securityledger
@securityledger
Followers
4K
Following
615
Media
2K
Statuses
14K
Independent cybersecurity news and opinion since 2012. Open DMs. Subscribe: https://t.co/O6X7j42QCr | Mastodon https://t.co/xzHMxoMJKF
Boston, MA
Joined August 2012
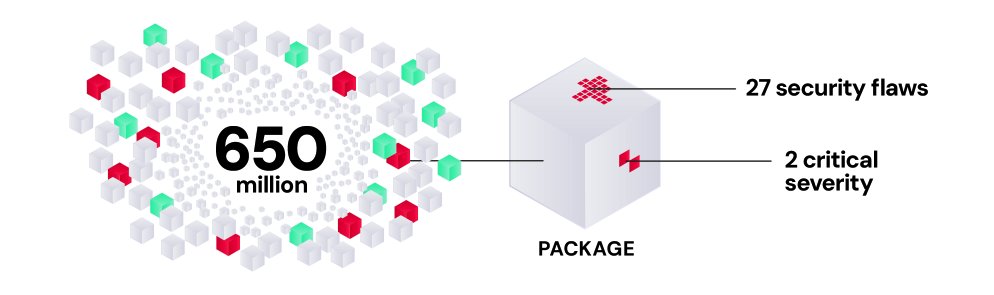
Report: Epidemic of Flaws in Commercial and Open Source Code Fuels Attacks @ReversingLabs #OSS #softwaresupplychain #cybersecurity #appsec #report via @securityledger
0
2
3
In this clip from our latest podcast, host @paulfroberts .asks David Kellerman, Field #CTO @Cymulateltd about security tool overload and the need for optimization. Check out the full interview here: #podcast #sponsored
0
1
0
Researcher @samwcyo and others found a flaw in a @Kia_Worldwide website giving hackers access to the vehicle's location & driver data, remote start, locking, horn, etc. with just a license plate number! #InternetOfThings
0
1
0
At #RSAC2024 ? Check Bricked and Abandoned tomorrow (TUE 5/7) at 9:00 AM. EIC @paulfroberts talks with @allanfriedman of @CISACyber, @tarah, @WeldPond, @window and @MalwareJake on the security implications of OEM #EOL decisions.
1
2
1
Check out our latest Spotlight #Podcast with Jim Broome, President and #CTO at @Direct_Defense. Jim and host @paulfroberts chat about D2's latest Security Operations Threat Report and changes in the threat landscape driven by the use of #AI.
0
1
1
And – as with food safety – we all will benefit in the end. 🙏 #cybersecurity #DevSecOps #software #supplychain #opinion.
0
1
0
out to investigate the circumstances that led to the mass release of flaws like #CVE #202320198, and #202320273 to the public. Arm those inspectors and oversight agencies with new laws and regulations, and they might even hold software makers accountable for their mistakes. .
1
0
0