Alex Weinert
@Alex_T_Weinert
Followers
5K
Following
2K
Media
79
Statuses
2K
VP Director of Identity Security at Microsoft. he/him.
Washington, USA
Joined February 2016
Brilliant training on a critical feature
A great and comprehensive video from John Savill about @AzureAD Auth Strength! He will show step-by-step how to use this excellent feature to enforce the right level of MFA. Our customers will love this video as they evaluate the deployment plan! https://t.co/3zDKIKv9yv
0
1
8
How cool is this?!
If you have started to use authentication strength in your conditional access policies, I wrote a #KQL query that will calculate the MFA posture for all your apps; authentication strength vs MFA vs single factor - https://t.co/oSqiKVvO9p
0
2
9
New EvilProxy Threat analytics report in M365D. EvilProxy is an adversary-in-the-middle (AiTM) phishing kit available as a new phishing-as-a-service (PhaaS). Microsoft released a new Threat analytic report in #M365D portal with the name; AiTM proliferation through EvilProxy
0
16
26
You can now search your #MicrosoftAuthenticator accounts on BOTH iOS and Android!! 🔔🎉 iOS rollout is in progress if you haven’t gotten it already!
4
19
55
When you do BYOD but need phish resistant auth - CBA on your unmanaged mobile devices:
techcommunity.microsoft.com
Announcing the public preview of Azure AD CBA on iOS and Android devices using certificates on hardware security key
2
9
30
Multifactor Authentication is one of the best ways to help protect against cyberattacks, but "MFA fatigue" is real. @CISAgov shares helpful guidance to implement phishing-resistant MFA including how to use Microsoft Authenticator.
0
62
151
Why is MFA over SMS/Voice not considered safe vs other MFA methods like TOTP & Authenticator apps? I'll break down a blog post by Microsoft's VP of Identity Security @Alex_T_Weinert on why he considers SMS to be the least secure of MFA methods. 👇
9
95
386
Don’t miss key a key update again – we’re automatically enabling critical security features to adapt to ever-changing threat vectors. See the new Microsoft Authenticator features now generally available! #MultifactorAuthentication #Passwordless
User context, number matching, and more are GA in the Authenticator - fight (MFA) fatigue, turn on the features now!
1
14
18
Simpler, more powerful Conditional Access policies using application tags:
2
14
50
Two great tastes that taste great together - Azure AD and Defender!
0
0
4
Huge congrats to the team on this one - end to end Identity Protection on prem to cloud, integrated into the Identity stack and for multi-pillar hunting - YES PLEASE! https://t.co/5ljFzbRAja
@ravivtamir @idanplotnik @sarahhandler dream team!
techcommunity.microsoft.com
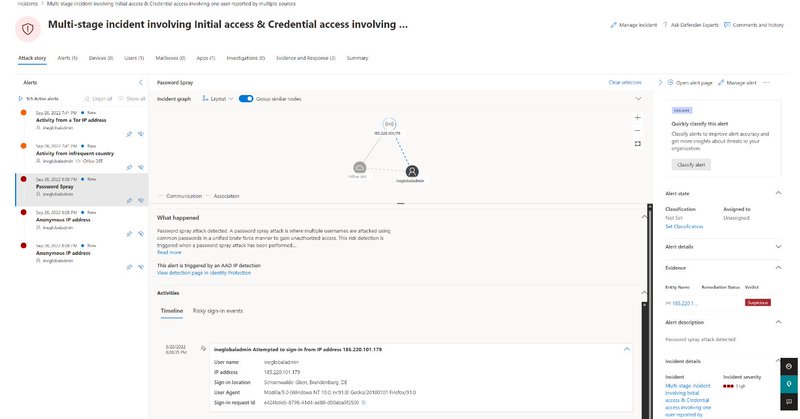
Identity Protection alerts are now part of incidents along with alerts from the other security domains and can be reviewed directly in Microsoft 365 Defender...
0
3
17
User context, number matching, and more are GA in the Authenticator - fight (MFA) fatigue, turn on the features now!
techcommunity.microsoft.com
Number Matching and Rich Context now generally available with new Admin UX and APIs for a more secure authentication experience
0
15
49
Did you know that CA policies now provide granular control over the types of external users you want to apply the policy to? External users are categorized based on how they authenticate (internally or externally) and their relationship to your org (guest or member).
6
75
240
A good time to evaluate latest capabilities in #AzureAD #ConditionalAccess to improve your security baseline for privileged access: 💪 Authentication Strength to require WHfB/FIDO2 💻 Device Filters to enforce using secure admin devices 🏬 Policies for service providers (CSP)
4
16
96