Being nice pentester 🇯🇴
@BeInsabat
Followers
36
Following
122
Media
13
Statuses
403
ethical hacker, bounty hunter | google cyber security professional | SOC | penetration tester
Joined August 2022
I was today years old when I found out military iPhone's don't come with a camera
658
1K
27K
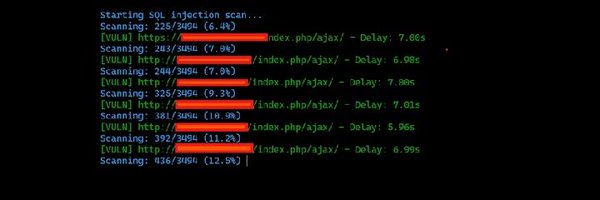
found CVE-2025-55182 in self hosted #bugbounty #program BUT #WAF is blocking my commands can anyone collaborate with me for this
0
0
0
The AI-powered ffuf wrapper by @rez0__ just got a cool update, it now generates contextual wordlists! Instead of just suggesting extensions, ffufai can analyze your target and create custom wordlists for fuzzing. Use --wordlists to enable it, --max-wordlist-size to control the
github.com
AI-powered ffuf wrapper. Contribute to jthack/ffufai development by creating an account on GitHub.
2
72
368
just reported a Bug to self hosted #BugBounty bounty #program join our #whatsapp group for more bug #bounty #updates and insights
0
0
0
Mobile Forensics: Extracting Data from WhatsApp – Hackers Arise
0
9
30
سويت لكم منصة تشرح ثغرات تطبيقات الجوال بطريقة تفاعلية ومعها لابات تطبيقية سهلة وواضحة كل شيء يشتغل محلي وبدون أي ا��صال خارجي: داخل المتصفح وبـ Local Storage وفيها دارك مود بزر واحد، وعربي/إنجليزي بزر واحد لسه ما سوينا شي اي استفسار خاص او تحت التغريده 🩶 https://t.co/K2sjOPKjTO
3
23
285
New Video: Are you still scrolling through JavaScript files manually? I'm sharing my fully automated JS analysis workflow that finds high-impact vulnerabilities JS Recon Automation: Modern Bug Bounty Workflow https://t.co/dziMwckHeh
#BugBounty #JSRecognition #CyberSecurity
1
19
112
Cloudflare hides 19.3% of all websites—but not perfectly. CloudRip scans subdomains to find IPs not behind Cloudflare protection, exposing the real origin server: https://t.co/cRzA62yQ5q
@three_cube
26
216
1K
💡 Quick tip! You don't need an iOS device to obtain an IPA file. Ipatool can easily help you download iOS apps from the App Store for static analysis & vulnerability scanning! 🤠 Check it out! 👇 https://t.co/qzXsocSI9B
7
53
287
Got another bounty from a private bug bounty program join our group for more insight of bug bounty https://t.co/AZ1IsXMfIi
0
0
0
Collection of blog posts, write-ups, papers and tools related to cybersecurity, reverse engineering and exploitation https://t.co/6YgCLKcdUH
#cybersecurity #infosec
1
76
466
A curated list of free courses with certifications.
4
250
3K
Cyber Security from Zero to Expert A Complete Paid Course Free for 24 Hours⏰ This will help you crack your dream role Only for the First 500 People🫣 Retweet & Reply "NEED" to get it for free. [MUST FOLLOW] @tech_crafters so that I can DM you.
692
372
999
JTW Attack & Tools 🧵 1. Check for sensitive data in the JWT Check if any user info or any sensitive info is there in payload section. 2. None algorithm Change "alg:" to none "alg:none" { "alg": "none", "typ": "JWT" } 3. Change algorithm from RS256 to HS256 Get the
2
82
253
🔥Bypass Reset Password Code Lead to Account Takeover https://t.co/sBGQF4uEmK GitHub python script https://t.co/TQpqvDFZJd… credit: @lu3ky13
#bugbountytips #bugbounty
2
20
71
How to build Android Bug Bounty lab Guide to configuring emulators, real devices, proxies, Magisk, Burp, Frida by @yeswehack
https://t.co/f3Iez8PKI0
3
125
682
If you wish to learn more about exploiting JWT vulnerabilities (and how they work), make sure you read our comprehensive article on this topic! 👇 https://t.co/a0G37tsfcp
intigriti.com
Learn how to identify and exploit JSON Web Token (JWT) vulnerabilities using several different testing methods. Read the article now!
0
5
22
Simple way to test for the JWT 'none' algorithm attack: 🤠 1. Base64 decode the JWT header and payload 2. Set the 'alg' header property to 'none' 3. Tamper with the claims, in our example, we want to change the 'role' property to 'owner' and 'organizationId' to the victim's
2
20
151