M Abbas M
@AbbasM
Followers
285
Following
71
Media
88
Statuses
25K
AI Strategy & Digital Innovation Leader | Transforming Businesses with Technology
Texas, USA
Joined November 2008
Ready to level up your agile journey?. Join the Agile Practitioners Association (APA) and unlock exclusive Member-Only Benefits:. 🔹 Access to the Neo Smart Ai Agile Advisor for personalized, AI-powered agile guidance.🔹 Connect with a thriving community of Ai agile experts.🔹
0
0
0
RT @AI_SmartHub: ✨ Today’s Highlights:.• OpenAI’s Voice Mode now feels more human — rolling out to more GPT-4o users. • xAI’s Grok is offic….
0
1
0
This Sunday, remind yourself: You’re not starting over. You’re starting better. Every lesson, every setback, every win — it all adds up. Next week is yours. Go claim it. ✨. #SundayMotivation #LevelUp
0
0
0
RT @iSecurity: The hacktivist group Head Mare has leveraged a vulnerability in WinRAR to infiltrate and encrypt systems running on Windows….
cybersecuritynews.com
Head Mare has leveraged a vulnerability in WinRAR to infiltrate and encrypt systems running on Windows and Linux.
0
1
0
RT @iSecurity: The Asian country’s law enforcement suspects the instant messaging app of abetting deepfake sex crimes .
infosecurity-magazine.com
The Asian country’s law enforcement suspects the instant messaging app of abetting deepfake sex crimes
0
1
0
RT @iSecurity: Hackers abuse Google Sheets to covertly store and transmit stolen data or execute malicious scripts, taking advantage of its….
cybersecuritynews.com
Hackers abuse Google Sheets to covertly store and transmit stolen data or execute malicious scripts, taking advantage of its trusted platform
0
1
0
RT @iSecurity: DeadXInject, the group behind AresLoader and AiDLocker ransomware, is offering a new Malware-as-a-Service (MaaS) called Mant….
cybersecuritynews.com
DeadXInject, the group behind AresLoader and AiDLocker ransomware, is offering a new Malware-as-a-Service (MaaS) called ManticoraLoader.
0
1
0
RT @iSecurity: The US FTC has proposed a $2.95m fine for security camera firm Verkada for alleged security failings that allowed hackers to….
infosecurity-magazine.com
The US FTC has proposed a $2.95m fine for security camera firm Verkada for alleged security failings that allowed hackers to access customers' video footage
0
1
0
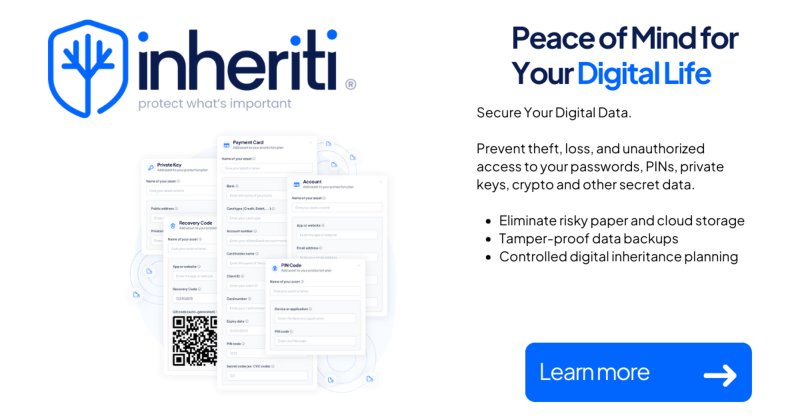
RT @iSecurity: The company’s new product covers every base for digital legacies, resulting in the industry’s first truly comprehensive prod….
cybersecuritynews.com
SafeTech Labs, a company specializing in pioneering blockchain development and technology, announced today that its releasing Inheriti® 2.0.
0
1
0
RT @iSecurity: A new attack vector has emerged, exploiting the critical vulnerability CVE-2023-22527 in Atlassian Confluence. This vulnerab….
cybersecuritynews.com
The vulnerability affecting the Confluence Data Center and Server products has been weaponized using the Godzilla backdoor Exploited.
0
1
0
RT @iSecurity: Cybersecurity researchers at Microsoft recently discovered that Peach Sandstorm, a state-sponsored threat actor affiliated w….
cybersecuritynews.com
The reasons for attacking satellite devices by the threat actors are their vital importance for modern facilities, that is military and global
0
1
0
RT @iSecurity: Truesec claims new Cicada3301 ransomware-as-a-service group could have ties to ALPHV/BlackCat and Brutus .
infosecurity-magazine.com
Truesec claims new Cicada3301 ransomware-as-a-service group could have ties to ALPHV/BlackCat and Brutus
0
1
0
RT @iSecurity: Phishing remains a persistent danger. It’s an email-based cyber threat through which threat actors target sensitive user cre….
cybersecuritynews.com
Phishing remains a persistent danger, as it's an email-based cyber threat through which threat actors target sensitive user credentials and
0
1
0
RT @iSecurity: Proofpoint has uncovered a new cyber-espionage campaign deploying new malware dubbed “Voldemort” #Cy….
infosecurity-magazine.com
Proofpoint has uncovered a new cyber-espionage campaign deploying new malware dubbed “Voldemort”
0
1
0
RT @iSecurity: The Latrodectus malware has been observed to have enhanced capabilities and sophisticated evasion techniques. Initially disc….
cybersecuritynews.com
Latrodectus, a downloader malware, became a subject of interest due to its code and infrastructure similarities with IcedI
0
1
0
RT @iSecurity: Hackers often target NPM packages to inject malicious code into widely used libraries, enabling them to reach a massive deve….
cybersecuritynews.com
NPM packages are often targeted by hackers to inject malicious code into widely used libraries, as this enables hackers to reach a massive
0
1
0