Huntress
@HuntressLabs
Followers
37K
Following
4K
Media
2K
Statuses
4K
Managed #cybersecurity without the complexity. EDR, ITDR, SIEM & SAT crafted for under-resourced IT and Security teams.
Maryland, USA
Joined June 2015
On August 29, our SOC ran into a brand-new ransomware variant named Obscura—a Go-based payload with a ransom note that reads more like a manifesto than extortion demand. Read the full breakdown, including IOCs and ransomware internals 👇
A look at a newer ransomware variant that we've seen here at @HuntressLabs Thanks to Harlan Carvey and @LindseyOD123 and awesome analysis by @birchb0y and @RussianPanda9xx of the binary! https://t.co/pRutOq0KYe
0
6
24
We are thrilled to announce that @_JohnHammond will be the keynote speaker at @BSidesNYC on October 18, 2025! We look forward to John sharing his insights.
3
13
76
Turn old photos into videos and see friends and family come to life. Try Grok Imagine, free for a limited time.
732
1K
5K
Obscura ransomware: ⚙️ Go binary 🧠 Domain-aware 🧨 Schedules tasks 🔪 Kills 120+ security procs 🔐 XChaCha20 encryption 📜 Ransom note delivered via base64 string Here’s what we found and why it matters → https://t.co/IaBHrFGe0B
4
30
90
Welcome to the Dark Web. Here's a handy FAQ to get you started... Take a Journey to the Center of The Dark Web with @_JohnHammond & @davekleinatland
https://t.co/gmioJrSafa
0
6
28
This month’s Tradecraft Tuesday dives into the biggest threats shaping 2025. 👀 On the agenda: ✔️ What’s changed since our 2025 Cyber Threat Report ✔️ Tradecraft on the rise ✔️ Emerging threats like vulnerable drivers and IT worker scams Save your spot: https://t.co/v80cZueAbu
0
2
9
🚩 Shady logins: Attackers use sketchy user agents to mimic legitimate browsers or email clients. Red flag detection helps us spot them. Hackers know your people are the easiest way in. That’s why identity is one of their favorite attack surfaces.
1
1
6
🚩 Malicious inbox rules: Hackers hide warning emails or auto-forward your sensitive info. We monitor and shut these shady setups down. 🚩 Malicious infrastructure: When IP addresses link back to known attacker hubs, we move fast to kill the session.
1
2
9
Business Email Compromise (BEC) costs enterprises $2.9 billion every year. Here's how threat actors pull it off. 🚩 Unknown VPNs: Logins from untrusted VPNs are a dead giveaway someone is sidestepping your network controls. We flag and stop them.
3
9
58
Persistence = hackers biding their time for the right moment. This recent case started had a rogue RMM disguised as VMware had been lurking for years (before we were even deployed). Even verified VMware was in use before deploying. We can end the long game in real-time.
1
12
72
Full blog has: ✔️ More IOCs ✔️ Full command line breakdowns ✔️ Defender telemetry ✔️ Ransom note excerpts Read:
huntress.com
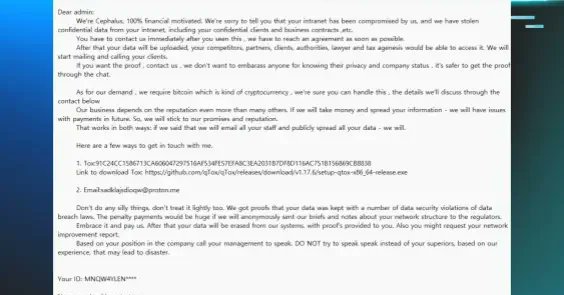
In mid-August, Huntress saw two incidents that linked back to a ransomware variant called Cephalus, which included DLL sideloading via a legitimate SentinelOne executable.
0
2
15
6/ Bonus: “Cephalus” comes from Greek mythology, Cephie wielded a javelin that never missed. The name (and tactics) suggest this crew isn’t here to experiment.
1
1
8
5/ Also this twist: The note included a link to a GoFile repository + password. Victims were encouraged to verify their stolen data. Proof of exfil. Pressure to pay.
1
1
7
4/ The ransom note? It links to dark web articles promoting Cephalus. Threat actor flexing their “credibility” with prior hits. Not your average note.
1
2
8
3/ Then came the obfuscation: ✔️ Shadow copies deleted ✔️ Defender exclusions created ✔️ Defender services disabled ✔️ Scheduled tasks created ✔️ All via PowerShell and Registry edits
1
2
6
2/ 🚨 DLL Sideloading via SentinelOne This attacker used: 🟢 SentinelBrowserNativeHost.exe 🟣 + SentinelAgentCore.dll 🟡 + data.bin (the ransomware payload) Legit tools abused to fly under the radar.
1
2
12
1/ 🔐 Initial Access ➡️ RDP ➡️ No MFA ➡️ Compromised creds ➡️ MEGA cloud storage for exfil Classic double extortion setup—but the ransomware deployment caught our attention.
huntress.com
In mid-August, Huntress saw two incidents that linked back to a ransomware variant called Cephalus, which included DLL sideloading via a legitimate SentinelOne executable.
1
2
10
🧵 Cephalus Ransomware: Don’t Lose Your Head We just ran into a new ransomware variant with a unique attack process Here’s what makes Cephalus different, and why defenders need to pay attention. 👇
3
22
88
Over the past 10 years, attackers have tested us. But every cutting-edge attack pushed our community to double down on wrecking hackers. 💪 As #HuntressTurns10, we’re looking back at the biggest cybersecurity moments that defined the decade: https://t.co/LMYXMK25Qo
1
1
16
Ransomware groups don’t just encrypt files, they steal them first. Data staging + exfiltration is the most common step before encryption. Here's how it happens (with real tactics + command lines):👇 https://t.co/deNqIKsXSM
0
8
38
10 years 🤯 of wrecking hackers. In this month's Product Lab, we're rewinding the highs, the lows & the lessons that shaped us. Plus, a look ahead at the threats the next decade could bring (and what we’re doing to stop them). 👀 Register now: https://t.co/HzsS4qmcCV
0
0
5