2 enable admin access via session theft. 3.5….
wiz.io
Detect and mitigate CVE-2025-5349, CVE-2025-5777, and CVE-2025-6543, Citrix Netscaler ADC and Gateway vulnerabilities being exploited in the wild. Organizations should patch urgently.
0
6
0
RT @Horizon3Attack: Indicators of Compromise:.🔹 Depending on logging configurations, log entries in ns.log with non-printable characters ar….
0
3
0
RT @wiz_io: 🚨 Wiz spotted a JDWP RCE attack deploying a stealthy cryptominer within hours. Custom XMRig, no CLI flags, deep persistence. D….
wiz.io
Understanding the risks and impact of deploying dev-mode in production environments.
0
1
0
RT @AwsSecDigest: Tracking Cloud-Fluent Threat Actors – Part Two: Behavioral Cloud IOCs.By Merav Bar & Gili Tikochinski. Sophisticated atta….
0
3
0
RT @nirohfeld: Something I’m incredibly proud of is finally live. We've launched the Cloud Security Championship: a 12-month series of dee….
cloudsecuritychampionship.com
Join our monthly cloud security CTF challenge, built by top Wiz researchers. Solve real-world scenarios and rise to the top of the leaderboard.
0
11
0
RT @wiz_io: 🎙️ New drop: @DavidJBianco joins Crying Out Cloud to talk threat hunting, the Pyramid of Pain, and more. Don't miss this cyb….
0
1
0
Check out @AminovDanielle and @GiliTikochinki's recent talk at @DistrictCon about exploitation in the wild of application misconfigurations - this category of risk is well known to threat actors but often ignored by defenders:
0
4
12