DryRunSecurity
@DryRunSecurity
Followers
32
Following
9
Media
22
Statuses
71
We believe there is one thing missing from all tools on the market today: security context for developers. DryRun Security provides that context as you code.
Joined February 2023
Still chasing false positives with regex? 😵💫.Our NLCPs treat code as context, not just text—so you catch real risk, fast. See how AppSec teams are spotting auth gaps, insecure workflows & PII leaks 🔍. 👇 Read the blog. #AppSec #DevSecOps #AI
1
1
3
SAST is stuck. Regex can’t catch AI-generated logic flaws. Join @wickett at #OWASP Austin to see how context-first security changes the game. Live demo + 2025 SAST Accuracy Report .👇for links to the event. #AppSec #SAST #DevSecOps #AI #Cybersecurity
1
0
1
Legacy scanners follow recipes. Probabilism thinks like a chef. 👨🍳. Our latest blog explores probabilistic vs. deterministic SAST—and why rigid rules can’t catch complex, real-world risks. 📖 Read it here: #AppSec #SAST #AI #Cybersecurity #DevSecOps
0
2
5
Legacy SAST + AI = window unit AC ❄️🪟. AI-native SAST = central air 🌬️🔥.One’s clunky. The other’s seamless, efficient, and built in. We didn’t retrofit—DryRun is AI from the ground up. Full blog 👇.#AppSec #SAST #CyberSecurity #AI
0
0
0
New pod drop 🎙️. DryRun CEO, @wickett, joined Oliver Legg of @AspironSearch at RSA to talk blazing-fast SAST accuracy (88% vs ~40% 😳), building DryRun from the ground up, and brisket. TL;DR: Pattern-matching is out. Contextual Security is in. 🔗
0
0
0
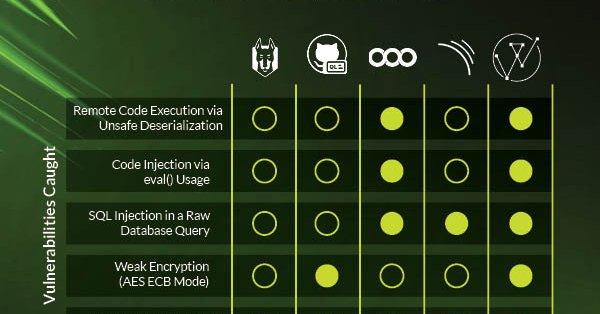
3/3 DryRun Security analyzes code context in real-time, catching risks that others overlook. See the full results of our head-to-head test at
dryrun.security
This is the Python/Django edition! In this post, we use intentionally vulnerable code in Django to compare 5 tools across 5 different vulnerability classes including SQLi, eval() RCE, Broken Access...
0
0
0
3/3 DryRun Security analyzes code context in real-time, catching risks that others overlook. See the full results at
dryrun.security
This is the C# edition of DryRun Security going head-to-head with traditional SAST tools. In this post, we test an intentionally vulnerable ASP.NET Core application to compare 5 tools across 6...
0
0
0
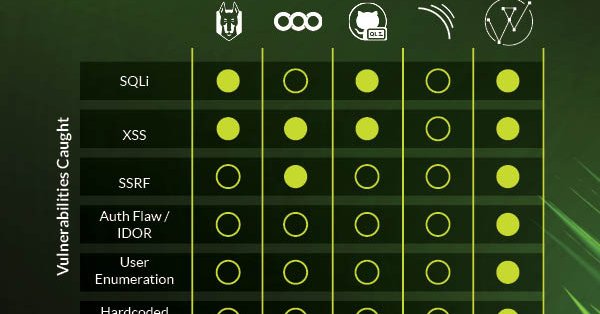
1/3 This is the head-to-head #C# edition! We tested DryRun Security against Snyk, CodeQL, Semgrep, and SonarQube—testing real security flaws like IDOR, SSRF, SQLi, and hardcoded tokens.
1
0
1
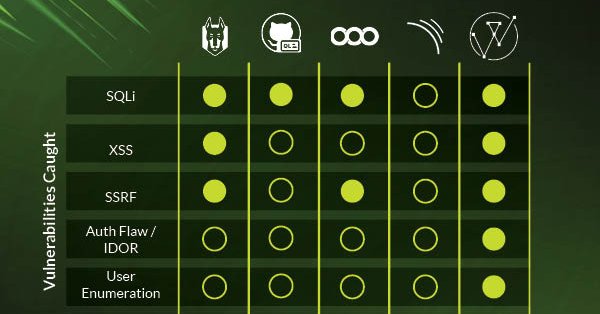
2/2 Legacy tools rely on pattern matching and still miss critical logic flaws. DryRun Security analyzes code context in real-time, catching risks that others overlook. 🔗 See the full results of our head-to-head test at
dryrun.security
See us go head-to-head with some of the best SAST tools on the market today. In this post, we use intentionally vulnerable code in RailsGoat to compare 6 categories across 6 different vulnerability...
0
0
0
🎉We are thrilled to announce to you today, not only our seed round funding, but a new feature we think is going to knock your socks off!.
lnkd.in
This link will take you to a page that’s not on LinkedIn
0
0
3