KoifSec
@KoifSec
Followers
72
Following
65
Media
14
Statuses
70
Security research/detection, also writing for https://t.co/8C74RVZYox. Base64 Enjoyer. Clippy is a threat actor. BSKY https://t.co/JoPhPt9VcN
Joined December 2021
New post out! this time something a bit different :) "Invoke-Shadow” — Applying Jungian Psychology to Detection Engineering. As always big thanks to @ateixei for sharing my articles on the fantastic publication of
detect.fyi
“Until you make the unconscious conscious, it will direct your life — and you will call it fate.” — Carl Jung
0
2
11
RT @Wietze: As June comes to an end, so does #HuntingTipOfTheDay. I hope you enjoyed them! . 👉 Find all threat hunting tips here: https://t….
0
6
0
Hello! I will be running an interactive workshop as part of my company's "2025 State of Detection" webinar on June 17th 9am PST/12pm EST primarily focused about immutable artifacts and detection pitfalls. Sign up here:
cardinalops.com
Download this webinar to explore findings from the 2025 State of SIEM Detection Risk Report and learn how to implement best practices aligned to the report’s key takeaways. In this recording, Dr....
0
0
0
RT @nas_bench: New Sigma release r2025-05-21 is available for download. 🌟15 New Rules.🛡️47 Rule updates.🔬13 Rule Fixes. Explore the full r….
0
21
0
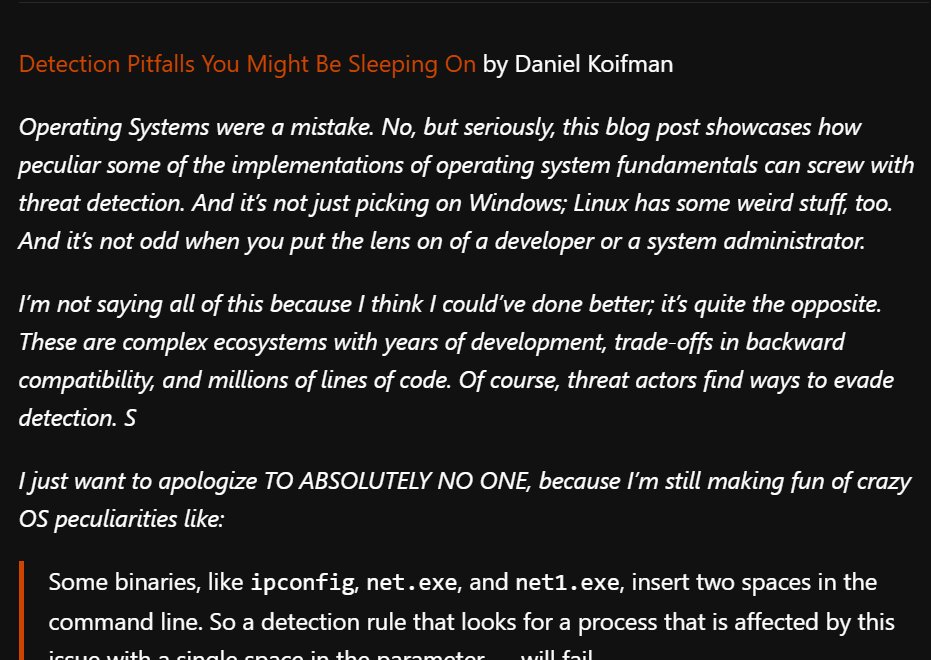
New post out! "Detection Pitfalls You Might Be Sleeping On".
detect.fyi
Detection engineering isn’t just about finding bad behavior. It’s about understanding how attackers appear normal — on accident or by…
0
0
0
RT @CardinalOps: Looking to sharpen your detections? Anchor them on immutable artifacts:. 🎯 Detect intent, not syntax.🗺️ Map to behavior, n….
cardinalops.com
In detection, immutable artifacts are the unchangeable traces of attacker activity, no matter the tool, technique, or obfuscation.
0
1
0
RT @CardinalOps: What’s the most powerful threat detection tool in Google SecOps SIEM? If you ask @KoifSec it's the ability to create metri….
cardinalops.com
Learn how to create metrics in Google SecOps SIEM, with an overview of YARA-L function parameters and two examples: monitoring network bytes and first-seen logins.
0
1
0
Check out my new article on ->
detect.fyi
If a log falls in the SIEM, does it generate an alert?
0
2
14